08/01/2019 E-Newsletter: FaceApp – stealing your info? What is SSL and why do I need it?
Extremely important! Learn how to keep your computers safe from junk and viruses. Also, who gains access to your accounts after you pass away? Read this to learn how that works. More scams coming to your inbox. Don’t fall for fake debt collectors. Click here to read all this and more!Read More
Everything You Need to Know About Your Google Business Listing
Google My Business is the tool that allows you to directly edit your business’s information on Google. On top of that, it is a good place to view insights and reviews too. If you’re a business owner and need to claim your business, add your business to Google, or remove spam/fake reviews and customer photos, read on.Read More
07/11/2019 E-Newsletter: Slow computer? Let’s fix that. Fake debt collector emails
Extremely important! Learn how to keep your computers safe from junk and viruses. Also, who gains access to your accounts after you pass away? Read this to learn how that works. More scams coming to your inbox. Don’t fall for fake debt collectors. Click here to read all this and more!Read More
Why You Need an SSL Certificate on Your Website
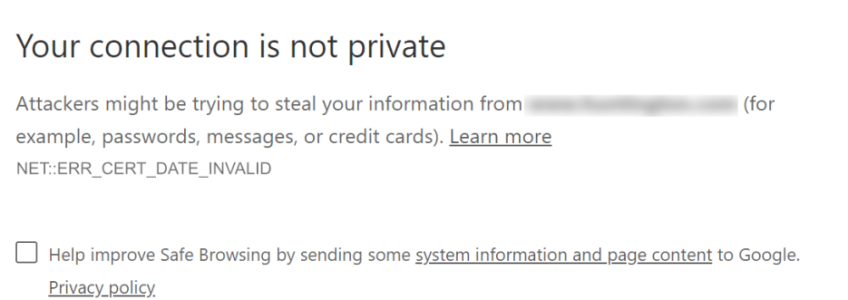
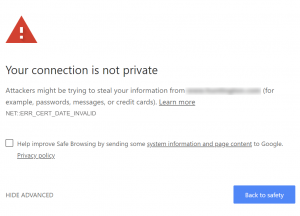 Have you ever visited a website and been greeted by a warning stating that the site is “Not Secure” or something similar? It is definitely off-putting to visitors when this happens. If you are a site owner and notice your site doing this, it is actually pretty easy to fix. All you need to do is install an SSL certificate.
Have you ever visited a website and been greeted by a warning stating that the site is “Not Secure” or something similar? It is definitely off-putting to visitors when this happens. If you are a site owner and notice your site doing this, it is actually pretty easy to fix. All you need to do is install an SSL certificate.
What is SSL?
SSL stands for “secure sockets layer”. This essential technology encrypts data as it moves between a web server and browser. In other words, it stands between you and the rest of the internet, 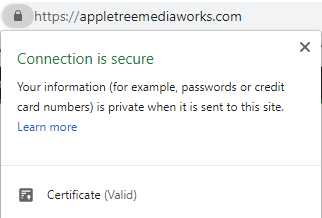 jumbling whatever information you send (such as usernames, passwords, credit card info, etc) into nonsense that can only be decrypted by a special “private key” held by the intended recipient. This protects you from hackers who could otherwise intercept your info while it is in transit. You’ll know you’re on a site with an SSL certificate if you see a padlock to the left of the URL in the address bar.
jumbling whatever information you send (such as usernames, passwords, credit card info, etc) into nonsense that can only be decrypted by a special “private key” held by the intended recipient. This protects you from hackers who could otherwise intercept your info while it is in transit. You’ll know you’re on a site with an SSL certificate if you see a padlock to the left of the URL in the address bar.
What if My Site Doesn’t Collect Personal Information?
Google encourages every site to obtain an SSL certificate. As a reward, your website gets a boost in search ranking. By not having one, you ultimately rank worse regardless of your data collection policy. If you’re running a small business, building a good Google ranking is essential to help bring in customers. This reason alone is good enough to justify the effort – you can outrank your competitors!
In addition to that, not having an SSL certificate causes some browsers to display a warning. Google Chrome, specifically, shows a “Not Secure” label (as mentioned earlier). This can be alarming to potential visitors, redirecting them away before they even land on your site. If enough visitors “bounce” because of this, it can ruin your website’s performance and eventually even harm your company’s credibility!
Keep Your Information Safe
If you manage your website using a content management system like WordPress, your administrative login credentials could become compromised if your site does not have an SSL certificate. Without it, your username and password are sent as plain text over the internet. Credentials sent this way can easily be picked up by hackers. Another way to combat unauthorized logins is by using two-step verification. Enable that whenever it is available.
Stay Cautious
Sometimes even phishing & scam websites are able to obtain legitimate SSL certificates. Just seeing a padlock in the corner does not necessarily mean you should trust the site with your personal information. Usually, you only have to worry about these types of scams coming through your email, so make sure to keep your guard up and know what to look out for.
Now that you know how important SSL certificates can be for you and your customers, help keep your website visitors safe and comfortable by installing one as soon as possible. This will boost your reputation as well as your organic search rankings over time. Not sure how to install SSL yourself? The experts here at Appletree would be happy to assist – we do this all the time! Don’t hesitate to drop us a line and let us know how we can help.
Subscribe to the free Appletree MediaWorks E-Newsletter to get bi-weekly tech tips, scam notices and more, straight to your email!
06/27/2019 E-Newsletter: Business Social Media Reputations and Free Wi-Fi Worries
Wait! Know the risks before connecting to public Wi-Fi. Get an email asking you to update your 1&1 Ionos account information? We did too, luckily we were able to tell it was a SCAM. Lastly, we helped garner hundreds of job applications easily. You can too!Read More
Social Media After Death
 As of this year, at least 2.34 billion people worldwide are social media users. In the United States alone, 79% of people have a social media profile. Something we don’t really think about when signing up for these accounts is what will happen to them when we pass away. Should we write your passwords down somewhere? Can someone gain access to them after we’re gone? What happens to your social media after death? It is reported that around 8,000 Facebook users die every day. It’s important that policies and protocols are put into place.
As of this year, at least 2.34 billion people worldwide are social media users. In the United States alone, 79% of people have a social media profile. Something we don’t really think about when signing up for these accounts is what will happen to them when we pass away. Should we write your passwords down somewhere? Can someone gain access to them after we’re gone? What happens to your social media after death? It is reported that around 8,000 Facebook users die every day. It’s important that policies and protocols are put into place.
Facebook & Instagram
Facebook and Instagram are the only major social media platforms that “memorialize” your account.
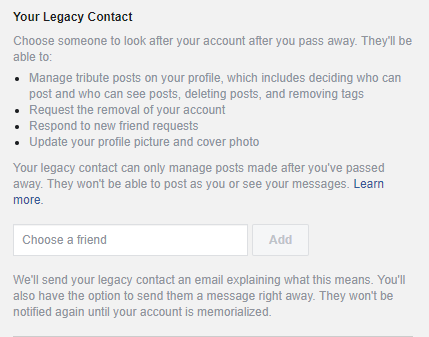
With Facebook, you can set up a “legacy contact”. This is the person who will manage your account after you’re gone. To set up your legacy contact, go into your Facebook general settings and select Manage Account and choose the person to take this role. As seen in this screenshot, the person you choose to be your legacy contact will not be able to post as you or read your messages. If you don’t want to have a legacy contact, you can also request for your account to be deleted when the time comes. To request for an account to be memorialized, contact Facebook here.
Instagram does things a little bit different. There is no legacy contact that can manage your account for you when you die. Once a family or friend sends a report and the account is memorialized, it appears mostly the same. However, the account will not show up as a recommendation anywhere on the app (such as in the explore section). Nothing can be deleted or changed on the account after it is memorialized.
Other Platforms
For most other social media platforms (including Twitter), there are no memorialized profiles, therefore a family member has to request the removal of a deceased user’s account. In general, social media platforms will never give login details to anyone but the account owner, even immediate family members. This would violate most terms of service. If you want someone to have full access to your social media, it may be smart for you to put this in writing with something like a digital will. This will hand over ownership of your accounts after you pass away. This helps avoid violating any terms of service.
Computers and Devices
That great password you’ve set up on your computer or device to keep others out will do just that after your death. As a rule, device manufacturers will not grant access to others to get around your pass codes and passwords. Keep in mind many of your online accounts also have 2-factor authentication too. Banks and other service providers are happy to work with whoever holds your power of attorney posthumously, but email accounts and other online accounts will need to be accessed with the information you leave in your digital will.
Though it may be odd, it is important to have a plan for what happens to your social media and online accounts after death. Set up your legacy contact on Facebook today. Also, inform your friends and family by sharing this with them! Subscribe to our bi-weekly e-newsletter for more helpful information like this!
Maintaining Your Company’s Social Media

Being active on social media is almost required to run a successful business these days. We also know that it can be difficult to gain and maintain an active following. This is why it is extremely important to make sure you create and approach your social media accounts in a professional manner.
Creating Business Social Media Accounts
One of the most important things to do when creating profiles for your business is to use a business email address (for example: marketing@companyname.com). Do not allow an employee to use their own email when setting up social media accounts. We’ve seen companies let go of employees and lose access to accounts because they hadn’t been set up using a business-owned email address.
Employee retaliation can even result in the account being deleted with no option for recovery. This means you would lose access to the audience you worked so hard to build up. You’ll have to start all over which can be a large waste of time and money. Make sure to use a company email and keep track of your passwords!
Posting to Your Business Social Media
Nowadays, there are too many social media platforms to keep up with. It is time-consuming to jump from platform to platform and make individual posts. Thankfully, there are tools available which make this process much faster and easier. Using a program like Hootsuite helps by enabling you to schedule posts to almost any social media platform from one location, all at the same time. It will also allow you to schedule posts out for days when you aren’t going to be at the office. Scheduling ahead like this also gives you time to proof each post before it goes live. You can even send the draft around internally to get another set of eyes on it before any embarrassing mistakes go out to your audience. If Hootsuite isn’t your cup of tea, there are many other alternatives for you to choose from.
Having Social Media Guidelines
Making sure you have a company social media policy in place is important. Your social media policy should outline that an employee’s online activity reflects on the company and employee. It should remind employees of your company’s privacy and confidentiality rules. Setting rules in a policy ensure that nothing gets posted that shouldn’t. Your policy should educate and train your employees about using social media on behalf of the company while presenting a consistent corporate image. Keeping your posts on-brand and relevant will help them stand out from the crowd.
Conclusion
To maintain the security and longevity of your social media accounts, make sure they are created with company credentials. Use a scheduling program like Hootsuite to plan and proof posts before they go live. Lastly, have a clear social media policy in place to ensure the appropriateness of the content being posted. You can always call in a professional to handle your company’s social media. Appletree MediaWorks has an on-staff Social Media Specialist that is experienced in managing social media accounts for businesses like yours.
Get weekly tech tips and helpful products by subscribing to our bi-weekly newsletter for free (at the top of the article)!
06/07/2019 E-Newsletter: Did Microsoft call? How to Make Strong Passwords
Take a look at the new and improved Asphalt Management Inc website! On top of that, check out this easy method for creating secure (but easy to remember) passwords! Let us also help you not fall victim to these popular scams making the rounds. Read More
05/22/2019 E-Newsletter: Welcome to Appletree’s E-Newsletter
Vulnerabilities were found in popular applications you may use. Make sure you update! Another week another scam..stay up to date with us here! On the bright side, W. Soule has a nice new site, fully responsive with a custom programmed management system. Also, have some old technology lying around? There is a right and wrong way to get rid of it!Read More
Microsoft Scam Calls are Still Rampant
 Microsoft scam calls have been around for a while, but they’re still detrimental. In 2018 alone, it’s estimated that tech support scammers managed to take a whopping $55 million out of the bank accounts of over 140,000 innocent people. These scammers call you out of the blue to catch you off guard. This is why it is important to know exactly how to handle scam calls and get real support when needed.
Microsoft scam calls have been around for a while, but they’re still detrimental. In 2018 alone, it’s estimated that tech support scammers managed to take a whopping $55 million out of the bank accounts of over 140,000 innocent people. These scammers call you out of the blue to catch you off guard. This is why it is important to know exactly how to handle scam calls and get real support when needed.
How to Identify Fraudulent Support
Unsolicited calls from anyone claiming to work for a software company and asking for bank information are not real. Similar calls telling you that your computer/device is infected are usually not real. The best thing to do would be to hang up, report the incident, and block the number. Unfortunately, some of these scams are becoming a little more sophisticated. Sometimes Microsoft scam calls may appear on your caller ID as the real number for Microsoft. This is called caller ID spoofing.
Caller ID spoofing is done through a computer program that allows the user to change the outgoing number to anything. This makes it harder to block and report the scammers.
In the event that you receive a call from any company such as Microsoft, you can always hang up and contact them yourself to confirm if the call was real or not. On Microsoft’s website, they have an option to instantly chat with a real Microsoft support person. You should be able to verify if you were actually being contacted by Microsoft or not. You can also find their real customer service numbers on the Microsoft website if you prefer talking on the phone.
If you are ever prompted with a pop up telling you to call immediately because something is wrong with your computer or information has been stolen, you can rest assured that it is not real. Microsoft error and warning messages will never have a phone number for you to call. Follow the steps below to get rid of and avoid these pop-ups.
How to Get Rid of Pop-Ups
Browser Pop-Ups
If you are browsing the web when you receive a pop-up, all you have to do is close out of it. The best way to do that is by pressing CTRL+W. This will close the tab that is currently in focus without you having to click on anything. This minimizes the risk of you accidentally downloading malware by clicking a false X or initiating other hidden downloads. If you see something did get downloaded, do not click on it in the downloads bar. Go to your downloads folder of your computer and delete the download, followed by clearing your recycling bin to make sure it is completely off your machine.
To avoid browser-based pop-ups like this, make sure you have your pop up blocker enabled. We also recommend that internet users download an ad blocker like Adblock Plus. It is completely free and blocks any intrusive or misleading ads, but whitelists legitimate ads that are clearly labeled as advertisements. If pop-ups persist, check your browser extensions and make sure to uninstall any extensions that you do not recognize.
System Pop-Ups
In the case of receiving odd system pop-ups, this is probably caused by a virus that is already on your computer. If these pop-ups are new and you recently installed some software, you might have missed something in the installer that was packaged with the software. Make sure to uninstall any non-native programs that you do not recognize. If you’ve been having pop-ups for a while and can’t pinpoint where they’re coming from, scan your computer with Windows Defender Antivirus which is built into Windows 10 (if you’re not running Windows 10, make sure to update soon to keep your computer secure).
Never Be Too Sure
It’s important to never immediately trust any email, phone call, or computer message that you receive. Make sure to confirm that you’re talking to the people you think you are to avoid falling victim to a scam that has claimed the dollars of so many. Keep your computer and your money safe and sound. Appletree clients frequently forward us emails and text messages that they’ve received. Many of these scams appear to be legit until we look closer at them. Check out our blog for how to spot a scam email.
When in doubt, feel free to contact Appletree, we’re happy to provide peace of mind.