Protect Your Smartphone From Malware
With the recent scares about Android’s ‘StageFright 2.0’ bug, that you get by opening a MP3 or MP4 file, it might get your wondering more about whether you have or had a bug on your phone. Different malware includes adware, bug, spyware, Trojan horse, virus, and many more (Learn more about Malware types ) There are some signs that your phone is being attacked and many ways to prevent your smartphone from getting malware. Already have a virus? There are ways to get your phone back in your control.
Has your phone been bugged? Here are some signs your phone is being tapped into:
- Difficulty Shutting Down – You may experience a delay in shutting down your phone. Often you will notice the back-light is still on even after it’s shut off.
- Odd Activity – This can consist of distortions on your screen or even application being installed by itself.
 Call Interference – During phone calls there may be unexplained background noises, clicks, echoes, or static.
Call Interference – During phone calls there may be unexplained background noises, clicks, echoes, or static.- Data Use Increase – Drastic increases in data without a good explanation. Not sure how to tell… “Look at how much data your device is using, and see if there’s a big discrepancy between how much data you’re using, and how much your applications are using. Any difference involving 10MB or more might be a sign of ‘parasitic activity’” – DarkReading
- Low Battery and High Temperatures – Both paired together could be caused by a constantly running application tapping into your phone.
- Coded Text Messages – This is a strong sign your phone has been tapped
The 2015 Internet Security Threat Report from Symantec showed that data breaches surged by 23 percent last year, and nearly a million new pieces of malware (“malicious software”) were created per day. Almost 1 in 5 Android apps available last year were actually malware in disguise, says the same report. The more popular smartphones and downloading apps become, the more popular malware and other viruses are becoming as well. Be smart and keep your smartphone safe from these bugs.
How do you prevent your phone from getting infected?
Strong Lockscreens – The stronger your passcode to get your phone unlocked the more secure your phone is.
- Not sure how to set up a lockscreen…

- Android Lockscreen Setup
- iPhone Lockscreen Setup
- Top lockscreen apps…
Get A Security Program – Ultimately the best ones would include anti-virus, anti-malware, anti-spam, anti-phishing defense, and a firewall.
- Android Antivirus Apps
- iOS Antivirus Apps
Update Your OS – There is a reason they come out with updates and new operating systems. The longer you put off updating your phone, the more susceptible it is.
Use Trustworthy Companies – If you are downloading applications, ringtones, wallpapers, etc. always use trustworthy companies, take the time to read reviews too.
Avoid Suspicious Websites – If you feel suspicious there’s good reason.
- How do you tell a website is unsafe? (SpyRambly)
- Poor layout
- Bright and flashing buttons, banners, or images
- Constant pressure to download
- Manipulation used to click on unsafe links
Turn Off Bluetooth – When you are not using the Bluetooth, have it set to off
Take Out Battery – Although this make not as practical for frequent users but if you know you won’t be using your phone for a while, take out the battery.
Don’t Jailbreak – If you jailbreak your phone this leaves you much more susceptible to viruses.
Use the Two Step Verification – This is an extra security step.
- Not sure how to set it up…
- Google 2-Step Verification
- Apple 2-Step Verification
Encrypt Sensitive Information – Another extra security step to help keep you safe.
- How do you encrypt?
 TIP: Backup Your Information – No matter how hard you try to prevent it there is still a chance you will get infected. It is always a good idea to have your information backed up in case you have to wipe your phone clean.
TIP: Backup Your Information – No matter how hard you try to prevent it there is still a chance you will get infected. It is always a good idea to have your information backed up in case you have to wipe your phone clean.
- How do you backup your phone?
- Android Backups
- iPhone Backups
My phone is infected! What do I do now?
- Take out your SIM card at first sign of malware
- Restart your phone in ‘Safe Mode’
 Depending on the severity of the infection:
Depending on the severity of the infection:
- Uninstall the application or remove file/software from where the malware came from
- Reset to factory settings – you can do this on your own or take it to your provider (This is where backing your information up is important)
- Run an anti-virus scan
Court Notice Scam
“Court Notice” Mail Scam
 One of the more alarming new scams going around involves court notice emails prompting the user to open an attachment.
One of the more alarming new scams going around involves court notice emails prompting the user to open an attachment.
Lets take a look at the especially scary-sounding court notice scam to learn how to identify it, and avoid becoming a victim to this and other email scams like it.
It Says I Need To Go To Court!
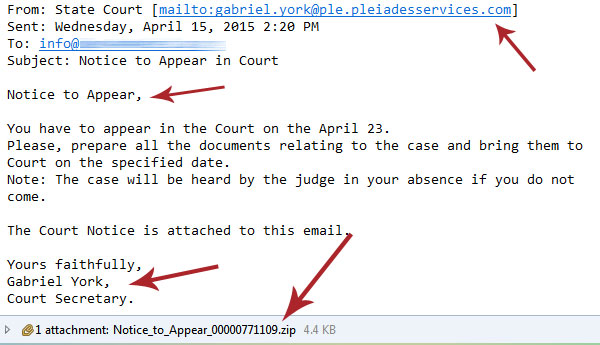
This piece of spam arrived in a client’s email box to inform him that he had to appear in court.
The email did not explain why. It didn’t include any information on how to contact the court. It didn’t even mention a name.
It did, however, have an attachment.
When the attachment was opened the antivirus software kicked into gear, giving a malware warning.
How You Can Tell This is Spam
There are a few things to watch for in suspicious emails; this one avoids some, but hits on others.
- What Is it? Would you be receiving this as an email? A notice to appear in court is a formal affair. You would receive a letter by mail, not just an unclear email with no name. And you generally opt in to receiving important correspondence through email anyway.
- The Recipient: In this case the email is being sent to an info@ email that is not addressed to any one person.
- The Sender: Check the sender’s address to see if it is consistent with what you would expect from a court email. In this case it is ambiguous; in some, it’s an obvious fake.
- Grammar: Are there typos, or is grammar terrible? In this case there are no typos and grammar is solid, but a lot of spam can be identified by grammar.
- The Attachment: The attachment is the big warning. In most notices a word document would suffice (even if they are not inherently safe). In this case a zip file is sent. Zip files can easily contain EXE files, programs that can put malicious software on your computer.
- Antivirus: Clicking on the file triggered the antivirus and told the user that malware was trying to infect his computer. He was lucky – software may not always catch everything, and opening attachments is not advisable.
[alertbox color=”yellow”]Always have some form of antivirus software on your computer, and make sure it’s automatically updating. [/alertbox][space10]
 What can you do?
What can you do?
- Mark Them As Spam: This may teach the email client that emails of this sort are no good. In the future they might go straight to the spam box.
- Antivirus: Everyone should have some kind of antivirus software on their computer these days, with no exceptions. Windows 8 comes with its own antivirus software, and anything older has plenty of options. Make sure your computer has one, and that it’s automatically updating.
- Call the Agency: If there is no agency, like this email? Odds are pretty good it’s a spoof.
- Don’t Respond: Responding to the email just tells the sender that your email address is ‘live’ and can be put on other spam lists.
Be aware of similar email and phishing scams:
- FedEx/Shipping Scam – These inform you that there is a problem with your delivery and that your shipping label is attached. The label is a zip file. Don’t open the zip file. If you are expecting something go to your original tracking mail or the website. If you aren’t waiting on a package? Disregard.
- Friends in Distress – These scams may use a friend’s email or name to alarm you into thinking they are stranded somewhere and need help or money. Contact your friend directly to see if this is a scam.
- Spear Phishing – This is one of the phishing scams that may target your organization or you as an individual and appear to be from a trusted source. It uses your name and sounds personal. The trick here is to be careful of your private info, and if something sounds suspicious, contact the presumed sender to confirm.
Email scams are not going away. The more you educate yourself on how to spot them and what to do about them, the less likely you’ll be to fall for them when distressed and alarmed.
[alertbox] Want to know more about email and internet scams? Visit our articles on Paypal Phishing, Domain Slamming, Ransomware, Energy Bill Service Scams, and Facebook Password Scams. [/alertbox]
My Computer Files are Being Held for Ransom!
 Ransomware
Ransomware
Ransomware, often going by the specific name CryptoLocker or Cryptowall, is a form of malware that, when installed on your computer, encrypts your files and locks them with a key. It then demands a ransom in digital currency within a set amount of time, or the key will be deleted and the files will be inaccessible.
How do you get it Ransomware?
The most common way to become infected with ransomware is to download it inadvertently. When downloaded, the malware sets to work.
Ransomware is often installed by:
- Opening email attachments
- Clicking on banner ads
Why doesn’t my antivirus protection catch Ransomware?
Generally speaking, Ransomware is sneaky malware that slips in to your computer because you have inadvertently installed it. You’ve gone ahead and told your computer to install things, and the malware takes advantage.
[pullquote cite=”- George W.”]”I got an alarmed call from my grandma. She likes playing online games, and clicked on an ad promising her more coins for her game, and moments later she had a message across her screen telling her that her computer had been infected, and that she had to call a number and pay to get the problem resolved. Fortunately, my grandma didn’t have many files on her computer. We wiped the hard drive and reinstalled Windows. But if she’d had important paperwork or photos without any backups, she would have been in a lot of trouble.”[/pullquote][space10]
Who is the biggest target?
This malware can attack anyone, but it causes the most damage to businesses, as they have more valuable data that is not easily replaced. Ransomware is designed to get money by holding your data for ransom.
How do I avoid Ransomware?
Don’t click on things you shouldn’t, or open unexpected files. Functionally we all know this isn’t always the case, however, and sometimes files slip through because they are deceptive.
If you become infected with Ransomware:
- Have secondary backups of important files that are not updated real time, this way, if you need to roll back, you have something unattached that is not infected.
- Unhook your computer from the internet RIGHT AWAY. All files may not have a chance to be encrypted.
[alertbox color=”red” icon=”delete” hide=”0″]
A few companies claim to be able to undo the damage, or have released the keys to unlock encrypted data, but this has not been guaranteed to work in all cases, especially since criminals update the software all the time.
[/alertbox] [space5]
My files are being held for ransom!
If you do find that you have this software, you have two options:
- Pay up and hope the keys they supply you to unlock your data works as indicated. This is risky as it encourages criminals to continue the scam, and since they ARE untrusted people, nothing is guaranteed.
- Wipe computer clean and restore from backup.
Hacking and computer exploits have become more sophisticated and with more businesses online, the risk is real. Precautions and backups are the most surefire way to avoid the worst of damage from hackers, criminals and emergencies when your files are being held for ransom. For more information on internet security, visit our blog at Appletree Mediaworks, LLC.
For more information visit:
– http://www.businessnewsdaily.com/6657-ransomware-cryptolocker-protection.html
– https://www.foolishit.com/cryptoprevent-malware-prevention/
– http://www.welivesecurity.com/2013/12/12/11-things-you-can-do-to-protect-against-ransomware-including-cryptolocker/
– https://blog.malwarebytes.org/intelligence/2013/10/cryptolocker-ransomware-what-you-need-to-know/
How to Clean Up Your Computer
 Have you ever noticed your computer starting to run slower for no apparent reason? Does Windows seem to take a while to boot up when it has no business crawling along like that? Has your browser become bogged down with a half-dozen tool bars of dubious origin?
Have you ever noticed your computer starting to run slower for no apparent reason? Does Windows seem to take a while to boot up when it has no business crawling along like that? Has your browser become bogged down with a half-dozen tool bars of dubious origin?
Keeping your computer cleaned up is not always something that comes to mind, but a little regular maintenance will keep it running smoothly.
Virus Protection
All PCs should have some form of virus protection and most, in fact, do. Newly purchased computers might come with McAfee or Norton Antivirus, but these programs often have special features that are free for a limited time, but then proceed to nag you once they expire. Fortunately, there are several free and reliable antivirus programs available, including Avast and AVG. Microsoft also distributes Microsoft Essentials for free, which runs quietly and discreetly in the background.
Whatever you decide to do, make sure to uninstall any antivirus program you may already have before installing another – doubling up on antivirus software can create more problems than it prevents. If your computer is sluggish, check to make sure that you have only one antivirus program installed.
Your job is to make sure your antivirus is running, up to date, and scheduled to scan regularly.
Popup Blockers
Most browsers come with popup blockers, but malware often finds its way in through ads, so installing an add-on such as Adblock Plus can reduce the likelihood of malicious advertising infecting your computer. However, do not go overboard with the addons. Occasionally, legitimate plugins will be purchased and compromised by shifty companies that use them to inject malware into your computer. Consider each plugin wisely, and uninstall them when you don’t need them anymore.
Anti-Malware Software
I know what you’re thinking – what is this and what about the antivirus software? The problem with malicious programs is that there are many kinds, and they evolve and change, so that old protection software may not catch everything. Further, there are many kinds – from tracking spyware to software that hijacks your browser. While doubling up on antivirus software may do more harm than good, having secondary anti-malware software does help – this is where MalwareBytes comes in.
MalwareBytes should be updated and run on a regular basis. It digs out things that your antivirus might not have caught, and then may ask to reset your computer to further dislodge any bad software it finds. Let it do its job – it’s one of the better pieces of software out there.
Taking Out the Trash
Another handy piece of software for keeping your computer running smoothly, CCleaner will get rid of old temporary files, history files, clean up the remains of uninstalled software, and much more. It also has an option to uninstall software you don’t need any more and makes it easy to deactivate programs that run in the background, eating up valuable system resources.
Deactivating software that runs in the background when your computer first starts up will speed up the process drastically. Be careful with this tool because you might need unexpected things (your antivirus software, some drivers and video software) – but do you really need parts of Adobe Acrobat checking for updates every time you turn on the computer? Probably not.
Driver Updates
Speaking of updates – drivers rarely bother you, but they can benefit from occasional updates as well. Updating your hardware drivers can boost computer performance and keep things running smoothly, especially in an older computer. Slimdrivers is a free program that will scan your computer and detect when drivers need updating. It will even download the correct drivers and initiate the update process without having to leave the program.
Software Updates
A lot of your software will update automatically, but it is still a good idea to keep track of what’s been updated, and manually update what is behind. Windows, Firefox, Chrome, and IE can be checked for updates. Flash, Acrobat, and Java will prompt you for updates, quite frequently. Go ahead and update them as they come in. Updates often patch security holes.
Defrag, Defrag, Defrag
When you’re all done, defrag that thing. Defrag is part of Windows (though you can get better or more visually appealing versions of the software). It crunches together fragmented files, giving your computer a little added boost. If you’re using a Mac, fire up Disk Utility and Verify and Repair your disk permissions.
Dust That Thing
If you’re feeling bold and don’t mind cracking your desktop computer open, get some canned air and dust out the machine. You’ll be amazed (and maybe a little scared) at just how much dust gathers on electronics – dust gums up the works and holds in heat that your computer does not need.
Be smart about it though – if your computer is under warranty you may not want to go meddling around inside. Warranties aside, always make sure the computer is unplugged before prying open the case. It also helps to ground yourself on something so you don’t inadvertently shock some delicate computer chip with a static charge from your finger. Also, remember that you’re messing with delicate electronic equipment. You don’t want to bring an industrial shop vac to the machine (yes, sadly, this has been done). It is possible to knock things loose if you bump or nudge cards or cords, so make sure they are seated properly before closing everything back up.
While you’re at it, take a look at that keyboard. It may need a little more than canned air.
Wrapping It All Up
Once everything is taken care of, it never hurts to create a backup or restore point, in case something malicious does find its way onto your computer. Along with good practices for keeping nuisance programs off your computer (I’m looking at you, toolbars and ‘free games’), regularly cleaning your computer can keep it running smoothly for years.






