 Scam emails are a very popular and while most email services have a spam sorting feature built in, not all will be sorted properly. Scams can look like they came from a friend, a business you interact with or do not interact with, federal agencies, charities, or complete strangers.
Scam emails are a very popular and while most email services have a spam sorting feature built in, not all will be sorted properly. Scams can look like they came from a friend, a business you interact with or do not interact with, federal agencies, charities, or complete strangers.
There are ways to notice whether the emails are legitimate or not. There are extra precautions you can take for those that may not be as noticeable but still suspicious. However sometimes you do fall victim to these and there are some steps to take if that happens.
Common Types of Scams
There are so many types of email scams out there but some of the popular ones include bogus offers, phishing, Trojan Horse, and request for help.
Bogus Offers
These usually involve discounted or free items or too good to be true products or services. Your best bet if it sound too good to be true then you are probably right.
Bogus Business Opportunities
 Subject Lines: Make a Regular Income with Online Auctions, Put your computer to work for you!, Get Rich Click, or Use the Internet to make money.
Subject Lines: Make a Regular Income with Online Auctions, Put your computer to work for you!, Get Rich Click, or Use the Internet to make money.
Scam: Most of these contain links that either contain malware, bring you to bogus sites that ask you to enter personal information or pay for an “information kit”
Health and Diet Scams
Subject Lines: Need to lose weight for summer?, Reduce body fat and build lean muscle without exercise, CONTROL YOUR WEIGHT!!, or Takes years off your appearance.
Scam: Most contain links that contain malware. Some may contain fake customer testimonials to convince you.
Easy Money or Free Items
Always avoid anything with these similar titles. It is almost always a scam.
Scam: They usually lead to a website you have to enter your information in to steal it or ask for some sort of fee for “processing” or “shipping”.
Phishing
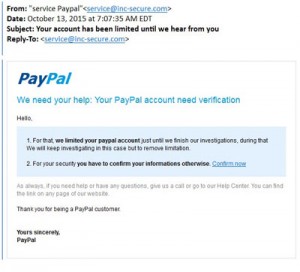 The definition is in the name, these are people “fishing” for your information. These types of scams exploit existing companies that you may or may not interact with. Using a popular companies name can make you believe the email is real.
The definition is in the name, these are people “fishing” for your information. These types of scams exploit existing companies that you may or may not interact with. Using a popular companies name can make you believe the email is real.
Account or Credit Information
Subject Lines: Your account is going to expire!, You’re Pre-Approved, or Guaranteed credit card
Scam: This will most likely contain a link that downloads malware, more specifically a keystroke logging malware so when it directs you to the convincing but fake website it steals your sensitive information.
Trojan Horse
These are emails that contain attachments. They usually promise something funny, a photograph, or a patch for software vulnerability.
Subject Line: Funny, Hi Friend, Check it out!
Scam: These attachments contain malware making your device vulnerable and possible installs software stealing your information.
Requests for Help
Disaster Relief
Fake charity websites are created to get people to donate money to a disaster such as 9-11 or Katrina.
Scam: Link inside email will direct you to offer your bank or credit card information to steal.
Nigerian – 419
These are very common scam emails that include sob stories, unfailingly polite language, and a promise of a big payoff.
Subject Lines: My Dearest Friend, Contact my secretary, and from the desk of.
Scam: Most offer huge payout if you help. Only problem is you need to pay a fee or “tax” to get the money. This allows scammer to take your money and identity.
Most Recent Reported Scams
 WhatsApp Scam Email
WhatsApp Scam Email
This email poses as a popular mobile phone app called “WhatsApp” claiming it has an incoming voice message for the user. Inside the email is a video message that if played will add malware to your device or bring you to a site that will add malware.
Credit Card Chip Scam Email
With new credit card chips on the rise, scammers have created an email that say you need to update your information to receive your new card. This is a method of phishing, and scammers even use the credit company’s logos. “… card companies won’t be giving you a heads-up, you’ll simply get your new card in the mail…”
How to recognize that an email is a scam?
- Sounds too good to be true
- Include words like easy, free, fast, and quick
- All capital letters
- Sounds urgent
- Uses misspelled words or slang
Sender
- Email account name does not match sender name.
 Example:
Example:
From: Meijer (ShopForMore@mymeijer.com) – The name of sender and email account match well enough to show some trust from the sender
Example:
From: Allied & NAVL (79JN@kipwring.com) – Most businesses have their business name after @ and before .com and start with either info, support, and noreply.
Body of Email
- Information is extremely vague – Especially when pertaining to subject lines about account expiration or upgrade, is a tactic to get you to click on link because of your confusion. This is also common in the ‘get rich quick scams’ and ‘lose weight fast’ using you curiosity to their advantage.
- Image is only thing in body – A real email will try to use a good mix of images and text.
- Plain text is only thing in body – Once again a real email will try to use a good mix of images and text.
How to avoid these scam emails?
 Install/Update Antivirus Software – This will help block any email-born viruses
Install/Update Antivirus Software – This will help block any email-born viruses
- Android Antivirus Apps
- iOS Antivirus Apps
- Desktop Antivirus
Install/Update Personal Firewall – This will also help block any email-born viruses
Setup Email Spam Filtering – A lot of emails offer spam filtering which does a fairly good job. This is not 100% effective though so do not rely on spam filtering.
 Setup Email Security – A lot of emails automatically have a security set up for spam but some you may need to configure yourself. Anytime you make an account on the internet you need to always check the security and privacy options to protect yourself.
Setup Email Security – A lot of emails automatically have a security set up for spam but some you may need to configure yourself. Anytime you make an account on the internet you need to always check the security and privacy options to protect yourself.
Do Not Trust Unsoliciated Email – These are individuals or organizations that are unknown. Most likely they are not a trustworthy sender.
Tip: Anything of real importance will contact you by phone or mail. Anything federal/Government related will only contact you by mail.
Be Cautious About Attachments – This is a very easy way to download malware onto your device. To be safe, only open attachments from trusted senders.
 Do Not Click Links – This is another easy way to download malware onto your device. Even though the link name may look familiar, mimicking a real business, it does not mean it is real.
Do Not Click Links – This is another easy way to download malware onto your device. Even though the link name may look familiar, mimicking a real business, it does not mean it is real.
Click link to see an example: https://www.youtube.com – Looks like a real link to YouTube but it didn’t take you to YouTube
Tip: Not sure if a link is safe? Type it into your browser instead of clicking on the link.
If you have been a victim of fraud email
- Run a antivirus scan
- Contact Credit Agency – You can place an alert with any one of the three major credit bureaus signals to potential creditors that you could be a victim of identity theft.
- Update Account Logons – Change passwords on as many accounts as possible
- Report it to Action Fraud
- Fill a complaint at the Federal Bureau of Investigation Internet Crime Complaint Center and review recent press releases
- File a report with the Federal Trade Commission
[stylebox color=”gray” bgcolor=”#7ad0ff” textcolor=”#000000″]
TIPS:
- IRS and court appearances will never contact you by email. They will most likely use paper mail.
- Type links into your browser instead of clicking on the link. This will prevent a redirected link.
- Do not open attachments unless from a trusted sender.
- If it is free or too good to be true then do not trust it.
- Before you donate to charity, research the company to make sure it is real. Use the Guidestar Nonprofit Directory to search for registered charities.
- Do not send money to people you do not know.
- If the subject line says urgent it’s most likely a scam.
- If buying any items, use scamAdviser to check website trust ratings.
[/stylebox]





