Why You Need an SSL Certificate on Your Website
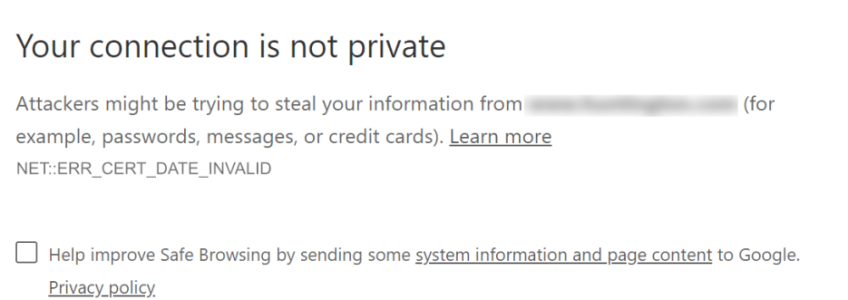
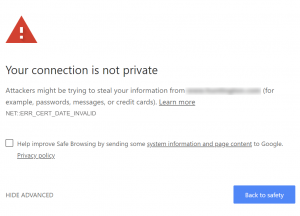 Have you ever visited a website and been greeted by a warning stating that the site is “Not Secure” or something similar? It is definitely off-putting to visitors when this happens. If you are a site owner and notice your site doing this, it is actually pretty easy to fix. All you need to do is install an SSL certificate.
Have you ever visited a website and been greeted by a warning stating that the site is “Not Secure” or something similar? It is definitely off-putting to visitors when this happens. If you are a site owner and notice your site doing this, it is actually pretty easy to fix. All you need to do is install an SSL certificate.
What is SSL?
SSL stands for “secure sockets layer”. This essential technology encrypts data as it moves between a web server and browser. In other words, it stands between you and the rest of the internet, 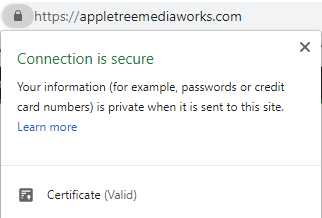 jumbling whatever information you send (such as usernames, passwords, credit card info, etc) into nonsense that can only be decrypted by a special “private key” held by the intended recipient. This protects you from hackers who could otherwise intercept your info while it is in transit. You’ll know you’re on a site with an SSL certificate if you see a padlock to the left of the URL in the address bar.
jumbling whatever information you send (such as usernames, passwords, credit card info, etc) into nonsense that can only be decrypted by a special “private key” held by the intended recipient. This protects you from hackers who could otherwise intercept your info while it is in transit. You’ll know you’re on a site with an SSL certificate if you see a padlock to the left of the URL in the address bar.
What if My Site Doesn’t Collect Personal Information?
Google encourages every site to obtain an SSL certificate. As a reward, your website gets a boost in search ranking. By not having one, you ultimately rank worse regardless of your data collection policy. If you’re running a small business, building a good Google ranking is essential to help bring in customers. This reason alone is good enough to justify the effort – you can outrank your competitors!
In addition to that, not having an SSL certificate causes some browsers to display a warning. Google Chrome, specifically, shows a “Not Secure” label (as mentioned earlier). This can be alarming to potential visitors, redirecting them away before they even land on your site. If enough visitors “bounce” because of this, it can ruin your website’s performance and eventually even harm your company’s credibility!
Keep Your Information Safe
If you manage your website using a content management system like WordPress, your administrative login credentials could become compromised if your site does not have an SSL certificate. Without it, your username and password are sent as plain text over the internet. Credentials sent this way can easily be picked up by hackers. Another way to combat unauthorized logins is by using two-step verification. Enable that whenever it is available.
Stay Cautious
Sometimes even phishing & scam websites are able to obtain legitimate SSL certificates. Just seeing a padlock in the corner does not necessarily mean you should trust the site with your personal information. Usually, you only have to worry about these types of scams coming through your email, so make sure to keep your guard up and know what to look out for.
Now that you know how important SSL certificates can be for you and your customers, help keep your website visitors safe and comfortable by installing one as soon as possible. This will boost your reputation as well as your organic search rankings over time. Not sure how to install SSL yourself? The experts here at Appletree would be happy to assist – we do this all the time! Don’t hesitate to drop us a line and let us know how we can help.
Subscribe to the free Appletree MediaWorks E-Newsletter to get bi-weekly tech tips, scam notices and more, straight to your email!
Windows 7 End of Life Approaches
 The Windows 7 end of life date is quickly approaching. If you’re still behind, you should mark your calendar. Microsoft is ending extended support for this popular OS on January 14, 2020. After this date, they will stop patching security holes. Users who do not upgrade will be exposed to an ever increasing number of online threats. If you are still using Windows 7, what should you do to prepare? Read our simple guide below to find out!
The Windows 7 end of life date is quickly approaching. If you’re still behind, you should mark your calendar. Microsoft is ending extended support for this popular OS on January 14, 2020. After this date, they will stop patching security holes. Users who do not upgrade will be exposed to an ever increasing number of online threats. If you are still using Windows 7, what should you do to prepare? Read our simple guide below to find out!
Keep applying patches – especially now!
Although we always recommend updating your software, it is especially important to apply updates frequently through July of 2019. This is because Microsoft will be changing the way it supplies patches to its users. If updates were not applied leading up to July, Microsoft will stop supplying security updates altogether. This would potentially open your system up to attack a full 6 months before the official sunset date.
Upgrade to Windows 10
Since Windows 7 will no longer be viable after January 14, it is important to upgrade your operating system before that crucial date. Although there are many operating systems to choose from (we recommend Linux if you have the know-how), for most the obvious choice will be Windows 10. This offers the easiest transition since in most cases you do not need to convert any files. Also, your favorite programs will continue working without any interruption. Follow these steps to upgrade from Windows 7 to 10.
- Make sure your device can support Windows 10. The latest version of Windows requires a 1GHz or faster processor, 1GB of RAM, and 32GB of hard drive space. Read the full requirements here and make sure your system or device will work. If not, you may need to upgrade your hardware as well.
- Purchase Windows 10. The free update period expired back in 2016. Although some people have reported that they are still able to upgrade for free, the rest will need to purchase a new Windows 10 product key from microsoft.com.
- Create a full backup. Although this upgrade process is usually seamless, it can sometimes fail and you may lose data. To avoid any problems, it is best to make a full backup of your system so that you can roll back if necessary. Windows 7 comes with a System Image Backup tool to make this process easier.
- Uninstall unnecessary software. Windows 10 will do its best to migrate all of your programs. However, some outdated or uncommon programs may cause problems. To minimize this possibility, we recommend using the Programs & Features tool to remove any software that you no longer need.
- Download and install Windows 10. Finally, download the Windows 10 Disc Image (ISO File) tool. Once downloaded, run the executable and follow the on-screen instructions. When prompted, select “Upgrade this PC now” and later on, be sure to select the “Keep personal files and apps” option. During this process, you will be prompted to enter your Windows 10 product key. Use the key you purchased from microsoft.com.
An Alternative
Not happy with Windows 10? Is your device a little too old to handle the latest system requirements from Microsoft? Fortunately, Linux still runs on most anything and is available for free. There may be a bit of a learning curve, but popular distributions such as Ubuntu have made it much more user-friendly over the years.
If you decide to install Linux, be sure and make a full backup of all your essential files and documents on a thumb drive or external disc before making the jump. Remember that most Windows programs do not work natively in Linux, although there are workarounds and Linux versions available for some of them. Overall, prepare to re-learn some tasks and to spend time searching for alternative programs. This option is for moderate-to-advanced users who aren’t trying to do anything essential or time sensitive during the transition.
Can’t upgrade it? Recycle it!
If all this seems a little daunting, you may be better off just buying a new system with a more recent operating system already installed. In today’s market, low- to mid-level desktops are very affordable, especially when you subtract the cost of a Windows 10 license. If you go this route, a simple thumb drive can be used to transfer files and documents from your old system to the new.
Once all of your documents have been transferred, read our guide on recycling to learn how you can safely recycle your old system without compromising on security. Remember that old systems and devices contain batteries (whether you can see them or not), so it is important to discard them properly so they don’t leak toxic chemicals into the water supply.
Why Labor Unions Need Member Data Systems
Many large organizations – specifically labor unions – struggle trying to keep their member data updated and accessible. Without a centralized database, the most up-to-date vital pieces of information often find their way into a collection of personal spreadsheets and sticky notes rather than somewhere useful.
But what makes a centralized database somewhere useful in the first place? Let’s take a closer look at a few of the benefits and let you decide for yourself.
Easily Remain Compliant with Ever-Changing Government Policies
It’s no secret that our government changes the rules – frequently. Labor unions in particular have witnessed Right-To-Work laws changing the way they collect dues in a growing number of states since the 1940s. A centralized database can help to highlight which members live in Right-To-Work states. This then allows leadership to enact separate collection policies depending on each state’s individual requirements.
Audit Trails
Whether you’re selling books or tracking dues payments, a clear and complete audit trail can be a life saver in the case of a government audit, but there are less obvious benefits as well. Not only can member systems track financial information, but also any changes to the member data itself. Need to know when a member’s address changed? An audit trail can provide not only when, but also who – and in some cases why.
Data Integrity
A centralized database means that every member has exactly one record. It becomes much simpler, for example, to update a member’s address if there is only one record to update. Imagine if an organization stored member data in a collection of spreadsheets or locally stored Access databases. It might take hours to locate and update every instance of a member’s address.  Even then, it throws the door wide open for mistakes, causing endless frustration for the unfortunate member who can’t seem to get a bill mailed to the correct address.
Even then, it throws the door wide open for mistakes, causing endless frustration for the unfortunate member who can’t seem to get a bill mailed to the correct address.
The example we’ve seen time and time again is when an employer sends over a spreadsheet of their current union employee data. The local must then go through the spreadsheet and look for edits. Local reps seldom send these edits on to the district or national level. This lack of data integrity creates wasted postage for returned items and an even bigger issue of member disconnect.
Consistent Member Experience
Maintaining an internally accessible member database fosters a much more satisfying experience for members throughout your organization. Union reps can store notes on a member’s account which the next person who assists that individual can see. Members end up feeling far less frustrated when they don’t need to re-explain themselves with every interaction.
Web/Mobile Integration
 Most modern database solutions allow for integration with your website or mobile application. Data gets fed directly into the database where it becomes instantly available to the entire organization. Once set up, member data systems accept updates directly from the web – often from the members themselves.
Most modern database solutions allow for integration with your website or mobile application. Data gets fed directly into the database where it becomes instantly available to the entire organization. Once set up, member data systems accept updates directly from the web – often from the members themselves.
Additionally, union reps can collect and update member information at special events and trade shows this way using nothing more imposing than a tablet. Our company recently did this for a union client at their constitutional convention. Dozens of members discovered that their contact information was out of date with their union. Members simply updated their information on the tablet. Within minutes, their contact information synchronized across to the national, district and local levels.
Easier Training of Office Staff
 With a single data entry and maintenance system, the learning curve for new hires is greatly reduced. The “write this in this notebook”, “make sure you forward this onto”, and “what was that spreadsheet named” headaches go out the window. Just login, update the information and everyone has access to the same updated information.
With a single data entry and maintenance system, the learning curve for new hires is greatly reduced. The “write this in this notebook”, “make sure you forward this onto”, and “what was that spreadsheet named” headaches go out the window. Just login, update the information and everyone has access to the same updated information.
Security
It may seem counterintuitive, but it is actually much more secure to have one centrally located source of information accessible throughout an organization. In the same way it is easier to patch a hole than a net, having one point of failure allows you to build multiple layers of security around it, knowing your members’ data is safely stored within.  In case a breach does occur, damage control can immediately kick into gear since the audit trail and server logs tell us exactly what happened.
In case a breach does occur, damage control can immediately kick into gear since the audit trail and server logs tell us exactly what happened.
Although it may be easy to imagine that centralizing the data and making it accessible (to the right people) online makes it a target, the alternative often falls to far less attractive options. In spreadsheet offices, for example, it is not uncommon practice for sensitive data to end up on laptops. Employees then transport these laptops off premises, and into a world where laptop theft occurs every 53 seconds. Furthermore, when laptops go missing, it’s often difficult or impossible to know what exactly was on it. Organizations can easily lock a staff member’s account out of a central database in case of laptop theft.
Yes, We Need a Member Data System
 If you found yourself nodding your head yes while reading this article, then it likely is time to move forward with a member data system. Appletree MediaWorks is an experienced firm in this field. We offer a flexible member data system product to our union clients. Our employees are union members too, so we understand your organization’s needs. Whether you’re a small local or a national union, Appletree Media is happy to help you get your member data organized with an affordable solution that will grow with your organization.
If you found yourself nodding your head yes while reading this article, then it likely is time to move forward with a member data system. Appletree MediaWorks is an experienced firm in this field. We offer a flexible member data system product to our union clients. Our employees are union members too, so we understand your organization’s needs. Whether you’re a small local or a national union, Appletree Media is happy to help you get your member data organized with an affordable solution that will grow with your organization.
Don’t miss the 2nd article in this series where we discuss systems to integrate with your member data system. These include: member dues, certification tracking and contract management.
Good WordPress Administrator Names
 Good WordPress Administrator Names
Good WordPress Administrator Names
WordPress lets you select your administrator name and by default, historically we have seen ‘admin’ come up as the most often used name. But using ‘admin’ as your username for WordPress is a potential security breach in the making. When hackers try to brute-force their way into a site, the first name they try is the old standby. There are better and more secure choices. Read on, for some options on good WordPress Administrator names.
Do’s:
- Your private email address; pick one you use that will not be placed
prominently on the site. - A memorable phrase; something with a few words that you won’t forget but won’t be apparent to a site visitor.
- A name with numbers or characters; any numbers will help.
- WordPress also permits symbols in its usernames.
Dont’s:
- Keep the default ‘Admin’
- An email address displayed on your site itself
- Your domain name
Wordfence monitors brute-force attacks, and we see ‘admin’ used in hacking attempts more than anything. You don’t have to make your WordPress username as complex as a password, but making it a little more creative and difficult to guess will make your site much more secure.
[alertbox]
For more on safe username and password use, read up on Protecting Your Facebook Passwords, Preventing Your Email From Getting Hacked, Securing Your Social Media, and a Facebook Password Reset Scam. [/alertbox]
Facebook Password Reset Scam!
Scam of the Day: Facebook Password Reset Scam
 [space10]
[space10]
The Email:
 Many of the phishing scams you may see in your mailbox are designed to alarm you into clicking, but look genuine enough at a glance so you don’t look that close. In a rush to fix things and at a cursory glance, you just click the links and do as instructed. Today’s phishing example, the Facebook Password Reset Scam does just that. And it’s rather sneaky about it.
Many of the phishing scams you may see in your mailbox are designed to alarm you into clicking, but look genuine enough at a glance so you don’t look that close. In a rush to fix things and at a cursory glance, you just click the links and do as instructed. Today’s phishing example, the Facebook Password Reset Scam does just that. And it’s rather sneaky about it.
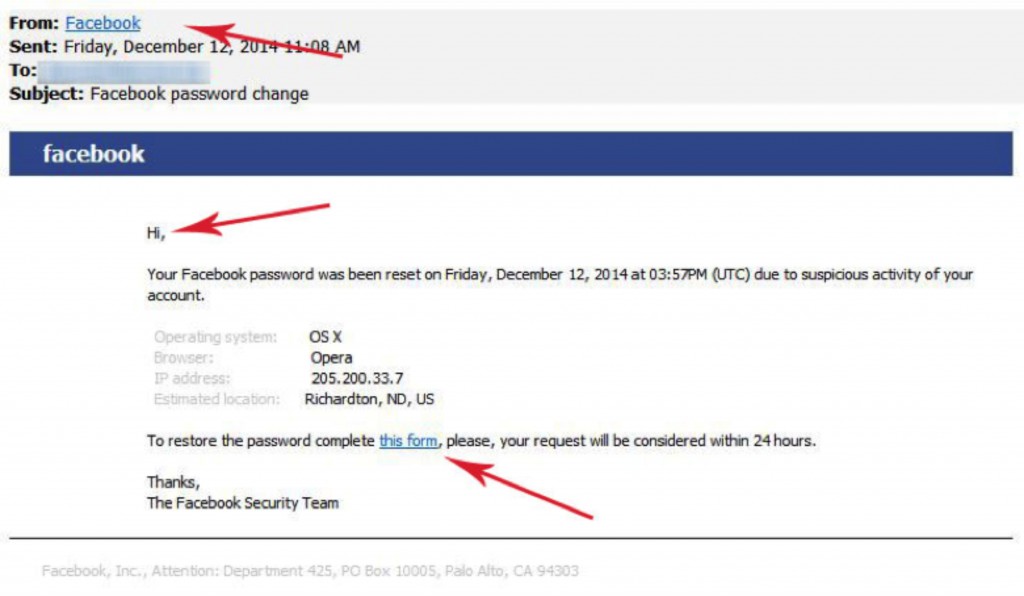
The email in question claims to be from Facebook and the subject simply says “Facebook password change.” Then comes the familiar blue Facebook header and the name.
The message gives cursory information with little detail and instructions you to click on a link and fill out a form in order to restore your password.
The Facebook Reset Scam:
This is a traditional email scam designed to get you to click on the link. The link does not go to Facebook. Instead, clicking either sends you to a form to submit private information, or the link may lead you to a site that will put malware on your computer.
How to Know:
This email is tricky and easy to mistake for the real thing but there are a few details to look for that can tip you off to understanding this is a scam.
1. Hover your mouse over the email link after “From”. In this case it claims to be from Facebook. Hovering over the blue link with your mouse turns up something different: At the bottom of your screen, you see that “@armcandys.co.uk” is the domain from the provided email, not Facebook!
2. Hover your mouse arrow over the other link in the email, “this form”, the one you are instructed to click on to reset your password. Instead of clicking, look again at the provided URL. In this case, we have an entirely different and unknown URL.
3. Often, social media, banks, and other sites that you have an account with will greet you by the name you have signed up through them with. It is uncommon that you will receive a serious piece of correspondence without any indication as to who the email is addressed to.
What To Do:
If you get an email like this and you’re not sure if it’s real or a scam, there are a couple ways to follow up.
1. Do NOT click on the link and follow instructions. Instead, go to your browser, type in the proper URL to the real site and see if you can log in. If you have no problem logging in, then your password has not been reset.
2. Ignore and delete the phishing email.
3. If you would like to follow up on it further, go to the Facebook website and see if they have any information on phishing. They may ask you to send a copy of the scammy email, and give you further instructions on what to do.
Scams of this nature, and phishing emails in general, tend to revolve around surprise and fear, operating under the assumption that the user will click and act without thinking.
We here at Appletree Mediaworks will continue to keep you informed on the nature of these scams so when one of them lands in your mailbox, you are better informed, can stop and think about what you are seeing, and be much better prepared.
[alertbox] Want to know more about email and internet scams? Visit our articles on Paypal Phishing, Domain Slamming, Ransomware, Energy Bill Service Scams, and Court Notice Scams. [/alertbox]
EMV Chip and PIN Credit Cards
EMV Chip and PIN Credit Cards
You may be receiving new credit cards this summer: the chip and PIN credit cards.
Credit card terminals must be upgraded to the new technology, common in Europe, by October 1st
or will be held liable for Credit Card fraud that happens in their establishment.
The EMV chip and pin cards reduce credit card data theft by containing a chip that encodes data transferred to the merchant. They are also tougher to clone than
magnetic strips.
Reducing, But Not Eliminating, Data Theft
This technology will not do away entirely with data theft. Online fraud and insecure websites that might store your data are not protected by the chip. For that, you need complicated, hard to guess passwords. And since credit card fraud still happens overseas, the system is not fail-safe.
For businesses and companies, this means it is their responsibility to upgrade credit card terminals for the new technology or they will be held liable for credit card fraud.
My Computer Files are Being Held for Ransom!
 Ransomware
Ransomware
Ransomware, often going by the specific name CryptoLocker or Cryptowall, is a form of malware that, when installed on your computer, encrypts your files and locks them with a key. It then demands a ransom in digital currency within a set amount of time, or the key will be deleted and the files will be inaccessible.
How do you get it Ransomware?
The most common way to become infected with ransomware is to download it inadvertently. When downloaded, the malware sets to work.
Ransomware is often installed by:
- Opening email attachments
- Clicking on banner ads
Why doesn’t my antivirus protection catch Ransomware?
Generally speaking, Ransomware is sneaky malware that slips in to your computer because you have inadvertently installed it. You’ve gone ahead and told your computer to install things, and the malware takes advantage.
[pullquote cite=”- George W.”]”I got an alarmed call from my grandma. She likes playing online games, and clicked on an ad promising her more coins for her game, and moments later she had a message across her screen telling her that her computer had been infected, and that she had to call a number and pay to get the problem resolved. Fortunately, my grandma didn’t have many files on her computer. We wiped the hard drive and reinstalled Windows. But if she’d had important paperwork or photos without any backups, she would have been in a lot of trouble.”[/pullquote][space10]
Who is the biggest target?
This malware can attack anyone, but it causes the most damage to businesses, as they have more valuable data that is not easily replaced. Ransomware is designed to get money by holding your data for ransom.
How do I avoid Ransomware?
Don’t click on things you shouldn’t, or open unexpected files. Functionally we all know this isn’t always the case, however, and sometimes files slip through because they are deceptive.
If you become infected with Ransomware:
- Have secondary backups of important files that are not updated real time, this way, if you need to roll back, you have something unattached that is not infected.
- Unhook your computer from the internet RIGHT AWAY. All files may not have a chance to be encrypted.
[alertbox color=”red” icon=”delete” hide=”0″]
A few companies claim to be able to undo the damage, or have released the keys to unlock encrypted data, but this has not been guaranteed to work in all cases, especially since criminals update the software all the time.
[/alertbox] [space5]
My files are being held for ransom!
If you do find that you have this software, you have two options:
- Pay up and hope the keys they supply you to unlock your data works as indicated. This is risky as it encourages criminals to continue the scam, and since they ARE untrusted people, nothing is guaranteed.
- Wipe computer clean and restore from backup.
Hacking and computer exploits have become more sophisticated and with more businesses online, the risk is real. Precautions and backups are the most surefire way to avoid the worst of damage from hackers, criminals and emergencies when your files are being held for ransom. For more information on internet security, visit our blog at Appletree Mediaworks, LLC.
For more information visit:
– http://www.businessnewsdaily.com/6657-ransomware-cryptolocker-protection.html
– https://www.foolishit.com/cryptoprevent-malware-prevention/
– http://www.welivesecurity.com/2013/12/12/11-things-you-can-do-to-protect-against-ransomware-including-cryptolocker/
– https://blog.malwarebytes.org/intelligence/2013/10/cryptolocker-ransomware-what-you-need-to-know/
Masque Attack
 Masque Attack was a recent vulnerability involving Apple’s mobile operating system that would allow hackers to use web pages, text messages, and emails to trick people into downloading fake apps that disclose personal information.
Masque Attack was a recent vulnerability involving Apple’s mobile operating system that would allow hackers to use web pages, text messages, and emails to trick people into downloading fake apps that disclose personal information.
The concern is that fake apps resembling real apps such as banks or email program could replace genuine apps installed through the App Store, and siphon personal data without user knowledge. Obviously there is a potential for a sneaky vulnerability on any device, but it’s noteworthy for Apple, which many of its users consider more resistant to hacks and problems.
There is no evidence the vulnerability is being used in the US, but the bug affects iOS 7 or later. 95 percent of Apple mobile devices could be vulnerable.
Apple issued a statement about the matter, that it does not know of any customers who were affected by the issue, and to only download apps from trusted sources.
How To Avoid This, whether you use an iPhone, or an Android or Windows device:
- Don’t install apps from third party sources. Only use Apple’s App store (or the appropriate one to your device) or your own organization if it has apps.
- Don’t click ‘install’ from a popup, even if the popup seems legitimate.
- If iOS says “Untrusted App Developer” click on “Don’t Trust” and uninstall the app.
The Good and the Bad of Cloud Computing
Cloud Computing
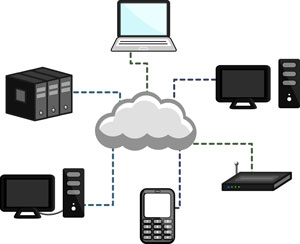
Cloud computing seems inescapable. Phones and devices have cloud servers for files, any user can get free cloud backups for their own computers, and even federal and state governments are investing in cloud computing for their own data. But just what is it, and is it safe?
What Is It?
First, we had computers that had hard drives with information and programs on them, and then we used discs to move that information from computer to the next. These discs were small, so we took to thumb drives, but this was problematic if you forgot your thumb drive at home or work or school. Those of us who had web mail account like Yahoo or Hotmail recognized we could just email ourselves the data, and open it from wherever.
This was the early stage of Cloud Computing.
Cloud computing is the practice of using a network of remote servers hosted on the internet to store and manage data, rather than a local server, or a personal computer. Given that few of us stick to just one computer these days –between home, work, school, laptops, tablets, and other devices – having ready access to that information on any device is important. This is where cloud computing comes in.
Where is it stored?
Cloud computing is named as such because information or even programs are used or run from a number of application or storage servers kept and backed up off site, and accessed through multiple computers where the user logs into an interface for access. A simple example of this is web-based email which is accessible through a web browser and website, but available through any computer.
Individuals and companies often resort to third-party cloud storage, such as iCloud, Dropbox, Google Drive and others. Companies may wish to back up not only files, but whole computers, databases, or programs for use.
When are people going to use this tech?
This sort of technology has been used since the ‘90s when people backed up files on web hosts or used web-based email clients. With the ever increasing use of mobile computing, cloud hosting has become more prevalent and will continue to do so for the foreseeable future.
Why is this needed?
The more mobile people become with their computing, the more important it will be to have access to files, data, and programs remotely. While devices and computers have ever-increasingly large hard drives and can hold more info, hauling around secondary drives and copying information over is redundant and unnecessary.
For companies and industries, a base location for all information is valuable in the interests of saving money and time. Instead of a slowly depreciating server under a desk or stuck in the back room, all information is available and reliably backed up offsite. This also allows for people in multiple locations, branches, or buildings, to have access to and immediately update information as needed.
What are the potential pitfalls and drawbacks?
Cloud computing has some very real drawbacks and concerns, and some of them do not have good solutions at this time:
- Access: To access the cloud (whatever form of cloud you are accessing at the moment), the user needs internet access. Without wifi or otherwise, access to files and software severely limits what can be done. This is becoming less and less a problem as time goes on, but still could come up as an issue.
- Security: Every day the news broadcasts another company or institution getting hacked. And as security gets more sophisticated, hackers always seem one step ahead. Information could be accessed and stolen during a number of points in the cloud computing process, whether it be a hacker discovering a means of getting in, or a user with a weak password.
- Privacy: Housing your data somewhere on the web inevitably means someone else may have access to it. Along with the aforementioned hackers, NSA access to various servers and databases has been argued and discussed extensively throughout the last year. While a company may not have anything to hide, they may not want that data accessible in general.
- Third Party Control: Ultimately, in handing over data and programs to a third party, a company or institution is handing the keys over to someone else. Not everyone likes this or feels comfortable with it, and would prefer to have complete control over their information.
Despite the potential hazards of cloud computing, large companies and even government and official institutions more and more are turning in that direction due to reduced costs and ease of use. The debate and concern over the security of private information will only increase as hackers are more sophisticated and computing becomes more ubiquitous. But cloud computing is not going away any time soon.
For more information on cloud computing and internet security in general, follow the Appletree Media blog.
More On Cloud Computing:
http://computer.howstuffworks.com/cloud-computing/cloud-computing.htm
http://www.moneycrashers.com/cloud-computing-basics/
http://www.thefiscaltimes.com/2014/10/14/States-Turn-Cloud-Computing-Cost-Savings
http://www.whitehouse.gov/sites/default/files/omb/assets/egov_docs/25-point-implementation-plan-to-reform-federal-it.pdf
http://www.itproportal.com/2014/10/13/whitepaper-five-myths-cloud-computing/
Union Edge Tech Tips – October 29, 2014
Verizon’s Cookies and Windows XP Hackers
Verizon’s ‘Perma-Cookie’ Is a Privacy-Killing Machine
Apparently Verizon tracks your internet use and there is no way to opt out of it.
When surfing the internet using Verizon’s internet, a string of about 50 characters is added to the end of every URL you go to. Verizon calls this a Unique Identifier Header (UIDH), its essentially a serial number that advertisers can use to identify you on the web when you use Verizon’s internet service.
According to Verizon spokeswoman Debra Lewis, there’s no way to turn it off. She says that Verizon doesn’t use the UIDH to create customer profiles, and if you opt out of the company’s Relevant Mobile Advertising program by logging into your Verizon account. Then Verizon and its advertising partners won’t be using it to create targeted ads.
Because Verizon is broadcasting this unique identifier to every website, ad networks could start using it to build a profile of your web activity, even if you’ve opted out and without your consent.
There’s rumor that AT&T and T-mobile are doing the same thing to their users. To see what is being captured by Verizon or AT&T, Click Here to check your mobile device.
Full Article Text: WIRED -Verizon’s “Perma-Cookie”
Windows XP Is Still a Favorite Among Hackers
As much as people love Windows XP, there are reasons to upgrade to something newer. Almost 25% of all PCs are still running Windows XP, that’s 1.5 billion computers.
Back in April, Microsoft stopped supporting and updating XP. Leaving XP users open to new exploits. Researchers have found that close to ½ million US computers are hacked, and are botnets that send back information such as passwords and banking information.
This is only going to get worse, if you’re still running XP its time to think about upgrading your Malware software or updating to Windows 7 or soon 9.
Further Reading: MIT Technology Review – Windows XP Is Still A Favorite Among Hackers
Social Media Tips for Unions:
- It can’t hurt to have different social media platforms linked together even if they have similar info. People should be able to get from one platform to website to another platform with relative ease.
- It is a good idea to have the basic info filled out on any given platform because you never know which one people are going to go to first, even if you don’t intend to update regularly.
- Good to consider the following social media platforms:
- Facebook – A given. People use this extensively and refer to it frequently to keep track of current events and information.
- Twitter – Twitter is great for on-the-spot rapid posts and updates of current events as they happen.
- G+ – Set up G+ so people local to the area can find information on a given Local, and the information links up with the map feature. Google might put this information in the sidebar on the search page when someone does a search so that it displays more prominently.
- Pinterest – Pinterest is a great way to spread around images of events and things going on – photos are the way to go with this platform, and if you use them extensively, you’ll want to be sure to post them here.
- Ello – Ello is brand-new and still in beta, but they promise not to sell your information for advertising. It might be the right way to go, and could send the right image.
- Your own Website – Be sure you hook everything to the website and back again. Think of your website and social media platforms as a network that ties together. Better to get the word out when you need to!
Always practice Safe Tech!!
Read More About Crafting Strong Passwords at the Appletree Media Blog.