Facebook Password Reset Scam!
Scam of the Day: Facebook Password Reset Scam
 [space10]
[space10]
The Email:
 Many of the phishing scams you may see in your mailbox are designed to alarm you into clicking, but look genuine enough at a glance so you don’t look that close. In a rush to fix things and at a cursory glance, you just click the links and do as instructed. Today’s phishing example, the Facebook Password Reset Scam does just that. And it’s rather sneaky about it.
Many of the phishing scams you may see in your mailbox are designed to alarm you into clicking, but look genuine enough at a glance so you don’t look that close. In a rush to fix things and at a cursory glance, you just click the links and do as instructed. Today’s phishing example, the Facebook Password Reset Scam does just that. And it’s rather sneaky about it.
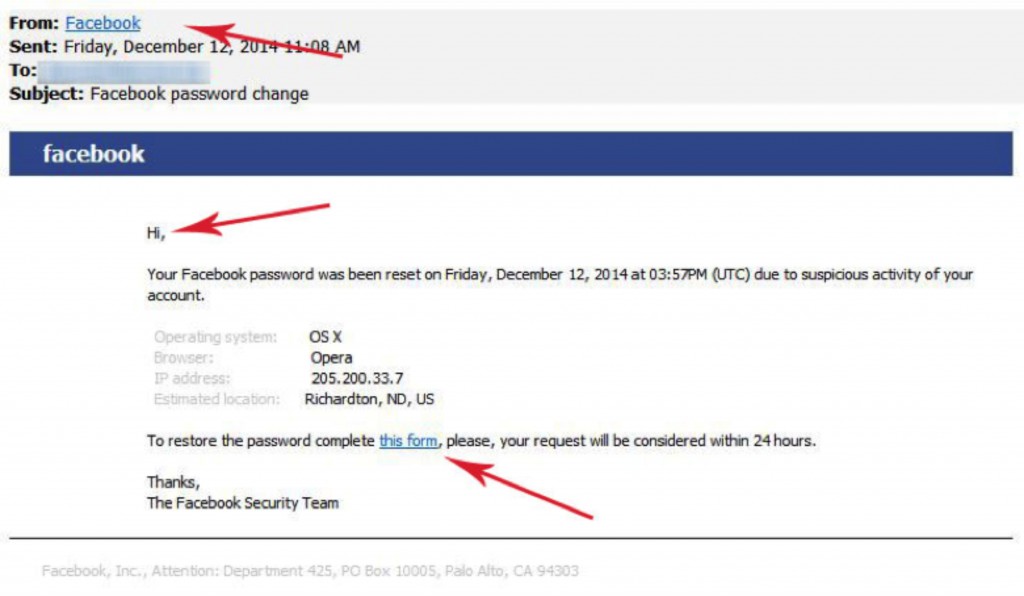
The email in question claims to be from Facebook and the subject simply says “Facebook password change.” Then comes the familiar blue Facebook header and the name.
The message gives cursory information with little detail and instructions you to click on a link and fill out a form in order to restore your password.
The Facebook Reset Scam:
This is a traditional email scam designed to get you to click on the link. The link does not go to Facebook. Instead, clicking either sends you to a form to submit private information, or the link may lead you to a site that will put malware on your computer.
How to Know:
This email is tricky and easy to mistake for the real thing but there are a few details to look for that can tip you off to understanding this is a scam.
1. Hover your mouse over the email link after “From”. In this case it claims to be from Facebook. Hovering over the blue link with your mouse turns up something different: At the bottom of your screen, you see that “@armcandys.co.uk” is the domain from the provided email, not Facebook!
2. Hover your mouse arrow over the other link in the email, “this form”, the one you are instructed to click on to reset your password. Instead of clicking, look again at the provided URL. In this case, we have an entirely different and unknown URL.
3. Often, social media, banks, and other sites that you have an account with will greet you by the name you have signed up through them with. It is uncommon that you will receive a serious piece of correspondence without any indication as to who the email is addressed to.
What To Do:
If you get an email like this and you’re not sure if it’s real or a scam, there are a couple ways to follow up.
1. Do NOT click on the link and follow instructions. Instead, go to your browser, type in the proper URL to the real site and see if you can log in. If you have no problem logging in, then your password has not been reset.
2. Ignore and delete the phishing email.
3. If you would like to follow up on it further, go to the Facebook website and see if they have any information on phishing. They may ask you to send a copy of the scammy email, and give you further instructions on what to do.
Scams of this nature, and phishing emails in general, tend to revolve around surprise and fear, operating under the assumption that the user will click and act without thinking.
We here at Appletree Mediaworks will continue to keep you informed on the nature of these scams so when one of them lands in your mailbox, you are better informed, can stop and think about what you are seeing, and be much better prepared.
[alertbox] Want to know more about email and internet scams? Visit our articles on Paypal Phishing, Domain Slamming, Ransomware, Energy Bill Service Scams, and Court Notice Scams. [/alertbox]
Good Links or Bad Links?
 Are Links Good or Bad?
Are Links Good or Bad?
Are links to and from your website good or bad? To most people this probably seems to be a no-brainer. Of course links are good, that’s what the web is all about, right? Google’s robots crawl the links, it’s how the Web Was Won.
But, Google says that links can be too much of a good thing. For years people have bought and sold links, created link farms, and used other bad tactics to beef up their SEO via links. And then one of Google’s updates hit, and fears spread that links were bad and to be avoided.
What is the truth here?
The truth is likely somewhere in the middle. Practical, useful links to and from other sites are important. But people tend to be afraid of any change Google makes, and take the extreme opposite stance.
Good Practices
- Directory and Citation Listings. Linking to your site from high quality directory listings makes sense because your website is supposed to be a hub for your online company or brand to begin with. It is common sense to send people from directories to your site so that they can have access to as much information as possible.

- Blog Posts. If you are writing for topical, appropriate blogs then it makes sense to link back. Google may penalize for back links that make no sense, but if you are a social media expert doing a guest post on a website blog, one expects a link to additional information. Google is said to have made bad judgment calls here with their penalties, but taking extreme measures does no good either.
- Social Media. Social media has been a nice way to spread information and even today this makes sense. Like directory listings that point to your web as the hub of your brand, social media is an active way to share info and let others pass it along.
Bad Practices
- Link Farms. According to Google, a link farm is “a set of web pages
 created with the sole aim of linking to a target page, in an attempt to improve that page’s search engine ranking.” Paying a company for the sheer purpose of spamming the world with links is a sure way to offend the Google Robots.
created with the sole aim of linking to a target page, in an attempt to improve that page’s search engine ranking.” Paying a company for the sheer purpose of spamming the world with links is a sure way to offend the Google Robots. - Black Hat SEO. From link manipulation, to automated Google queries, to keyword stuffing, Black Hat SEO is generally an attempt to manipulate search engines to rise in ranks, with no concern for human readers. These tendencies tend to be against search engine policies. This is why Google has made SEO more complicated. This is why we can’t have nice things.
Moderation
Google continually changes how its search engine considers things, and trying to follow Google specifications can be maddening. Links, as with any SEO, are better approached when they make sense. Don’t fear using them in a realistic way and at points that make sense, but don’t try to abuse them either. As with many things, moderation is key.
Social Media Content Rights
 Who Owns Rights To Your Social Media Content?
Who Owns Rights To Your Social Media Content?
Occasionally we see those posts on Facebook where a user declares that they don’t have to abide by Facebook’s terms of service, having written a clause in a post. We all know this is a hoax. After all, you already agreed to their terms by making an account.
Even so, what is the nature of your media on someone else’s social media network? What are your social media content rights? It varies, and it’s murky.
Facebook:
 Facebook’s terms are broad. Since their (and your) materials are hosted on various servers, their terms are written so that the data can be shared as desired or needed by them. According to Scoopshot, this does not end when you delete your account either. Your images may be hosted on one of their servers elsewhere.
Facebook’s terms are broad. Since their (and your) materials are hosted on various servers, their terms are written so that the data can be shared as desired or needed by them. According to Scoopshot, this does not end when you delete your account either. Your images may be hosted on one of their servers elsewhere.
Facebook says they have no intention of using these images for their own purposes, selling them, or otherwise distributing them. However, their legal terms are written so that they can.
Read Facebook’s Terms of Service
Don’t like it? Don’t host or post your media there.
Twitter:
 Media you post on Twitter stays yours, says Twitter, but their terms specify that they can distribute the materials posted through them. Again, their terms are open-ended.
Media you post on Twitter stays yours, says Twitter, but their terms specify that they can distribute the materials posted through them. Again, their terms are open-ended.
Twitter’s Terms of Service state “By submitting, posting or displaying Content on or through the Services, you grant us a worldwide, non-exclusive, royalty-free license (with the right to sublicense) to use, copy, reproduce, process, adapt, modify, publish, transmit, display and distribute such Content in any and all media or distribution methods (now known or later developed).”
Instagram:
 Your material belongs to you on Instagram, with the usual warnings about network sharing. They can display those images as they see fit. You are also responsible for not hosting copyright materials belonging to someone else.
Your material belongs to you on Instagram, with the usual warnings about network sharing. They can display those images as they see fit. You are also responsible for not hosting copyright materials belonging to someone else.
The terms of service for Instagram state “you hereby grant to Instagram a non-exclusive, fully paid and royalty-free, transferable, sub-licensable, worldwide license to use the Content that you post on or through the Service, subject to the Service’s Privacy Policy, available here including but not limited to Sections 3 (“Sharing of Your Information”), 4 (“How We Store Your Information”), and 5 (“Your Choices About Your Information”).”
Flickr:
 Flickr is owned by Yahoo, and there has been a lot of fuss over who owns those images. Currently, Flickr claims that you own the rights to your images in their social media network.
Flickr is owned by Yahoo, and there has been a lot of fuss over who owns those images. Currently, Flickr claims that you own the rights to your images in their social media network.
Other social media networks state that you own your media with the usual server/host limitations. They also assume that you are acknowledging that you own the materials you upload.
Ultimately, social media networks are going to cover all their bases for the foreseeable future, and make sure they are covered legally. This generally means they will broadly define their own rights. The result may be that they are allowed rights to your media. Your option, then, is to think carefully about where you are posting your media.
Writing for Your Clients and for Google
Writing for Your Clients and for Google
It’s easy to spot a blog or article written for Google: keywords make no sense, links litter the content, and much of the content seems unoriginal. Yet Search Engine Optimization is as important as it is mysterious. Google is always changing how ranking happens and it can be tricky to keep track of those changes.
Copywriting and SEO go hand in hand. Writing for people is important, and stuffing keywords and links is penalized. Google takes these abuses into account and acts against them. What’s becoming more significant is how often a link is passed along. A large part of modern SEO is getting your website shared on social media; you want to be considered an authority on your topic.
A few things are important to keep in mind, both for clients, readers, and Google.
![]()
[space10]
- Titles that are useful, urgent, and ultra-specific hold attention best.
- Titles that grab readers attention, such as ‘How To’, ‘Reasons Why’ and Testimonials that offer a reward for reading.
![]()
[space10]
- Stay simple, direct, and write in a natural way.
- Keep readers in mind at all times and do not write for search engines.
- Get to the point in the first paragraph.
- Use a call to action and ‘power words’ that grab attention.
![]()
[space10]
- Keep your content relevant and focused on your target audience.
- Stay sway from a bombardment of advertising or selling.
[blockquote]As a business person and website owner, I noticed that selling pools looked hard at my data. I found out that customers were most likely to purchase my product after they had read many pages. Those who contacted me at that point were almost guaranteed to buy.” – John T. Smyth[/blockquote]
![]()
[space10]
- Be the authority and Google will consider you the authority.
- The higher one ranks on a search engine, the more people will visit your site and click that link.
- The more a link is passed around, the more Google considers it significant.
This brings us to what seems to be the comprehensive theme of copywriting and SEO at the moment: Your job is to help the search engine robots figure out the fine details and points of what you are talking about, and what’s good for SEO is ultimately good for people.
EMV Chip and PIN Credit Cards
EMV Chip and PIN Credit Cards
You may be receiving new credit cards this summer: the chip and PIN credit cards.
Credit card terminals must be upgraded to the new technology, common in Europe, by October 1st
or will be held liable for Credit Card fraud that happens in their establishment.
The EMV chip and pin cards reduce credit card data theft by containing a chip that encodes data transferred to the merchant. They are also tougher to clone than
magnetic strips.
Reducing, But Not Eliminating, Data Theft
This technology will not do away entirely with data theft. Online fraud and insecure websites that might store your data are not protected by the chip. For that, you need complicated, hard to guess passwords. And since credit card fraud still happens overseas, the system is not fail-safe.
For businesses and companies, this means it is their responsibility to upgrade credit card terminals for the new technology or they will be held liable for credit card fraud.
Verizon Tracking Cookies Turned Zombie
 Remember those permanent Verizon tracking cookies? They’re causing a stir now that they’re being abused. According to Ars Technica, an advertiser named Turn exploited the Verizon tracking cookies to ‘turn back on’ tracking cookies on its own.
Remember those permanent Verizon tracking cookies? They’re causing a stir now that they’re being abused. According to Ars Technica, an advertiser named Turn exploited the Verizon tracking cookies to ‘turn back on’ tracking cookies on its own.
ProPublica released an article about the Zombie Cookies, which used Verizon’s tracking number to re-spawn tracking cookies that users had deleted. Verizon worked damage control by updating its site terms regarding the tracking cookies.
Later, Verizon stated it would expand its opt-out.
For more information visit:
Staff, Ars. “Verizon Will Now Let Users Kill Previously Indestructible Tracking Code.” Web. 3 Feb. 2015. <http://arstechnica.com/information-technology/2015/02/verizon-will-now-let-users-kill-previously-indestructible-tracking-code/>.
My Computer Files are Being Held for Ransom!
 Ransomware
Ransomware
Ransomware, often going by the specific name CryptoLocker or Cryptowall, is a form of malware that, when installed on your computer, encrypts your files and locks them with a key. It then demands a ransom in digital currency within a set amount of time, or the key will be deleted and the files will be inaccessible.
How do you get it Ransomware?
The most common way to become infected with ransomware is to download it inadvertently. When downloaded, the malware sets to work.
Ransomware is often installed by:
- Opening email attachments
- Clicking on banner ads
Why doesn’t my antivirus protection catch Ransomware?
Generally speaking, Ransomware is sneaky malware that slips in to your computer because you have inadvertently installed it. You’ve gone ahead and told your computer to install things, and the malware takes advantage.
[pullquote cite=”- George W.”]”I got an alarmed call from my grandma. She likes playing online games, and clicked on an ad promising her more coins for her game, and moments later she had a message across her screen telling her that her computer had been infected, and that she had to call a number and pay to get the problem resolved. Fortunately, my grandma didn’t have many files on her computer. We wiped the hard drive and reinstalled Windows. But if she’d had important paperwork or photos without any backups, she would have been in a lot of trouble.”[/pullquote][space10]
Who is the biggest target?
This malware can attack anyone, but it causes the most damage to businesses, as they have more valuable data that is not easily replaced. Ransomware is designed to get money by holding your data for ransom.
How do I avoid Ransomware?
Don’t click on things you shouldn’t, or open unexpected files. Functionally we all know this isn’t always the case, however, and sometimes files slip through because they are deceptive.
If you become infected with Ransomware:
- Have secondary backups of important files that are not updated real time, this way, if you need to roll back, you have something unattached that is not infected.
- Unhook your computer from the internet RIGHT AWAY. All files may not have a chance to be encrypted.
[alertbox color=”red” icon=”delete” hide=”0″]
A few companies claim to be able to undo the damage, or have released the keys to unlock encrypted data, but this has not been guaranteed to work in all cases, especially since criminals update the software all the time.
[/alertbox] [space5]
My files are being held for ransom!
If you do find that you have this software, you have two options:
- Pay up and hope the keys they supply you to unlock your data works as indicated. This is risky as it encourages criminals to continue the scam, and since they ARE untrusted people, nothing is guaranteed.
- Wipe computer clean and restore from backup.
Hacking and computer exploits have become more sophisticated and with more businesses online, the risk is real. Precautions and backups are the most surefire way to avoid the worst of damage from hackers, criminals and emergencies when your files are being held for ransom. For more information on internet security, visit our blog at Appletree Mediaworks, LLC.
For more information visit:
– http://www.businessnewsdaily.com/6657-ransomware-cryptolocker-protection.html
– https://www.foolishit.com/cryptoprevent-malware-prevention/
– http://www.welivesecurity.com/2013/12/12/11-things-you-can-do-to-protect-against-ransomware-including-cryptolocker/
– https://blog.malwarebytes.org/intelligence/2013/10/cryptolocker-ransomware-what-you-need-to-know/
How to Make a Website Mobile Ready
Is Your Website Mobile Ready?
According to Pew Research Center, over half of adult Americans own a smartphone – a full 55% of the adult population, and that number is only increasing. This means it has become essential that a person using their phone to search the web can access and easily navigate your website. What makes a website good or bad for the internet? We’ll go over those points, and what you can do to ensure you know how to make a website mobile ready.
First, it can help to find out how many people are accessing your website via mobile devices. The simplest way to do this is take a look at Google Analytics. This tool has the option to see what platform, device, and browser people are using to access your site. Some sites are more likely to be accessed from a phone than others, but most sites have at least some content that people might want to quickly access on-the-go. Try to think about parts of your website that someone might want to access while out on the road. For example, if your business has a physical location, your address and phone number should be prominently displayed on your mobile site.
What are the problems with ordinary sites?
There are a few problems that make navigating a website tricky from a mobile device:
- Too much right-scrolling. Your computer monitor is going to be much wider than any mobile device, and if your website persists in maintaining that wider-than-high aspect ratio, it’s going to force people to scroll right when they expect to be scrolling down.
- Small Text. Phone screens are tiny, and if your text does not scale properly, users are going to have to continually ‘pinch’ their screens to zoom in. This gets tedious when you have to pinch AND side-scroll. That’s work, and people don’t want to work to find your info on a website.
- Images and Videos are not adjusted. It’s important that a user not have to do finger-screen gymnastics to view an image or watch a video.
- Website loads too slow. Phones using data plans are usually considerably slower to load content than a regular computer connected to high speed internet. Additionally, data plans can be limited and capped. Don’t make a user spend precious time and data downloading content that is unnecessary.
- Navigation is difficult. Dropdown menus and lots of small buttons and links might be perfectly fine for a mouse, but generally a person is not going to carry a stylus to click on an itty-bitty link. Be sure a button is big enough to afford even the larger-fingered among us some accuracy.
How make things mobile-friendly
All that said, making sure you have a mobile-friendly website is not the beast of a challenge it may seem like. You have a few options to consider:
- Build a mobile version of your site. Technically, you will have two sites, one optimized for mobile devices, the other for the web. The problem here is that both sites are going to need maintenance and updating, and forgetting the content for your mobile site is going to be potentially worse than an inconvenient site.
- Use a Mobile-Optimized theme. If your site is targeted primarily at mobile users, it may be worth the time to consider designing your website with a mobile device in mind, and then adjust it accordingly for computer-based use later.
- Build an app. Lately everyone has jumped on the app bandwagon, but an app to download on a device may be worth your time to consider if your site does special things or has features that are above and beyond the needs of a website. If your app is just going to be a downloadable reproduction of your website, however, it may not be worth the time and effort.
- Use a responsive design. Appletree Mediaworks’ more recent web designs are responsive, geared both for use on a computer’s web browser and mobile devices concurrently. Responsive sites seamlessly transform themselves to fit whatever device they are being viewed on. Many WordPress themes are designed to be responsive.
Masque Attack
 Masque Attack was a recent vulnerability involving Apple’s mobile operating system that would allow hackers to use web pages, text messages, and emails to trick people into downloading fake apps that disclose personal information.
Masque Attack was a recent vulnerability involving Apple’s mobile operating system that would allow hackers to use web pages, text messages, and emails to trick people into downloading fake apps that disclose personal information.
The concern is that fake apps resembling real apps such as banks or email program could replace genuine apps installed through the App Store, and siphon personal data without user knowledge. Obviously there is a potential for a sneaky vulnerability on any device, but it’s noteworthy for Apple, which many of its users consider more resistant to hacks and problems.
There is no evidence the vulnerability is being used in the US, but the bug affects iOS 7 or later. 95 percent of Apple mobile devices could be vulnerable.
Apple issued a statement about the matter, that it does not know of any customers who were affected by the issue, and to only download apps from trusted sources.
How To Avoid This, whether you use an iPhone, or an Android or Windows device:
- Don’t install apps from third party sources. Only use Apple’s App store (or the appropriate one to your device) or your own organization if it has apps.
- Don’t click ‘install’ from a popup, even if the popup seems legitimate.
- If iOS says “Untrusted App Developer” click on “Don’t Trust” and uninstall the app.
How to Build A Web Presence
Have you noticed that some companies, small or large, seem to have it together when it comes to their web presence? Their website is set up and interactive, their social media is engaging and popular, their presence seems to permeate every corner of the web. From Yellow Pages to Yelp, you know exactly who they are. How do they build a web presence?
The Web Presence and the Website
A basic website is your first step towards establishing a web presence. Your website should be a home-base for all of your web content. It’s what should pop up first in a search for your business. Your website is where people should be able to find all of your content in one focused location.
A website does not need to be overly complex or cluttered with information – in fact, there are benefits to keeping it clean and easy to navigate. Visitors to your site should be able to find out what your business is and how to contact you with minimal effort.
Don’t think you can just build a website and forget it. Websites only thrive in search engine rankings if you are providing valuable content to people and updating it regularly. If you don’t have any knowledge to share, you can set up a “News” page and let people know what your business is up to. This kind of content keeps people engaged and gives them a reason to come back.
The Web Presence and Social Media
It’s hard to avoid social media; along with Facebook and Twitter, G+ is making its way onto the stage, along with dozens of other more specialized forms of social media.
Do you really need all that? Well, it certainly helps. Giving people more possibilities to land on information about your business means they will be more likely to choose your business when the time comes. If you are already making regular updates to your website, consider utilizing a program such as Hootsuite to easily update all of your social media outlets at once with topically similar information.
What social media should you be on? Facebook, Twitter, and G+ are the biggies. Beyond that, if you have lots of images to share, Pinterest or Tumblr might be welcome additions.
The Web Presence and Directory Sites
The goal of directory sites is to make your business available on any site someone might happen upon. Anywhere from Superpages to Bing to Yelp, your company should have a page. Sometimes these pages might already be created and you must claim them to correct and update the existing information. At other times, you will get to set everything up from scratch.
Plenty of for-pay services offer to fill in all directory sites in one fell swoop. There are also sites such as Moz which scans everything for you and presents a nice To Do list on what you still need to fill in. This gives you a little more control over which information gets entered on each individual directory.
While you’re at it, if you have a physical location, be sure to check it out on Google Maps to make sure your info is valid. This information may be tied to your G+ account, so if you’ve already set that up, it might already be accurate.
Final Thoughts
If this all seems a bit much and hard to keep up with, don’t throw your hands up and miss out on potential business. Contact Appletree Mediaworks. We will be more than happy to work with you and help boost your web presence.