As technology progresses, we’re finding new ways to do things better. One downside of this is, that also means scammers are finding new ways to do things better. Here is some spam to look out for.
Sextortion Email Scam
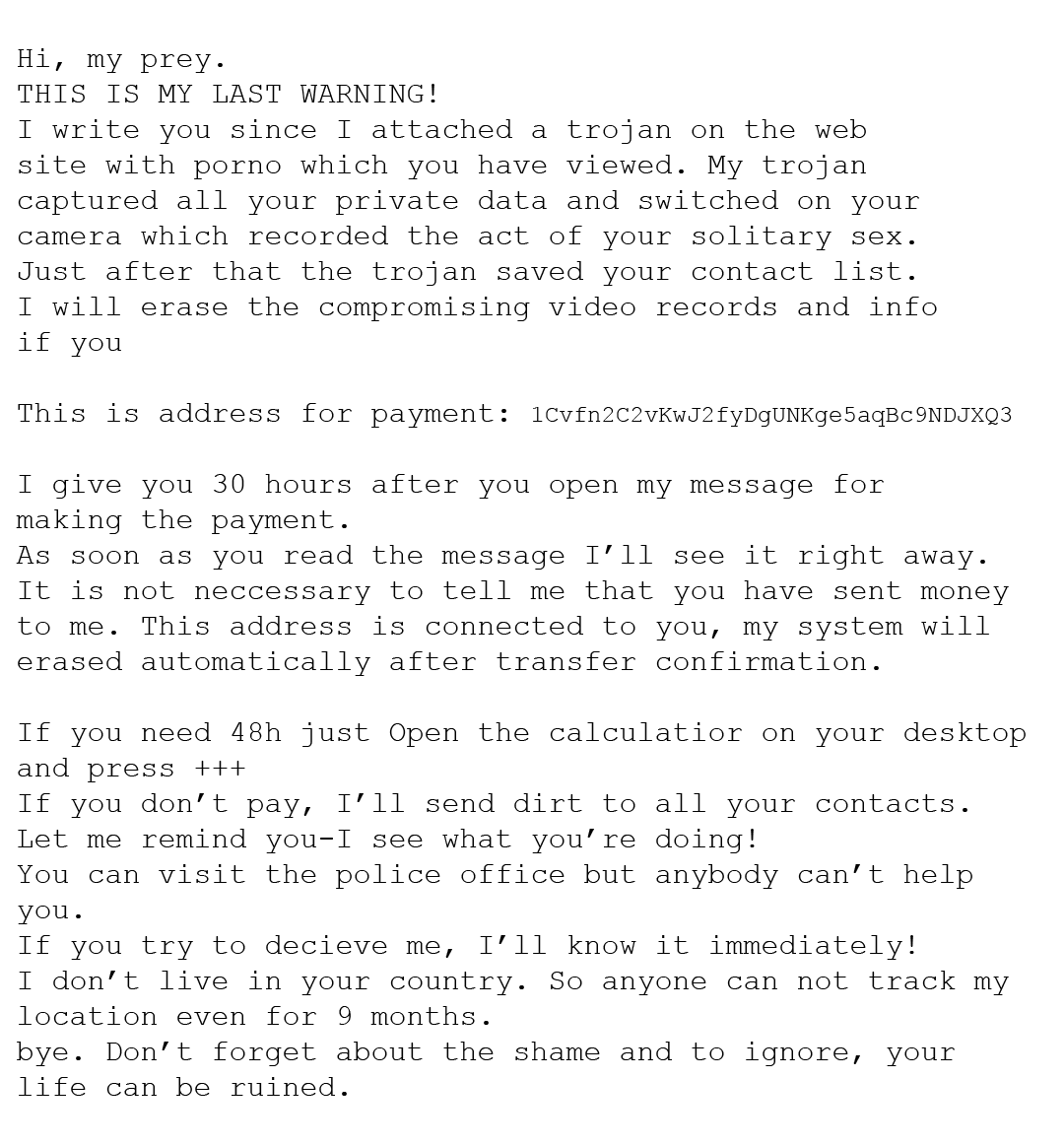
One scam that was popular last year had the scammer proclaiming that an amount of money (usually ranging from $600-$3000) in Bitcoin is enough to destroy video that they supposedly have of you. The scammer sometimes even supplies a password of yours within the email. They then threaten to release webcam video of you viewing pornography to your family, friends, and colleges. At this point, you may be nervous.
Here is an example of this scam:
What should you do?
If you’re still using the password they put in the email, you should certainly change it. Do not respond to scammers ever, just report the email and delete it instead.
Various Phishing Scams
If you haven’t heard of phishing yet, you’re probably at a higher risk of falling for it.
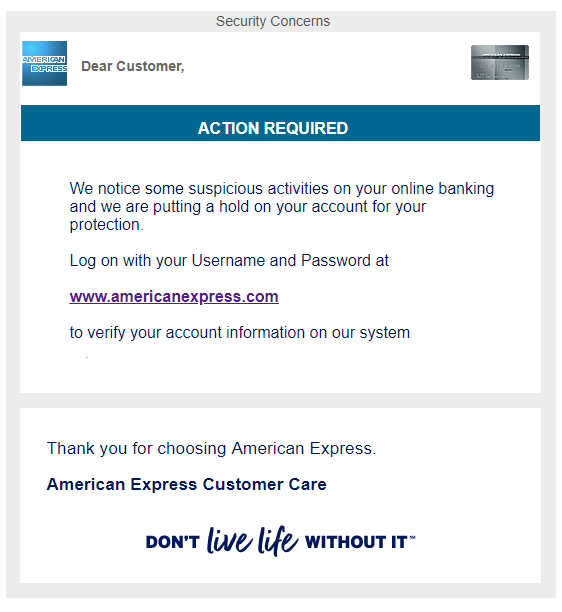
Phishing is a “bait” scam method (hence the relation to “fishing”) where scammers will have an imitation site that strongly resembles the real thing. It takes is a split second for them to get you. From adding a malicious extension to typing in billing information to a “failed transaction” from a fake Amazon, these scammers will pretend to be pretty much anything to get your money from you.
Here is an example of phishing (extremely authentic looking):
What should you do?
If you get an email that contains an external link, don’t click it right away.
– Double check who the sender is. Sometimes this can be a giveaway. Don’t recognize the email? Doesn’t look real? Don’t click the link.
– Use a website like https://www.urlvoid.com/ and paste the link that was provided. It will tell you the destination of the link. If anything..phishy.. comes up, don’t follow through. The link given to you in the email should be the same website as the destination.
– If nothing else, it’s better to be on the safer side. Never provide any information to a link you’re at all suspicious about.
Lottery Scams
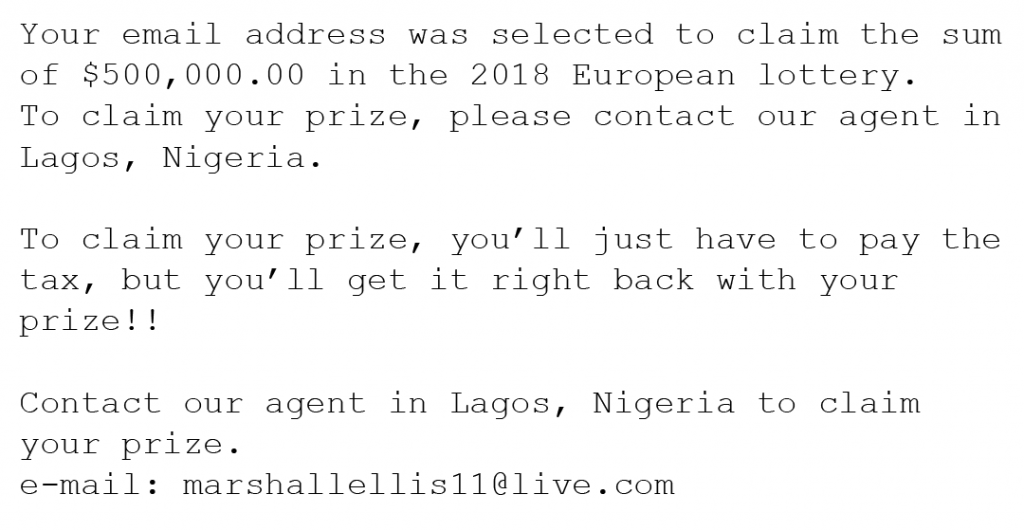
These are emails or texts from a fake lottery company saying that you won a lot of money or very valuable prizes out of nowhere. They will tell you that there are fees and/or taxes that have to be paid before your prize can be released to you.
Here is an example of a lottery scam:
What should you do?
Simply report and delete the email. Remember that you can’t win something you didn’t enter to win.
Hallmark eCard Scam
This scam would be an example of phishing, and it comes and goes pretty frequently. It’s a fake Hallmark email that is extremely real looking. If you click the link within the email to open the supposed eCard sent to you by a “friend”, a virus will launch and install malware onto your computer.
These emails will look just like Hallmark eCards.
What should you do?
Don’t click hyperlinks without knowing the destination. Attempt to verify the eCard on Hallmark’s website directly instead of clicking the link. Report and delete any unauthentic emails.
Hitman Scam
This scam would be terrifying for any victim unfamiliar with how internet scams work. Scammers here give you the option to live or die if you do not pay up. They claim a “friend” of yours gave them a lot of money to end your life, but they are giving you a chance to save it for a price ranging anywhere from $1000-$100,000.
Here is an example of the hitman scam: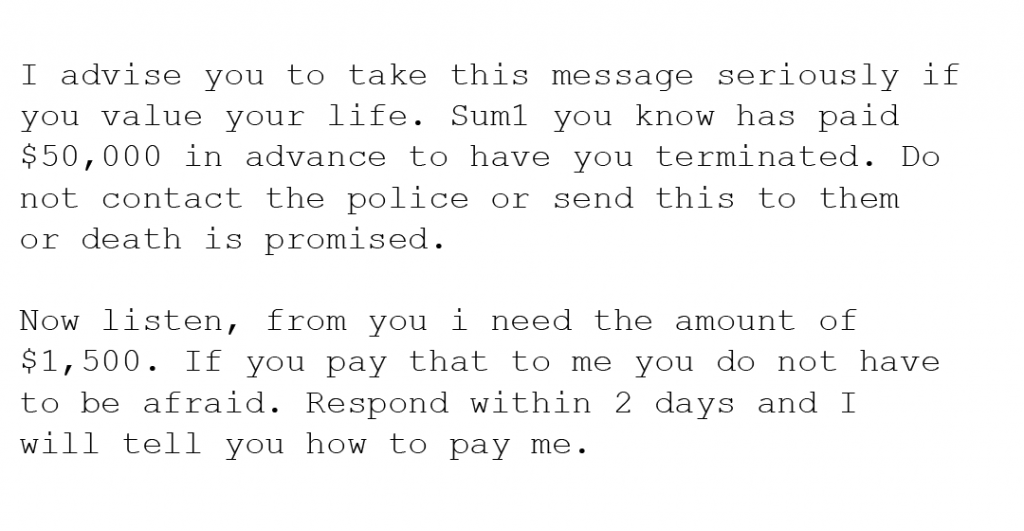
What should you do?
If you notice an email like this in your inbox, delete it without even opening it. Read below to learn where to report scams.
Protection
There are ways to keep yourself protected from scams. The most important thing is to know. Don’t believe everything that comes through your inbox and do your research.
How scammers get your information?
The scammers likely retrieved your email (and possibly an old or current password) from a database of leaked information that was obtained during a breach. To check and see if your email is associated with any data breaches, head to haveibeenpwned. You can type your email in and it will tell you if it’s ever been compromised. Also during which exact breach. Be sure to change your password if you haven’t since the last breach you were involved in.
What to do with spam
If obvious spam ever does come through your inbox, just delete it without opening it. A lot of scam emails contain what is commonly called a “pixel”. This acts as a read receipt. It will tell the scammer that the email was opened. It can also supply them with other information, such as:
- Browser you’re using
- Operating system
- IP Address
- The exact time the email was opened
Thankfully for us, there is a program that can tell us whether or not an email is being tracked. It’s called Ugly Email. It makes an eyeball appear next to the subject of any email that is being tracked. The slight downsides of this are that it’s only for Gmail and is only out for Chrome and Firefox at the moment. If you fall under the criteria, this can be a really useful tool.
Report Scams
You can help eliminate a popular scam by not only reporting it to your email provider, but to the IC3 as well. They are a branch of the FBI that deals with internet crime. Make sure to file a complaint for scams you may get – especially reappearing ones.