Windows 7 End of Life Approaches
 The Windows 7 end of life date is quickly approaching. If you’re still behind, you should mark your calendar. Microsoft is ending extended support for this popular OS on January 14, 2020. After this date, they will stop patching security holes. Users who do not upgrade will be exposed to an ever increasing number of online threats. If you are still using Windows 7, what should you do to prepare? Read our simple guide below to find out!
The Windows 7 end of life date is quickly approaching. If you’re still behind, you should mark your calendar. Microsoft is ending extended support for this popular OS on January 14, 2020. After this date, they will stop patching security holes. Users who do not upgrade will be exposed to an ever increasing number of online threats. If you are still using Windows 7, what should you do to prepare? Read our simple guide below to find out!
Keep applying patches – especially now!
Although we always recommend updating your software, it is especially important to apply updates frequently through July of 2019. This is because Microsoft will be changing the way it supplies patches to its users. If updates were not applied leading up to July, Microsoft will stop supplying security updates altogether. This would potentially open your system up to attack a full 6 months before the official sunset date.
Upgrade to Windows 10
Since Windows 7 will no longer be viable after January 14, it is important to upgrade your operating system before that crucial date. Although there are many operating systems to choose from (we recommend Linux if you have the know-how), for most the obvious choice will be Windows 10. This offers the easiest transition since in most cases you do not need to convert any files. Also, your favorite programs will continue working without any interruption. Follow these steps to upgrade from Windows 7 to 10.
- Make sure your device can support Windows 10. The latest version of Windows requires a 1GHz or faster processor, 1GB of RAM, and 32GB of hard drive space. Read the full requirements here and make sure your system or device will work. If not, you may need to upgrade your hardware as well.
- Purchase Windows 10. The free update period expired back in 2016. Although some people have reported that they are still able to upgrade for free, the rest will need to purchase a new Windows 10 product key from microsoft.com.
- Create a full backup. Although this upgrade process is usually seamless, it can sometimes fail and you may lose data. To avoid any problems, it is best to make a full backup of your system so that you can roll back if necessary. Windows 7 comes with a System Image Backup tool to make this process easier.
- Uninstall unnecessary software. Windows 10 will do its best to migrate all of your programs. However, some outdated or uncommon programs may cause problems. To minimize this possibility, we recommend using the Programs & Features tool to remove any software that you no longer need.
- Download and install Windows 10. Finally, download the Windows 10 Disc Image (ISO File) tool. Once downloaded, run the executable and follow the on-screen instructions. When prompted, select “Upgrade this PC now” and later on, be sure to select the “Keep personal files and apps” option. During this process, you will be prompted to enter your Windows 10 product key. Use the key you purchased from microsoft.com.
An Alternative
Not happy with Windows 10? Is your device a little too old to handle the latest system requirements from Microsoft? Fortunately, Linux still runs on most anything and is available for free. There may be a bit of a learning curve, but popular distributions such as Ubuntu have made it much more user-friendly over the years.
If you decide to install Linux, be sure and make a full backup of all your essential files and documents on a thumb drive or external disc before making the jump. Remember that most Windows programs do not work natively in Linux, although there are workarounds and Linux versions available for some of them. Overall, prepare to re-learn some tasks and to spend time searching for alternative programs. This option is for moderate-to-advanced users who aren’t trying to do anything essential or time sensitive during the transition.
Can’t upgrade it? Recycle it!
If all this seems a little daunting, you may be better off just buying a new system with a more recent operating system already installed. In today’s market, low- to mid-level desktops are very affordable, especially when you subtract the cost of a Windows 10 license. If you go this route, a simple thumb drive can be used to transfer files and documents from your old system to the new.
Once all of your documents have been transferred, read our guide on recycling to learn how you can safely recycle your old system without compromising on security. Remember that old systems and devices contain batteries (whether you can see them or not), so it is important to discard them properly so they don’t leak toxic chemicals into the water supply.
How to Recycle Technology Responsibly (without compromising your security)
 Did you ever wonder how to recycle technology responsibly? Earth Day is a good time to think about how our daily lives affect the planet we call home. If you’re like us, staying updated with the latest gadgets often results in boxes full of outdated tech. With Spring in the air, it can be tempting to just toss all that tech in a fit of Spring cleaning fever, but don’t be too hasty!
Did you ever wonder how to recycle technology responsibly? Earth Day is a good time to think about how our daily lives affect the planet we call home. If you’re like us, staying updated with the latest gadgets often results in boxes full of outdated tech. With Spring in the air, it can be tempting to just toss all that tech in a fit of Spring cleaning fever, but don’t be too hasty!
Did you know that old computers and gadgets often contain toxic chemicals that seep into the ground from landfills? What about the possibility of scavengers harvesting sensitive financial data from one of your tossed PCs? Never fear, there are ways to recycle technology responsibly without hurting the earth (and without compromising your sense of security). Follow these simple steps and you’ll be well on your way to a cleaner home – and a healthier planet!
-
Avoid throwing batteries in the trash
Batteries contain toxic chemicals which leak into the soil from landfills. These chemicals eventually wash down into our watershed and can get into the water supply. This affects everybody! Many grocery and department stores now have battery recycling drop-offs where old batteries can be recycled the safe way. This goes for rechargeable batteries as well. Not sure where to drop them off? Lowe’s hardware started a rechargeable battery recycling program in 2004.
Also, keep in mind that most hardware (such as laptops, PCs, game consoles, etc) have batteries embedded inside. These should also be removed and recycled separately before recycling the rest of the hardware. If you’re not sure how to remove the battery from your device, searching Google for your device name and “remove battery” will usually provide step-by-step instructions.
-
Wipe your data first!
Recycling a computer or device that holds personal or financial data? Be sure and clean out any internal storage drives and thumb drives completely before hauling them away. Format these drives using a full wipe option (erase everything). Do not select the “quick wipe” options since those do not fully remove data from the disk. Many programs even offer “multi-pass” wiping for added security, but you really only need to wipe the data once. Multi-pass grew in popularity due to an urban legend and now only serves to ease the paranoia of the uninformed.
-
Donate your tech if possible
If your product is still functioning and might still have some use, consider donating it to a reputable reuse organization. These organizations will refurbish products and donate them to schools and charities wherever needs arise. A couple of good ones include The National Cristina Foundation and World Computer Exchange. Some local robotics teams and HAM radio clubs also seek laptops and monitors for their organizations, seek them out and see if they would like any of your items.
-
Take your computers to a responsible e-Steward in your state
If your product is too old or broken down to donate, the next best thing is to recycle it. Although any recycling program is better than none, the best option is to use one which takes part in the “e-Steward” network. These follow high standards to ensure that nothing goes to waste or ends up shipped overseas to landfills in developing nations. E-Stewards are located all around America – click here to find one near you.
-
When all else fails…
If you cannot locate a technology recycling program near you, many big-box retailers offer their own programs. Staples and Best Buy, for example, will be more than happy to recycle your old devices and computers for you. If you don’t have one of these stores nearby, most manufacturers also offer their own free recycling programs which allow you to ship them the hardware from anywhere. Contact each manufacturer directly to find out how to take part. The manufacturer’s website often contains detailed information as well.
-
What about this smart phone?
After wiping your data clean and resetting your phone to factory default settings, cell phones can be shipped to one of several nationwide recycling programs which specialize in providing this service. Call2Recycle is one such well known and respected program. Best Buy also maintains cell phone drop-off recycling kiosks near the front of their retail locations.
How Does Facebook Know Everything About Me?
You may have noticed Facebook and its subsidiaries (Instagram, Messenger, etc.) seem to know exactly what you’re thinking and saying. It’s almost like Facebook is listening in on our private lives. There are a few resources that Facebook uses to achieve this level of creepiness.
Facebook Has Its Sources
Privacy International conducted a report in December 2018 on apps that instantly send information to Facebook whether you’re logged in or even have an account at all. Research in the past has shown that up to 42.55% of free apps on the Google Play store alone share data with Facebook.
The report addresses how app developers use Facebook’s software development kit (SDK) to track and transmit your information to them. 34 apps, all with between 10 and 500 million installs each, were analyzed for this report. All were found to transmit data to Facebook. 61% of the apps send information as soon as they’re launched. This data is sent to Facebook along with a unique Google Advertising ID which can be used to link user behavior between different apps to build an in-depth profile. All of the info sent from the apps you use combined with your internet browsing habits can flesh out an extremely detailed profile.
Permission Granted
Let’s be honest, most of us have taken at least one of those “harmless” Facebook quizzes before. You see your friends and family sharing their results constantly. It plagues your time line. But is it just the results to the quiz that are being shared, strictly with friends? You would think so – and hope so.
NameTests is a huge Facebook quiz platform. It was found that up to 120 million people’s information was being exposed due to a security flaw. This was the case for years. Information like names, birth dates, photos, and statuses were all exposed. This flaw is demonstrated here. A random website linked to NameTests with an access token from Facebook would be able to pull information for up to two months, even after the user deleted NameTests from their profile.
Turn Off Facebook Permissions
To protect yourself as much as possible, it is probably smart to clean up your Facebook permissions periodically. This will help you know exactly what each app and game you use with Facebook has permission to do.
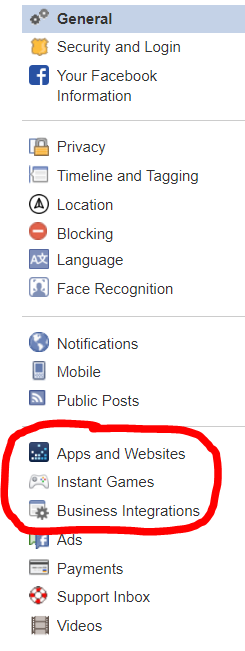
- Next to the notification and quick help button in the top right corner of Facebook, hit the dropdown and click Settings (second from the bottom).

- On the sidebar to the left, the last section contains Apps and Websites, Instant Games, and Business Integration. Click on each and complete steps 3 and 4 for all of them.
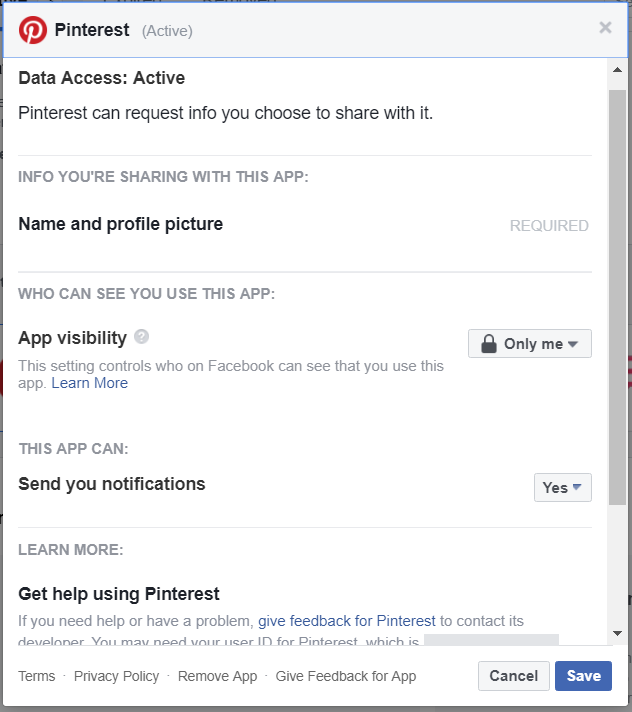
- Go through all the apps and websites displayed and get rid of the ones you don’t use.

- Click View and edit to review what the apps you use have permission to do.

Another thing to look out for is permissions that mobile apps ask for. Most people don’t think twice before giving the OK to install an app on their phone. A lot of apps these days will randomly request access to your microphone, camera, contacts, and more when it’s not really necessary. Usually, you will be able to turn some of those permissions off. Google Play Store users have to be especially careful. This is because it is easier for a malicious app to get listed on Google’s Play Store than it is with Apple’s App Store.
Should You Leave Facebook?
With everything we’ve talked about here AND last year’s security fiasco, it is completely reasonable to contemplate this. Facebook has always been a fantastic tool for keeping in touch with friends and family. It’s useful when looking for old friends or trying to read the latest update from your favorite restaurant. Businesses can connect and networking has never been easier than it is now. The cons are the security risks. Can we trust Facebook to keep our information private? Can we trust Facebook to tell us when there is a security issue? For some people, these problems are huge. If you’re looking to leave Facebook, you have a couple of options.
How to Deactivate Your Facebook Profile
This option is for those who may contemplate returning to the site someday. Deactivating will hide your profile entirely, apart from your name in your friends’ friend lists and previous messages that you’ve sent to friends. You can reactivate just by logging back in.
To deactivate your account, click this link and select the FIRST option that says “Deactivate Account”. You’ll be prompted to type in your password to continue.
How to Delete Your Facebook Profile
Before you go through with deleting your account, you might want to download your information. There is no getting it back after you click that final button. Also, any apps or websites you log into with Facebook may also be deleted. Change your login information on those sites first, if possible.
When you’re ready to proceed, Click this link, and at the bottom, click Delete Account. Facebook gives you a few day grace period to log back in and cancel your deletion. After that, they say it can take up to 3 months to fully erase your information from Facebook servers, although you’re completely untraceable on the platform.
In the end, we can’t be sure exactly what is happening to our information beyond deletion since this only removes your data from Facebook’s servers and not 3rd parties which may have already saved it off site. The best thing to do is to be selective about what you share, what you download and what information you hand over to 3rd party websites and apps.
Web Designer Vs. Web Developer
You may have heard somebody refer to themselves as either a web developer or a web designer (or even both). What is the difference? What does a developer do that a designer doesn’t, and vice versa?
Designer
We’re going to start here, since the design process comes before developing.
Web designers work in programs such as Adobe Photoshop to create the look of the website. They figure out how things should be laid out, and they create an image of what the final product should look like. Now-a-days, designers usually have to design a mobile version of a website as well as the desktop version. Over 50% of web browsing in done on a mobile device.
They figure out how things should be laid out, and they create an image of what the final product should look like. Now-a-days, designers usually have to design a mobile version of a website as well as the desktop version. Over 50% of web browsing in done on a mobile device.
This is a much more creative process than developing, and people with this job usually have a good eye for detail and like to create.
Front End Developer
The developer brings the design to life with “code”.
Developers have to make the design fully responsive. Responsiveness is how well the website adapts to different screen sizes (ex. monitor screen vs iPhone screen).
On top of that, developers have the responsiblity of setting fonts and positioning things on the site. They have to link all the pages together to ensure that when you click a link, it goes to the correct place.
This is a more technical process than designing. The developer focuses less on making the website look pretty, and more on fuctionality. They use various web languages to piece together a fully functioning website. HTML, CSS, and Javascript are usually used to bring a design to life.
Conclusion
It takes both a developer and a designer (or someone who can do both) to create a good looking and fully responsive website. Both roles are just as important to each other, as you can’t have one without the other.
Common Email Scams to Lookout For
As technology progresses, we’re finding new ways to do things better. One downside of this is, that also means scammers are finding new ways to do things better. Here is some spam to look out for.
Sextortion Email Scam
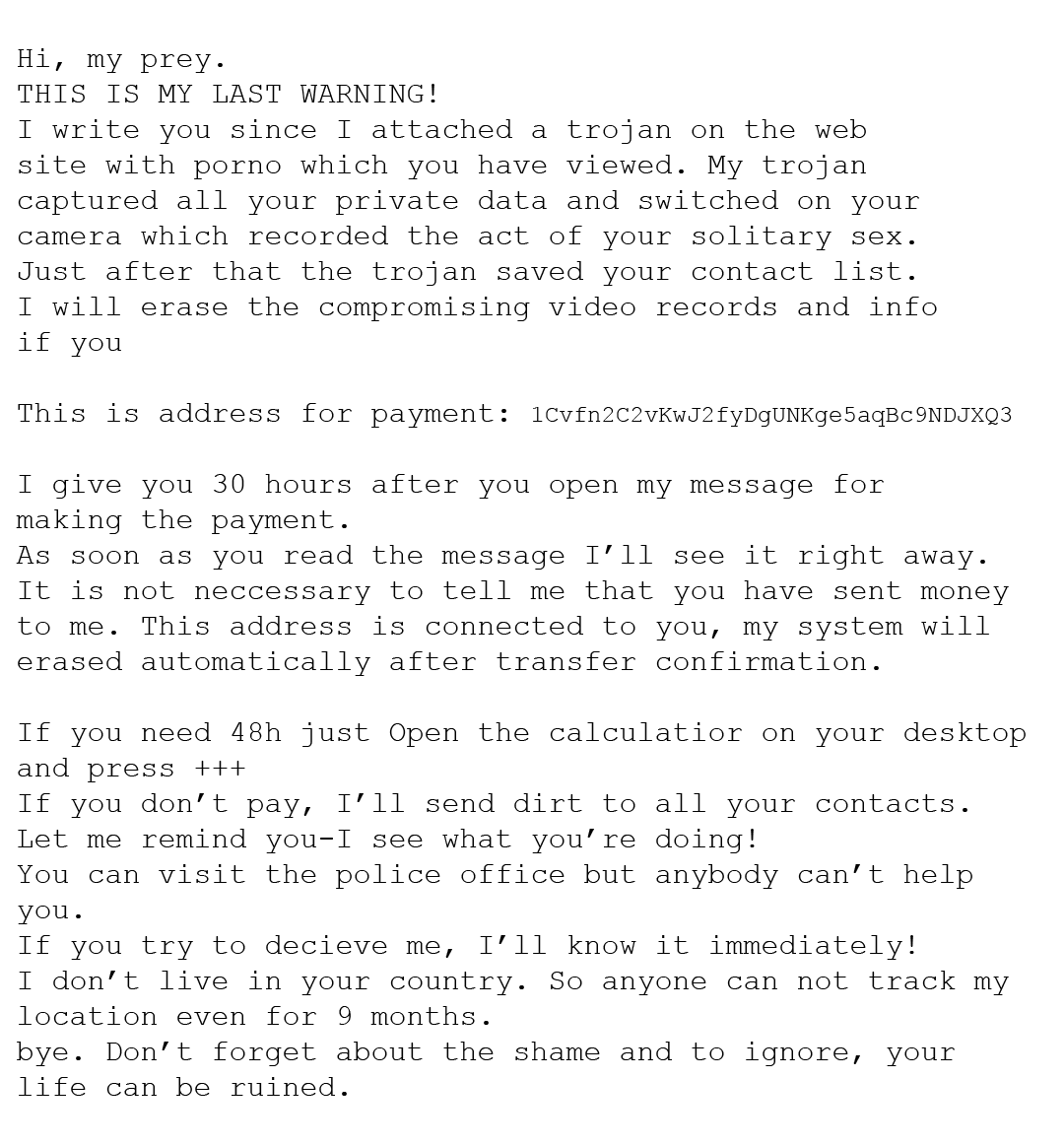
One scam that was popular last year had the scammer proclaiming that an amount of money (usually ranging from $600-$3000) in Bitcoin is enough to destroy video that they supposedly have of you. The scammer sometimes even supplies a password of yours within the email. They then threaten to release webcam video of you viewing pornography to your family, friends, and colleges. At this point, you may be nervous.
Here is an example of this scam:
What should you do?
If you’re still using the password they put in the email, you should certainly change it. Do not respond to scammers ever, just report the email and delete it instead.
Various Phishing Scams
If you haven’t heard of phishing yet, you’re probably at a higher risk of falling for it.
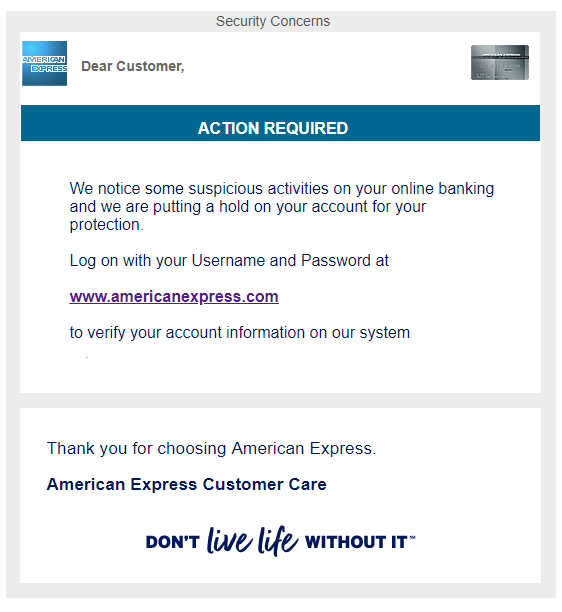
Phishing is a “bait” scam method (hence the relation to “fishing”) where scammers will have an imitation site that strongly resembles the real thing. It takes is a split second for them to get you. From adding a malicious extension to typing in billing information to a “failed transaction” from a fake Amazon, these scammers will pretend to be pretty much anything to get your money from you.
Here is an example of phishing (extremely authentic looking):
What should you do?
If you get an email that contains an external link, don’t click it right away.
– Double check who the sender is. Sometimes this can be a giveaway. Don’t recognize the email? Doesn’t look real? Don’t click the link.
– Use a website like https://www.urlvoid.com/ and paste the link that was provided. It will tell you the destination of the link. If anything..phishy.. comes up, don’t follow through. The link given to you in the email should be the same website as the destination.
– If nothing else, it’s better to be on the safer side. Never provide any information to a link you’re at all suspicious about.
Lottery Scams
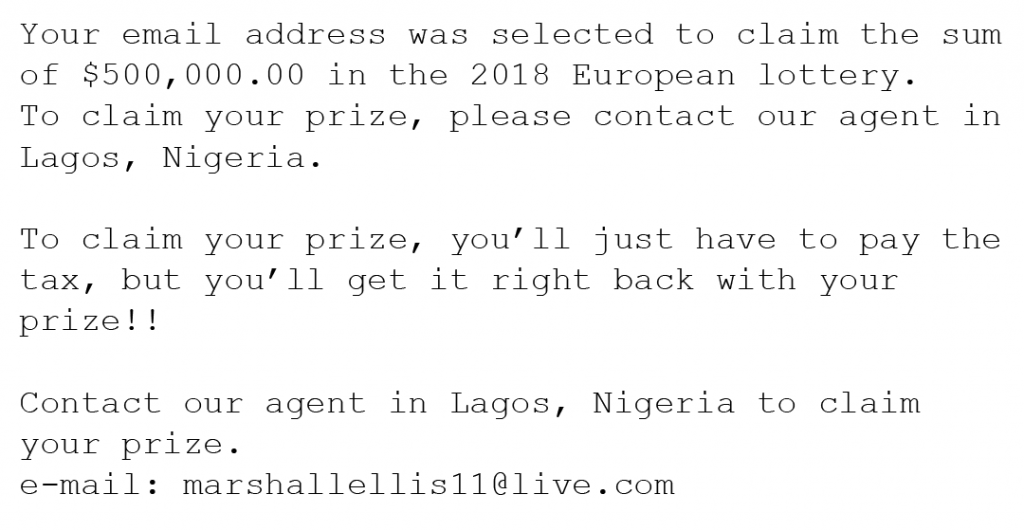
These are emails or texts from a fake lottery company saying that you won a lot of money or very valuable prizes out of nowhere. They will tell you that there are fees and/or taxes that have to be paid before your prize can be released to you.
Here is an example of a lottery scam:
What should you do?
Simply report and delete the email. Remember that you can’t win something you didn’t enter to win.
Hallmark eCard Scam
This scam would be an example of phishing, and it comes and goes pretty frequently. It’s a fake Hallmark email that is extremely real looking. If you click the link within the email to open the supposed eCard sent to you by a “friend”, a virus will launch and install malware onto your computer.
These emails will look just like Hallmark eCards.
What should you do?
Don’t click hyperlinks without knowing the destination. Attempt to verify the eCard on Hallmark’s website directly instead of clicking the link. Report and delete any unauthentic emails.
Hitman Scam
This scam would be terrifying for any victim unfamiliar with how internet scams work. Scammers here give you the option to live or die if you do not pay up. They claim a “friend” of yours gave them a lot of money to end your life, but they are giving you a chance to save it for a price ranging anywhere from $1000-$100,000.
Here is an example of the hitman scam: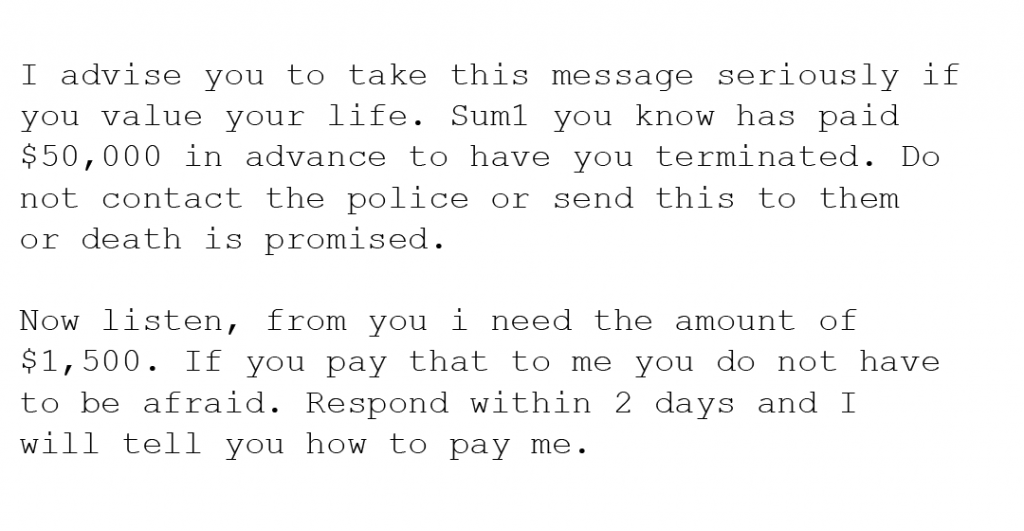
What should you do?
If you notice an email like this in your inbox, delete it without even opening it. Read below to learn where to report scams.
Protection
There are ways to keep yourself protected from scams. The most important thing is to know. Don’t believe everything that comes through your inbox and do your research.
How scammers get your information?
The scammers likely retrieved your email (and possibly an old or current password) from a database of leaked information that was obtained during a breach. To check and see if your email is associated with any data breaches, head to haveibeenpwned. You can type your email in and it will tell you if it’s ever been compromised. Also during which exact breach. Be sure to change your password if you haven’t since the last breach you were involved in.
What to do with spam
If obvious spam ever does come through your inbox, just delete it without opening it. A lot of scam emails contain what is commonly called a “pixel”. This acts as a read receipt. It will tell the scammer that the email was opened. It can also supply them with other information, such as:
- Browser you’re using
- Operating system
- IP Address
- The exact time the email was opened
Thankfully for us, there is a program that can tell us whether or not an email is being tracked. It’s called Ugly Email. It makes an eyeball appear next to the subject of any email that is being tracked. The slight downsides of this are that it’s only for Gmail and is only out for Chrome and Firefox at the moment. If you fall under the criteria, this can be a really useful tool.
Report Scams
You can help eliminate a popular scam by not only reporting it to your email provider, but to the IC3 as well. They are a branch of the FBI that deals with internet crime. Make sure to file a complaint for scams you may get – especially reappearing ones.