Technology for Christmas
 ‘Tis the Season to be Jolly and show how festive technology can be. Technology certainly does not ignore the fact that billions of people are celebrating the Holidays. Christmas cheer is being spread within mobile apps, Websites, and Blogs. Even Christmas decorations are redesigned using technology. Also, Google has done a lot to show their holiday cheer this year. Check out some of the ways you can enjoy all this festive technology for Christmas.
‘Tis the Season to be Jolly and show how festive technology can be. Technology certainly does not ignore the fact that billions of people are celebrating the Holidays. Christmas cheer is being spread within mobile apps, Websites, and Blogs. Even Christmas decorations are redesigned using technology. Also, Google has done a lot to show their holiday cheer this year. Check out some of the ways you can enjoy all this festive technology for Christmas.
Mobile Applications
Did you know that Christmas is also the unofficial Developers App Day?
 According to Flurry, 328 million apps were downloaded on Christmas Day last year in the United States. This is not too surprising though. With mobile devices being one of the most popular gifts to give during the holiday season, it is only natural that people will be downloading apps, often sharing them with friends and family.
According to Flurry, 328 million apps were downloaded on Christmas Day last year in the United States. This is not too surprising though. With mobile devices being one of the most popular gifts to give during the holiday season, it is only natural that people will be downloading apps, often sharing them with friends and family.
App developers work tirelessly leading up to the holiday season. This past September, developers were already hard at work polishing their apps for the Christmas rush. Some developers have even added exclusive seasonal content.
App Icon Festive Dress up
I’m sure you have noticed your mobile apps updating their icons to something festive for the Holidays. This is one way app developers celebrate the season.
Here are some popular apps showing off their holiday spirit with a festive new icon:
 |
 |
 |
 |
 |
 |
Photos from: itunes.apple.com/ and play.google.com/
Top Christmas Apps this Season
A Charlie Brown Christmas
Interactive storybook narrated by Peter Robbins (the original Charlie Brown voice).
NORAD Tracks Santa
Apple and Android Free
Track Santa throughout the world and see what he is doing and how you can help him.
Christmas Story Books
Apple and Android Free
Collections of Christmas stories such as “A Christmas Carol” and “Twas the Night Before Christmas”.
ElfYourself
Android Free with extras to buy
Turn your friends and family into elves and make them dance to a Christmas song.
Talking Santa
Apple and Android Free
Talk to an animated Santa. Tap the screen to make him respond in various ways.
Christmas Radio
Apple Free
Choose from 50 unique Christmas-themed Internet radio stations.
Websites and Blogs
Make your Website Festive
Use WordPress Plugins – Add things easily to your WordPress Site such as Advent Calendars, Countdowns, Holiday Popup Messages, and Christmas animated images to spruce up your website for the holidays.
Don’t have WordPress? Use these ideas to add extra flair to your site with some simple code.
Creating a Landing Page – Create a temporary landing page for your site as just a way to wish happy holidays or to highlight a promotion on your site. Make it easy to to dismiss so your visitors don’t get frustrated trying to bypass it.
Make a Festive Logo – Take your signature Logo and dress it up to make it festive. Use Photoshop, Gimp, or just hand it off to your graphic designer. It does not need to be a big change, just some extra flair your customers will notice.
Don’t Forget Your Social Media – Take all of what you have done and incorporate it into your social media. Change your profile picture to your the festive logo. Change your cover photo to a matching image. Then send out a post telling your followers to check out the changes you made to get more attention and clicks to your website.
Christmas Lighting
Technology Controls Christmas Lights
The new thing is to make a light show on your house with your Christmas Lights. Control when the lights turn on and off and even coordinate it with music. You can do this using computer software or even a smartphone app.
LumenPlay
For the Advanced create a light show using Raspberry Pi
Check out the DIY instructions
How Google Celebrates the Holidays
This year Google has been showing off their holiday spirit with Christmas logos, a Santa Tracker app, and more.
- This holiday season, Google is celebrating with new, festive logos:
 December 24 |
 December 23 |
 Winter Solstice December 22 |
|
- Google is also famous for hiding Easter eggs depending on what you search. To celebrate the holidays they created Easter eggs if you type “Christmas“, “Kwanzaa“, and “Hanukkah“
- Santa Tracker – You can play on your phone or on your desktop. Play Christmas related Games and Learn about Christmas too.
- Google Spotlight Stories Presents: Special Delivery
- A company named Boston Dynamics, with Google X, used their tech skills to create robotic reindeer to pull a sleigh.
Online Shopping Security Tips for the Holidays
 It’s that time of year again when everyone is trying to find the perfect presents for their friends and loved ones. This year’s online sales are sky-rocketing from customers shopping online on days such as Thanksgiving, Black Friday, and Cyber Monday.
It’s that time of year again when everyone is trying to find the perfect presents for their friends and loved ones. This year’s online sales are sky-rocketing from customers shopping online on days such as Thanksgiving, Black Friday, and Cyber Monday.
Customers should consider some of our online shopping security tips before exchanging their personal information and money through the Internet. Learn where to shop online, how to be secure, and best practices to keep yourself safe.
Where to Shop
Use Familiar Sites – Stick to the brands you know like amazon.com, costco.com, or similarly established sites. If you don’t recognize the store you’re shopping at, do some searching around to see if you can find reviews (on a different website) before making a purchase.
 Look for slightly misspelled words in the domain name. Often, hackers will register similar domain names and create a doppelganger site to try and steal credit card information from unsuspecting shoppers.
Look for slightly misspelled words in the domain name. Often, hackers will register similar domain names and create a doppelganger site to try and steal credit card information from unsuspecting shoppers.
Use Mobile Apps – These days, there is not much functional difference between using a mobile device or a desktop computer to shop online. The best practice on a mobile phone is to use a retailer’s app rather than using the phone’s web browser.
- Learn more about safe mobile shopping.
 Be Careful With Email – During the holidays you will probably get several emails promoting holiday deals. This increased traffic can present an opportunity to scammers to send you a nefarious link dressed up in an attractive email. Instead of clicking any links directly from an email, type the store’s URL directly into your browser.
Be Careful With Email – During the holidays you will probably get several emails promoting holiday deals. This increased traffic can present an opportunity to scammers to send you a nefarious link dressed up in an attractive email. Instead of clicking any links directly from an email, type the store’s URL directly into your browser.
Never give out your credit card number via email.
- Learn more about scam emails
How to be Secure
Computer Protection – First and foremost you need to protect your computer in case malware does leak through. You should also make sure your web browser and operating system are up to date. Software updates contain essential security patches.
 Phone antivirus apps
Phone antivirus apps
- Android Antivirus Apps
- iOS Antivirus Apps
Desktop antivirus
Check If It’s Secure – Any site that is taking credit card information should have SSL (secure sockets layer) encryption installed. To be sure your connection is encrypted using SSL, take a look at the URL in your browser.
A secure page will start with HTTPS:// instead of HTTP://
Typically, there will be an icon of a locked padlock either In the status bar (at the bottom of your web browser) or in the address bar (right next to the URL). The entire site does not necessarily need to be secured in this fashion, but it is essential on any page where you are asked to submit any personal information.
![]()
Give Out Minimal Information – No online shopping site needs you social security number or your birth date. These are two things you should never give out, especially when combined with your credit card information. If this information gets in the wrong hands you might have your identity stolen.
Use Strong Passwords – A lot of online shopping sites require you to have an account. The stronger your password, the less likely someone can hack into your account and use your saved card information.
The best advice for this is to not use the same password for all of your e-commerce accounts. If you happen to get hacked on one site, most likely the attacker will try the same password on other sites.
- Learn more about strong passwords.
Best Practices to Stay Safe
Check Statements Regularly – Many wait to look at their credit card and bank statements until the end of the month. During the holiday season, if you are shopping online often you should regularly check up on your transactions. This will give you time to catch any fraudulent charges. Most banks and card issuers give you 30 days to report any problems. If you don’t notify the bank within that period, you may be liable for any fraudulent charges made in your name.
 Skip the Gift Cards – Gift cards are always a common present to give around the holidays. Many sites like to auction off gift cards which end up having little or no funds on them. Skip buying them online and always buy gift cards straight from the source.
Skip the Gift Cards – Gift cards are always a common present to give around the holidays. Many sites like to auction off gift cards which end up having little or no funds on them. Skip buying them online and always buy gift cards straight from the source.
Print or Save Receipts – As with in-store purchases, you should receive some sort of payment receipt. Most likely you will receive an emailed receipt with a confirmation of your purchase. It is wise to save these documents in case something goes wrong.
 Don’t Shop Online Publicly – If you are out and about, turn off your public Wi-Fi and use the data on your phone or wait until you are using a trusted private network before making a purchase.
Don’t Shop Online Publicly – If you are out and about, turn off your public Wi-Fi and use the data on your phone or wait until you are using a trusted private network before making a purchase.
Most public networks and Wi-Fi hotspots do not encrypt your data, making identity theft much more likely.
Use The Too Good To Be True Rule – If it sounds too good to be true then it most likely isn’t true. If you are getting an extremely good deal or something for free then it’s almost certainly a scam.
Check out Mcafee’s 12 scams of Christmas.
Sources:
http://www.pcmag.com/article2/0,2817,2373130,00.asp
Email Newsletters in the Digital Age
In a digital age, sending out email newsletters instead of paper newsletters has become much more popular. And why not? The marketing potential of cheap, nearly instant communication with interested customers is difficult to overstate.
The content within your newsletter can greatly affect your readership and business. Read on to learn what to include in your newsletter and how to organize it to more effectively generate leads.
Digital Versus Paper Newsletters
Digital Newsletter Pros:
Cheaper – Everyone is looking for a way to save money and sending out an electronic newsletter can cost much less than running a traditional mail equivalent.
Easy Distribution – Email is much easier to manage than paper mail. Email address lists are usually easier to keep up to date than mailing addresses. And with near instant delivery, you can send out newsletters much more frequently than by paper mail.
Better Targeted Audience – Since a user must opt in, you are marketing to a more targeted, engaged audience.
 Gain More Audience – A digital newsletter has a better chance of being shared than its paper equivalent. An online share opens your marketing up to a much wider audience, which drives more traffic to your website.
Gain More Audience – A digital newsletter has a better chance of being shared than its paper equivalent. An online share opens your marketing up to a much wider audience, which drives more traffic to your website.
Use of Statistics – Most email marketing services provide statistics including open, click, bounce, and unsubscribe rates. These statistics can help you better tailor your content to your audience. If your open rate is low maybe you need a more interesting and eye-catching subject line, for example.
Digital Newsletter Cons:
Easily Ignored or Lost – Amongst the barrage of emails people receive on a daily basis, your newsletter can easily be overlooked.
 Viewed as Spam – Your subscribers’ email provider might tag your newsletter as spam. It’s a good idea to encourage your subscribers to add your newsletter’s FROM address to their address book. This prevents email programs from flagging your newsletters as spam.
Viewed as Spam – Your subscribers’ email provider might tag your newsletter as spam. It’s a good idea to encourage your subscribers to add your newsletter’s FROM address to their address book. This prevents email programs from flagging your newsletters as spam.
What should be in your Newsletter
90% Educational and 10% Promotional  – Promoting yourself too much can be a major turn off. If your newsletter constantly makes a subscriber feel pressured to buy, they will likely unsubscribe.
– Promoting yourself too much can be a major turn off. If your newsletter constantly makes a subscriber feel pressured to buy, they will likely unsubscribe.

Instead, include content that educates the subscriber or has relevant information that ties in with the items/services you are promoting.
Creative Subject Lines – A good subject is the first thing people see. Interesting subject lines entice users to click. Read some tips for creating a good subject line.
Another option is to use the same subject line each time you send out your newsletter. This may seem boring but can build a sense of familiarity with your subscriber base so they do not accidentally delete your messages.
One Main Call to Action – Most of the time you will have many call-to-actions within your newsletter, but make sure to highlight only one of them so as no to overwhelm your readers.
Straight Forward Design – Stay away from long paragraphs and bullet your information. This makes it easier to read and keeps your audience interested.
 Shares, Links, and Unsubscribe – Include an easy share button. Many times if your audience likes your content they will want to share it.
Shares, Links, and Unsubscribe – Include an easy share button. Many times if your audience likes your content they will want to share it.
Have links to your website and any other websites you may have a partnership with.
Always give your readers the option to unsubscribe. If your unsubscribe feature does not work, it will frustrate your subscribers and probably get you blacklisted for violating the CAN-SPAM Act.
 Contact Information – Have your business contact information prominently displayed in your newsletter.
Contact Information – Have your business contact information prominently displayed in your newsletter.
Photos – Have a balance between photos and text. Having too many of either can make your email look like spam. Try to spread your photos out and link them back to a relevant web page.
Let Appletree Mediaworks Help you
Need help designing, managing, and sending your newsletter?
Let Appletree Mediaworks take care of your newsletter. We will work with you as often as needed to gather content, design the template, manage your email list, and schedule your newsletter. We stay up with all the latest technology trends and laws so you can focus on running your business.
Contact Us TodaySafe Harbor Rule Invalidated, How it Affects You
The Data Safe Harbor Rule
 The Safe Harbor Rule was established in 2000 between the European Union (EU) and the United States (US). This agreement allowed businesses to legally funnel information across the Atlantic. Such data is normally transferred during global commerce, email correspondence, and even social media communication. Europe has stricter privacy guidelines to protect its citizens than the US does. Under the Safe Harbor agreement, US companies could “self-certify” that they met Europe’s stricter privacy standards in order to gain access to European markets.
The Safe Harbor Rule was established in 2000 between the European Union (EU) and the United States (US). This agreement allowed businesses to legally funnel information across the Atlantic. Such data is normally transferred during global commerce, email correspondence, and even social media communication. Europe has stricter privacy guidelines to protect its citizens than the US does. Under the Safe Harbor agreement, US companies could “self-certify” that they met Europe’s stricter privacy standards in order to gain access to European markets.
In early October, the European Court of Justice ruled that the US approach to domestic surveillance was not up to European standards. Basically, this happened because the court was concerned that the US would compromise the data of European citizens swept up in our country’s growing mass surveillance machine. Consequently, this ruling made the Safe Harbor pact invalid virtually overnight.
The Safe Harbor Agreement 2.0
The European Union and the Unites States will be meeting on December 17th to create a new agreement for the Safe Harbor. They plan to conclude this agreement in January of 2016. The EU would like to see some changes in the new agreement such as:
- Privacy watchdogs to challenge US companies’ handling of EU data
- European citizens should be able to complain directly to national authorities about data protection
What Does an Invalid Ruling of Safe Harbor Mean?
This affects businesses and consumers from both the European Union and United States. Over 4,000 companies rely on the Safe Harbor for their data transfers, including:
Effects on Companies:
This affects any US-based company doing online business in the EU.
 Many companies that relied on the Safe Harbor “Self Certification” will now have to obtain independent certification.
Many companies that relied on the Safe Harbor “Self Certification” will now have to obtain independent certification.
In Europe, EU standards from 1995 are now being used to determine whether a company’s data sharing is permissible. As of now, the EU operates under the Data Protection Directive. This requires that companies only transfer data to countries that offer adequate privacy protection.
For More Information: With Safe Harbor now “Invalid,” Companies Must Change Data Practices
Effects on Consumers:
Consumers in the US might not notice a substantial difference. European consumers may be cut off from US companies for a time, depending on how stringent the new rules become. It may take some time before US based companies have made the necessary adjustments to do business with the EU again.
Microsoft’s Solution
 Microsoft has stated they will be storing data in a German company, Deutsche Telekom, for their European cloud computing customers. Microsoft will not be able to access the data without permission of either the customer or the company.
Microsoft has stated they will be storing data in a German company, Deutsche Telekom, for their European cloud computing customers. Microsoft will not be able to access the data without permission of either the customer or the company.
This solution may be too expensive for many companies. As a result, the US has started offering customers and partners the opportunity to enter into ‘data processing addendums’. However, these are only a temporary solution. Consequently, many companies are awaiting to hear what’s in the new Safe Harbor Rule.
How the Internet Helps in a Crisis
Everyone has heard about the recent Paris Attacks on November 13th. Many people have found that the Internet helps in a crisis. The Internet can help to coordinate relief efforts while providing essential communication services to the unfortunate individuals involved in a disaster.
Google Crisis
![]() Google has created some powerful tools to help save the day in times of crisis.
Google has created some powerful tools to help save the day in times of crisis.
Crisis Response – Because Google’s crisis response team analyzes each crisis, each response may be slightly different.
A specific response may include:
- Creating a Resource Page – This is a simple web page containing the most relevant emergency information and tools available for a given crisis.
- Launching Google Person Finder – This is an application which connects friends and loved ones following a disaster. This is useful when there is a large number of missing people and traditional communication lines are unavailable.
- How it works: Google’s Person Finder page lists current disasters. Click on a disaster and you can then choose from either “I’m looking for someone” or “I have information about someone”.
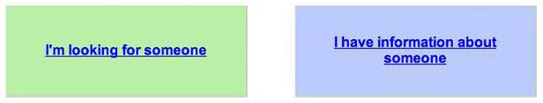
- How it works: Google’s Person Finder page lists current disasters. Click on a disaster and you can then choose from either “I’m looking for someone” or “I have information about someone”.
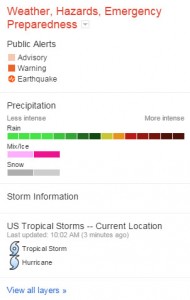 Hosting a Crisis Map – This is a map that displays information concerning the disaster such as storm paths, flood zones, evacuation routes, shelter locations, and power outages. This includes official content and user-generated content.
Hosting a Crisis Map – This is a map that displays information concerning the disaster such as storm paths, flood zones, evacuation routes, shelter locations, and power outages. This includes official content and user-generated content.
Tools For Responders – Do you think your organization may be able to help in a disaster? Google also provides some tools for responders.
- Google Public Alerts – An organization can send emergency alerts if they are relevant to an ongoing crisis. These alerts will appear on Google’s search results, maps, and android devices (using Google Now).
- Person Finder – This can be embedded into your company’s website.
- Crisis Map – This can be embedded in your company’s website.
- Other Google Tools – Docs, spreadsheets, and Earth are all useful tools for responders.
Facebook Safety Check Tool
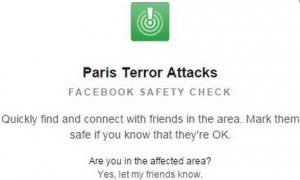 The Facebook Safety Check Tool was originally created for natural disasters. After the Paris Attacks, it has opened up to man made disasters as well. Basically, the Safety Check tool notifies friends and loved ones that you’re safe during a disaster.
The Facebook Safety Check Tool was originally created for natural disasters. After the Paris Attacks, it has opened up to man made disasters as well. Basically, the Safety Check tool notifies friends and loved ones that you’re safe during a disaster.
This was original inspired by the 2011 Tohoku earthquake and tsunami and was then released on October 15th, 2014.
How It Works:
- Affected Area Notification – Facebook sends you a notification if you are in an affected area and asks if you are safe.
- “I’m Safe” –
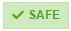 After receiving the notification, if you click or tap “I’m Safe” it adds a green “I’m Safe” box next to your name so others can see your status. Other friends may also confirm whether or not you are safe.
After receiving the notification, if you click or tap “I’m Safe” it adds a green “I’m Safe” box next to your name so others can see your status. Other friends may also confirm whether or not you are safe. - Safe Friends Notification – After the tool has been activated you will then receive notifications when your friends have marked themselves as safe.
 Ways Facebook responded to Paris Attacks:
Ways Facebook responded to Paris Attacks:
- Enabled their safety check
- Created a profile picture filter of blue, white, and red
Twitter Alerts
 What? This is an alert that contains vital real-time information during a fast moving emergency. Since this feature is intended for crisis, disaster, and emergency communications, these alerts consist of:
What? This is an alert that contains vital real-time information during a fast moving emergency. Since this feature is intended for crisis, disaster, and emergency communications, these alerts consist of:
- Warnings of imminent dangers
- Preventive instructions
- Evacuation directions
- Urgent safety alerts
- Information on access to essential resources
- Information on critical transit and utility outages
- Crowd and misinformation management.
- Who? Only these groups are authorized to send an alert:
- Law enforcement
- Public safety agencies
- Emergency management agencies
- City and municipal governments
- County and regional agencies
- Select state, federal, and nation agencies and NGOs
- When? Twitter Alerts are used when traditional ways of communication are not available. Such emergencies may include:
 Natural disasters
Natural disasters- Severe weather
- Biological incidents
- Chemical or hazardous materials emergencies
- Nuclear
- Radiological incidents
- Explosions
- Food and agricultural incidents
- Cyber incidents
- Terrorism incidents
- Crime
- Major transportation incidents
- Where? Twitter Alerts send as SMS notifications. Also, an orange bell displays next to alerts on your timeline.
Think your organization qualifies? Complete the Twitter Alert Enrollment Form
How do I get Twitter alerts? Twitter Alert Setup
Ways Twitter responded to Paris Attacks:
- Use of hastags
- #PorteOuverte – Translates to Open Doors. This means you need a safe place to stay or you have a safe place (with open doors).
- #PrayForParis – Used to show support for Paris
- #RechercheParis – Translates to Search Paris. Friends and loved ones used this to find each other.
Airbnb Disaster Relief Program
 As a result of Hurricane Sandy in October 2012, many people in New York opened their doors to stranded individuals.
As a result of Hurricane Sandy in October 2012, many people in New York opened their doors to stranded individuals.
Airbnb, the unique online rental listing company, wanted to do the same during a disaster. They eventually created their very own disaster relief program. Airbnb even partnered with local government agencies and disaster relief organizations to make this program as effective as possible.
How it works Airbnb first sends out emails to room hosts in affected areas asking if they are in a position help. Hosts may then choose whether or not to participate. Finally, participating hosts open their doors (for free) to help people affected by the disaster.
- Airbnb still offers 12/7 customer support, trust & safety tools, host guarantee and all other services.
- Airbnb also uses their network to provide disaster information to the guests and hosts.
Ways Airbnb responded to Paris Attacks:
- Activated their disaster relief program and many hosts in the affected areas opened their doors to help keep people safe.
Other companies that helped during the crisis
Uber – Turned off their city price surge.
Verzion, T-Mobile, Sprint, AT&T, Google, and Skype – Made calling and texts from United States to France available for free
Advertising Online for your Business
Advertising your business online can boost your sales and website traffic if done the correct way. There are many different ways and places to advertise online. Already have online ads? You may need to do some updates for today’s mobile world. Creating online ads has a good portion of planning before you place an advertisement. Learn all the types and best way to design your advertisement that works for your business.
Types of Advertising Online
-
Native – This is the new big way of advertising online. This form complements the website it is on. It will be relevant to the content and/or audience on the website.
- Banner – This type has been a go-to for the longest time but has become obsolete. We are now in a mobile world and banner ads do not fit the screens most people are using.
- 54% of users don’t click banner ads because they don’t trust them.
- Native ads are viewed 53% more than banner ads, according to Dedicated Media.
- Search – Most popular example of this is Google Adwords. This type of ad shows up from search engines using Cost-per-click (CPC) and Pay-per-click (PPC)
-
Screen Filled – These are mostly for mobile use and take over the entire screen. Usually these only show up every 10 screens or so to not overwhelm user.
 Social Media – Sites such as Facebook, Twitter, and Pinterest have options to create ads, sponsored posts, or promoted posts. This can be organic or paid. Pew Research estimates that 74% of all online adults use social networking sites.
Social Media – Sites such as Facebook, Twitter, and Pinterest have options to create ads, sponsored posts, or promoted posts. This can be organic or paid. Pew Research estimates that 74% of all online adults use social networking sites.
- Pop-Up – This is a very popular but described as most annoying. This consists of a small pop-up window upon opening of site and possibly when leaving.
Now that you know what types are out there how do you design an advertisement that works.
Target Your Audience – Just as you do with just about everything else with your business you need to know who your audience are.
 Geotargeting – Target your audience by country, state, city or zip-code. The closer to home your business is to a customer the more likely they will find your advertisement useful. Find out where your current customers are located using your websites analytics and tailor ads to that location.
Geotargeting – Target your audience by country, state, city or zip-code. The closer to home your business is to a customer the more likely they will find your advertisement useful. Find out where your current customers are located using your websites analytics and tailor ads to that location.- Contextual – Place you advertisement next to content that involves the same keywords and concepts your audience is browsing. Use your websites analytics to see the best keywords for your site and/or products or services.

- If a customer is reading a blog site about ‘running’ having your ad with your running shoes would get more traffic than putting it on a blog site about movie reviews.
- Behavioral – This uses analytics and data collecting to target specific users. It tailors to someone by a combination of their searches, website views, and products researched. Although this is highly controversial type but seems to be effective.
Design – After finding your target audience you can decide what you want your advertisement should look like. Make sure you experiment with these a bit. Use different colors, fonts, sizes, and types until you find what appeals to your customers.
 Images – Like you have always heard a picture is worth a million words which is very helpful when using such a small space to get your point across. Make sure they are eye-catching and keep it simple to draw your audience in.
Images – Like you have always heard a picture is worth a million words which is very helpful when using such a small space to get your point across. Make sure they are eye-catching and keep it simple to draw your audience in.- Videos – This seems to be a growing idea. Have a video of the commercial of your product or service, customer testimonials, or demonstrations. This has been commonly called annoying especially for those listening to music or at work.
A User Tip: Best technique I have seen is the rollover effect. It only plays when the mouse is rolled over it and it pauses when the mouse is not on it. - Text – Never use only text on an ad. It looks cheap and crude and almost looks more like a scam. Instead balance it well with your image.
- Urgency – Create a sense of urgency with your ad to get more immediate acts. Examples being time limited coupons, text of “Lowest Price”, or express the stock quantity (even though you may be restocking).
- SMS – With mobile being so big, using SMS texting with business has become very big. A Taco Bell example is “Text ‘TBICE’ to 30364 for a free Frutista Freeze with any food purchase.” Taco Bell sent out in excess of 29,500 SMS coupons, and was so well liked that at the end of the 5 week campaign, 93% of those SMS subscribers were still subscribed to the campaign. This keeps customers interested in your company as long as they are subscribed.
Make it Responsive – Users expect some sort of interactivity with the advertisement.
-
 Always have your ad clickable, leading to a page, video, or website
Always have your ad clickable, leading to a page, video, or website
- Try it now. Click the image.
- Have ad expand upon mouse rollover
- Use a Text box to enter sweepstakes or subscribe to emails
- Have a button leading to product or webpage
- Try it now. Click the button.
[button size=”small” link=”https://appletreemediaworks.com/blog/” target=”_blank” color=”blue”]Read the Appletree Media Blog![/button]
- Try it now. Click the button.
Use Day Parting – Often you can pick the time your advertisement is displayed for optimal your audience. Depending on what type of product or service you are making an ad for will depend on the time you may want it displayed.
Examples:
- A restaurant would advertise during afternoon hours when users may be looking for a place to eat.
- A company running weekend sales would run their ad all day Friday.
Now that you have your advertisement created, where should you place it?
Other Websites – You can find and partner with relevant blog sites and news sites when using native advertisements. You can also partner with a mobile display advertising partner (such as Mojiva or Google DoubleClick) that does the work of finding sites for you.
Apps – Depending on your product or service reaching a range of people who use applications on their phone can create a lot of traffic. These are usually the screen filled ads that only show up every 10 screens or so.
- Some mobile ad platforms
Search Engines – This is one of the most popular probably because of how popular search engines have become. Placing Ads at MSN, Yahoo, and Google can be very efficient.
Sources:
http://dealnerd.net/10-types-of-online-advertising-and-when-you-should-use-them/
http://www.appia.com/blog/6-tips-for-building-highly-effective-mobile-ad-campaigns
http://www.pr2.com/webads3.htm
How to use Web Analytics for your business
How to use Web Analytics for your business
Analytics is data analysis that usual involves taking past data to find trends and effects or decisions or events. It can also compare old data with new data using a given tool or scenario. In the sense of your online part of your business this can help measure engagement to your website and your social media. It can help steer you in a direction of gaining new customers and keeping current ones interested.
There are several tools out there to measure analytics on your websites and almost every social media sight has their own analytic tools. The important part of analytics is not just knowing that you can get this data but knowing how to use it to improvement you online content.
5 Key Analytic Points
 Visits – Usually your goal with this is to have as many visits as possible. Since this is a pretty general analytic there isn’t much specifically you can do with this information to raise your visits.
Visits – Usually your goal with this is to have as many visits as possible. Since this is a pretty general analytic there isn’t much specifically you can do with this information to raise your visits.
Traffic Source – A better way to understand your visits is seeing where they are coming from. There are 5 main sources:
 Organic Search
Organic Search
Traffic comes from a search engine that is unpaid.
Improvent: Improve your SEO (Search Engine Optimization).
This includes(but not limited to):
- Keyword list
- High-quality content
- Page titles
- Meta description
 Paid Search
Paid Search
Traffic comes from a search engine that is a paid. Most recognized in Google as top section when you search.
Paid search includes:
- Cost-per-click (CPC) – You pay every time ad is clicked
- Cost-per-impression (CPM) – You pay every 1,000 times ad appears on page
- Google Adwords – Uses both of these types.
 Direct
Direct
Traffic comes from directly typing in the web address to browser.
Best practice:
- Have a memorable domain name.
- Use your business name – customer directly types your business name in the browser instead of a search engine.
 Referral
Referral
Traffic comes from a link inside another website.
Improvement:
- Sponsor or speak at local events
- Guest posts – Guest blog post on another site. Learn some do’s and don’ts.
 Social
Social
Traffic comes from social media such as Facebook, twitter, Pinterest, etc.
Improvements:
- Have your website on your profile
- Have posts (but not much) that link back to your website – Could be promoting a recent blog post, product, service, etc.
- Get your pages on social bookmarking sites such as Stumble Upon
Bounce Rate – A bounce is when someone enters your site and then exits without seeing another page on the website. The goal is to keep this low. One condition this is not true, if the web page has a “phone number that the user is looking for, they may find the page, call the number and exit the site: This will count as a bounce but it’s a good bounce!” B2C
 Usually is a visitor bounces it means 1 of 2 things:
Usually is a visitor bounces it means 1 of 2 things:
- They did not find what they were looking for
- The webpage was difficult to use.
How to Improve:
- Using proper keywords – This will attract the correct audience so they find what they are looking for.
- Make website User-Friendly – Webpage user difficulty could be from a bad layout, confusing navigation menu, not mobile friendly, slow page load time, pop-up or self-loading ads, difficult to read.
 Time On Site – This measures the time spent on your site as a whole. Such things that influence this is how interesting your site it, how good the navigation menus are, links to other pages on site.
Time On Site – This measures the time spent on your site as a whole. Such things that influence this is how interesting your site it, how good the navigation menus are, links to other pages on site.
Pages Per Visit – This measures how many pages were viewed in one visit.
Some other things to think about:
- Location – tailor your site to the most popular cities the your viewers are from.
- Monitor size – tailor you site to the most popular monitor size your users are using, ultimately try to make it optimized for all especially mobile sizes.
Top Web Analytics Tools
Google Analytics
Clicky
Church Analytics
KISSmetrics
Open Web Analytics
Clicktale
CrazyEgg
Piwik
CloudFlare
Scam Emails
 Scam emails are a very popular and while most email services have a spam sorting feature built in, not all will be sorted properly. Scams can look like they came from a friend, a business you interact with or do not interact with, federal agencies, charities, or complete strangers.
Scam emails are a very popular and while most email services have a spam sorting feature built in, not all will be sorted properly. Scams can look like they came from a friend, a business you interact with or do not interact with, federal agencies, charities, or complete strangers.
There are ways to notice whether the emails are legitimate or not. There are extra precautions you can take for those that may not be as noticeable but still suspicious. However sometimes you do fall victim to these and there are some steps to take if that happens.
Common Types of Scams
There are so many types of email scams out there but some of the popular ones include bogus offers, phishing, Trojan Horse, and request for help.
Bogus Offers
These usually involve discounted or free items or too good to be true products or services. Your best bet if it sound too good to be true then you are probably right.
Bogus Business Opportunities
 Subject Lines: Make a Regular Income with Online Auctions, Put your computer to work for you!, Get Rich Click, or Use the Internet to make money.
Subject Lines: Make a Regular Income with Online Auctions, Put your computer to work for you!, Get Rich Click, or Use the Internet to make money.
Scam: Most of these contain links that either contain malware, bring you to bogus sites that ask you to enter personal information or pay for an “information kit”
Health and Diet Scams
Subject Lines: Need to lose weight for summer?, Reduce body fat and build lean muscle without exercise, CONTROL YOUR WEIGHT!!, or Takes years off your appearance.
Scam: Most contain links that contain malware. Some may contain fake customer testimonials to convince you.
Easy Money or Free Items
Always avoid anything with these similar titles. It is almost always a scam.
Scam: They usually lead to a website you have to enter your information in to steal it or ask for some sort of fee for “processing” or “shipping”.
Phishing
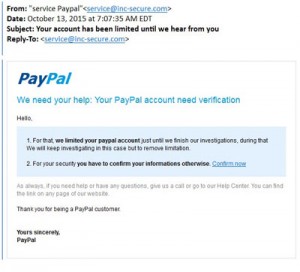 The definition is in the name, these are people “fishing” for your information. These types of scams exploit existing companies that you may or may not interact with. Using a popular companies name can make you believe the email is real.
The definition is in the name, these are people “fishing” for your information. These types of scams exploit existing companies that you may or may not interact with. Using a popular companies name can make you believe the email is real.
Account or Credit Information
Subject Lines: Your account is going to expire!, You’re Pre-Approved, or Guaranteed credit card
Scam: This will most likely contain a link that downloads malware, more specifically a keystroke logging malware so when it directs you to the convincing but fake website it steals your sensitive information.
Trojan Horse
These are emails that contain attachments. They usually promise something funny, a photograph, or a patch for software vulnerability.
Subject Line: Funny, Hi Friend, Check it out!
Scam: These attachments contain malware making your device vulnerable and possible installs software stealing your information.
Requests for Help
Disaster Relief
Fake charity websites are created to get people to donate money to a disaster such as 9-11 or Katrina.
Scam: Link inside email will direct you to offer your bank or credit card information to steal.
Nigerian – 419
These are very common scam emails that include sob stories, unfailingly polite language, and a promise of a big payoff.
Subject Lines: My Dearest Friend, Contact my secretary, and from the desk of.
Scam: Most offer huge payout if you help. Only problem is you need to pay a fee or “tax” to get the money. This allows scammer to take your money and identity.
Most Recent Reported Scams
 WhatsApp Scam Email
WhatsApp Scam Email
This email poses as a popular mobile phone app called “WhatsApp” claiming it has an incoming voice message for the user. Inside the email is a video message that if played will add malware to your device or bring you to a site that will add malware.
Credit Card Chip Scam Email
With new credit card chips on the rise, scammers have created an email that say you need to update your information to receive your new card. This is a method of phishing, and scammers even use the credit company’s logos. “… card companies won’t be giving you a heads-up, you’ll simply get your new card in the mail…”
How to recognize that an email is a scam?
- Sounds too good to be true
- Include words like easy, free, fast, and quick
- All capital letters
- Sounds urgent
- Uses misspelled words or slang
Sender
- Email account name does not match sender name.
 Example:
Example:
From: Meijer (ShopForMore@mymeijer.com) – The name of sender and email account match well enough to show some trust from the sender
Example:
From: Allied & NAVL (79JN@kipwring.com) – Most businesses have their business name after @ and before .com and start with either info, support, and noreply.
Body of Email
- Information is extremely vague – Especially when pertaining to subject lines about account expiration or upgrade, is a tactic to get you to click on link because of your confusion. This is also common in the ‘get rich quick scams’ and ‘lose weight fast’ using you curiosity to their advantage.
- Image is only thing in body – A real email will try to use a good mix of images and text.
- Plain text is only thing in body – Once again a real email will try to use a good mix of images and text.
How to avoid these scam emails?
 Install/Update Antivirus Software – This will help block any email-born viruses
Install/Update Antivirus Software – This will help block any email-born viruses
- Android Antivirus Apps
- iOS Antivirus Apps
- Desktop Antivirus
Install/Update Personal Firewall – This will also help block any email-born viruses
Setup Email Spam Filtering – A lot of emails offer spam filtering which does a fairly good job. This is not 100% effective though so do not rely on spam filtering.
 Setup Email Security – A lot of emails automatically have a security set up for spam but some you may need to configure yourself. Anytime you make an account on the internet you need to always check the security and privacy options to protect yourself.
Setup Email Security – A lot of emails automatically have a security set up for spam but some you may need to configure yourself. Anytime you make an account on the internet you need to always check the security and privacy options to protect yourself.
Do Not Trust Unsoliciated Email – These are individuals or organizations that are unknown. Most likely they are not a trustworthy sender.
Tip: Anything of real importance will contact you by phone or mail. Anything federal/Government related will only contact you by mail.
Be Cautious About Attachments – This is a very easy way to download malware onto your device. To be safe, only open attachments from trusted senders.
 Do Not Click Links – This is another easy way to download malware onto your device. Even though the link name may look familiar, mimicking a real business, it does not mean it is real.
Do Not Click Links – This is another easy way to download malware onto your device. Even though the link name may look familiar, mimicking a real business, it does not mean it is real.
Click link to see an example: https://www.youtube.com – Looks like a real link to YouTube but it didn’t take you to YouTube
Tip: Not sure if a link is safe? Type it into your browser instead of clicking on the link.
If you have been a victim of fraud email
- Run a antivirus scan
- Contact Credit Agency – You can place an alert with any one of the three major credit bureaus signals to potential creditors that you could be a victim of identity theft.
- Update Account Logons – Change passwords on as many accounts as possible
- Report it to Action Fraud
- Fill a complaint at the Federal Bureau of Investigation Internet Crime Complaint Center and review recent press releases
- File a report with the Federal Trade Commission
[stylebox color=”gray” bgcolor=”#7ad0ff” textcolor=”#000000″]
TIPS:
- IRS and court appearances will never contact you by email. They will most likely use paper mail.
- Type links into your browser instead of clicking on the link. This will prevent a redirected link.
- Do not open attachments unless from a trusted sender.
- If it is free or too good to be true then do not trust it.
- Before you donate to charity, research the company to make sure it is real. Use the Guidestar Nonprofit Directory to search for registered charities.
- Do not send money to people you do not know.
- If the subject line says urgent it’s most likely a scam.
- If buying any items, use scamAdviser to check website trust ratings.
[/stylebox]
Google Event. The Good and The Bad.
Google held their press event on Tuesday, September 19th in San Francisco announcing many new products such as the Nexus 6P and 5X, the new Chromecast 2, Chromecast Audio, and the Pixel C. They also announced their new Operating System.
 Nexus 6P
Nexus 6P
This was the most anticipated product coming out of Google and is considered the “flagship”. While there are a lot of great features in this new phone some have found minor complaints about the Nexus 6P
5.7 Inches
1440 Resolution
Metal Exterior
Gorilla Glass 4
7.3mm Thick
Snapdragon 810 Processor
Complaint: Users disappointed in this version of Snapdragon
Android 6.0 Marshmallow Operating System
3GB RAM
Complaint: Future is looking at 4GB and some worry this will not be enough RAM
Project Fi (WIFI) Availability
Updated Camera – 8 Megapixel front-facing and 12.3 Megapixel Back facing (4K video and slow-motion shots)
Complaint: There is a camera bump (similar to the iPhone bump) and an “ugly” black bar
Complaint: Does not have optical image stabilization (OIS)
2 Front Facing Speakers
Nexus Imprint – Fingerprint sensor. Used to easily unlock phone and can be used to authorize payments on android pay or the play store.
Larger Battery
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Complaint: Future is leaning towards the wireless charging. Users disappointed that was not incorporated.
Colors – Frost White, Aluminum, and graphite
Cost – $499
 Nexus 5X
Nexus 5X
The Nexus 5X is considered the affordable alternative to the Nexus 6P over $100 cheaper. Even that being said it still has a lot of great features but the biggest worry it is not worth the update from their current phone. (ibtimes)
5.2 Inches
1080 Resolution
Gorilla Glass 3
Equipped with Android Marshmallow
Project Fi (Wireless Network) availability
Bigger battery
Nexus Imprint – Fingerprint sensor. Used to easily unlock phone and can be used to authorize payments on android pay or the play store.
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Complaint: Future is leaning towards the wireless charging. Users disappointed that was not incorporated.
Snapdragon 808 processor – Many like this processor better than Nexus 6P’s Snapdragon 810
12-megapixel camera (4k video)
Cost – $379
Chromecast 2
Chromecast has gotten some updates but luckily the price did not change. A new look along with better Wifi are only a few update. Some features are still yet to come in the next year.
Wifi Updates – Supports 5GHz Wi-Fi and has 2 antennas for better streaming
New Look – A small disc with bendable HDMI arm
Colors – red, yellow, and black
Cost – $35 (no change)
 Chromecast App Update – Universal voice search tool – “fast Play” videos google thinks you want to watch – “what’s On” popular content (youtube and Netflix) – adding new apps, showtime, sling TV, NBA, and NHL and Spotify
Chromecast App Update – Universal voice search tool – “fast Play” videos google thinks you want to watch – “what’s On” popular content (youtube and Netflix) – adding new apps, showtime, sling TV, NBA, and NHL and Spotify
Only Complaint: Does not support 4k TVs
Chromecast Audio
Google announced a brand new product called Chromecast Audio. A neat way to put life back into your old speakers. You can connect and send music. Many were happy to here Chromecast now supports Spotify. With it’s cute look it seems to be a hit.
Plugs Into Speaker – 3.5mm audio port
OS Support – iOS/Android/Chrome
Supports RCA or optical outputs
Connect and Send Music – Using google play, Pandora, NPR one, Rdio, and Spotify (controlled by phone lock screen and android smartwatch or android and chrome tab)
Cool Look -Looks like a mini vinyl record
Cost – $35
Complaint: Users are concerned with compatibility with speakers.
 Pixel C
Pixel C
Top feature of the tablet Pixel C is that fact it is light but solid. The keyboard connects well and feels stable. While there is not a release date Google promises it will be out by the holidays.
10.2 Inch Tablet
Detachable Keyboard
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Nvidia X1 Processor
Complaint: Users likes Intel Processor and not sure why they switched.
3GB of RAM
Android Marshmallow
Complaint: Users want the Chrome OS. Using a mobile OS limits some of the things that can be done on the tablet.
Cost – $499
Keyboard cost – $149
Complaint: Enter and delete key take time to getting used to placement.
Complaint: No touch pad. Sometimes the touchscreen is not optimal e.i. word documents.
 Android 6.0 Marshmallow
Android 6.0 Marshmallow
Android’s new ‘M’ operating system is the 6.0 Marshmallow. It comes with some desirable improvements.
Notifications – More consistent
Improves Battery Life
Fine-Grained Privacy Controls
Now on Tap – Google searches and voice interaction in individual apps
Doze – Power-saving mode – shuts down processes when hasn’t been moving or used
Not released to enough phones to have any known complaints
Devices to get Android Marshmallow:
End of 2015 – HTC One M9, One M8
Early 2016 – HTC M9+, HTC E9, HTCME, HTC E8, HTC M8 EYE, HTC Butterfly 3, HTC Desire 826, HTC Desire 820, HTC Desire 815
Samsung has yet to say except their new devices will not be launching with it. – techRepublic
Protect Your Smartphone From Malware
With the recent scares about Android’s ‘StageFright 2.0’ bug, that you get by opening a MP3 or MP4 file, it might get your wondering more about whether you have or had a bug on your phone. Different malware includes adware, bug, spyware, Trojan horse, virus, and many more (Learn more about Malware types ) There are some signs that your phone is being attacked and many ways to prevent your smartphone from getting malware. Already have a virus? There are ways to get your phone back in your control.
Has your phone been bugged? Here are some signs your phone is being tapped into:
- Difficulty Shutting Down – You may experience a delay in shutting down your phone. Often you will notice the back-light is still on even after it’s shut off.
- Odd Activity – This can consist of distortions on your screen or even application being installed by itself.
 Call Interference – During phone calls there may be unexplained background noises, clicks, echoes, or static.
Call Interference – During phone calls there may be unexplained background noises, clicks, echoes, or static.- Data Use Increase – Drastic increases in data without a good explanation. Not sure how to tell… “Look at how much data your device is using, and see if there’s a big discrepancy between how much data you’re using, and how much your applications are using. Any difference involving 10MB or more might be a sign of ‘parasitic activity’” – DarkReading
- Low Battery and High Temperatures – Both paired together could be caused by a constantly running application tapping into your phone.
- Coded Text Messages – This is a strong sign your phone has been tapped
The 2015 Internet Security Threat Report from Symantec showed that data breaches surged by 23 percent last year, and nearly a million new pieces of malware (“malicious software”) were created per day. Almost 1 in 5 Android apps available last year were actually malware in disguise, says the same report. The more popular smartphones and downloading apps become, the more popular malware and other viruses are becoming as well. Be smart and keep your smartphone safe from these bugs.
How do you prevent your phone from getting infected?
Strong Lockscreens – The stronger your passcode to get your phone unlocked the more secure your phone is.
- Not sure how to set up a lockscreen…

- Android Lockscreen Setup
- iPhone Lockscreen Setup
- Top lockscreen apps…
Get A Security Program – Ultimately the best ones would include anti-virus, anti-malware, anti-spam, anti-phishing defense, and a firewall.
- Android Antivirus Apps
- iOS Antivirus Apps
Update Your OS – There is a reason they come out with updates and new operating systems. The longer you put off updating your phone, the more susceptible it is.
Use Trustworthy Companies – If you are downloading applications, ringtones, wallpapers, etc. always use trustworthy companies, take the time to read reviews too.
Avoid Suspicious Websites – If you feel suspicious there’s good reason.
- How do you tell a website is unsafe? (SpyRambly)
- Poor layout
- Bright and flashing buttons, banners, or images
- Constant pressure to download
- Manipulation used to click on unsafe links
Turn Off Bluetooth – When you are not using the Bluetooth, have it set to off
Take Out Battery – Although this make not as practical for frequent users but if you know you won’t be using your phone for a while, take out the battery.
Don’t Jailbreak – If you jailbreak your phone this leaves you much more susceptible to viruses.
Use the Two Step Verification – This is an extra security step.
- Not sure how to set it up…
- Google 2-Step Verification
- Apple 2-Step Verification
Encrypt Sensitive Information – Another extra security step to help keep you safe.
- How do you encrypt?
 TIP: Backup Your Information – No matter how hard you try to prevent it there is still a chance you will get infected. It is always a good idea to have your information backed up in case you have to wipe your phone clean.
TIP: Backup Your Information – No matter how hard you try to prevent it there is still a chance you will get infected. It is always a good idea to have your information backed up in case you have to wipe your phone clean.
- How do you backup your phone?
- Android Backups
- iPhone Backups
My phone is infected! What do I do now?
- Take out your SIM card at first sign of malware
- Restart your phone in ‘Safe Mode’
 Depending on the severity of the infection:
Depending on the severity of the infection:
- Uninstall the application or remove file/software from where the malware came from
- Reset to factory settings – you can do this on your own or take it to your provider (This is where backing your information up is important)
- Run an anti-virus scan