How Do I Recover My Data After A Computer Crash?
Set your mind at ease and back up your files now.
One of the most important (but also the most neglected) areas of computing is backing up your data. Most people assume they’re safe because they’ve never experienced a disaster in the past, but they are sadly mistaken. It’s not a matter of if, it’s a matter of when. Laptops get wet, hard drives die, viruses are caught, tablets are stolen, at some point you will be kicking yourself if you neglect the important task of backing up your data.
What does it mean to “backup?”
“Backing up” refers to the copying and archiving of computer data so it may be used to restore the original data after a data loss event. When a computer user backs up their data, they are storing a copy of their information in a safe and secure place. There are many options when it comes to backing up your data, and most of them are reasonably priced.
Why is backing up important?
Backups protect you from hardware failure, viruses, theft, accidental deletion, fires, floods and other disasters. If you were to experience any of these events without first backing up your data, you run the risk of losing all your work and important files. It is suggested that you have at least two off-site backup copies of your data; however, many people get by with just one.
What products are recommended for making backups?
1. Subscription Backup Services
There are many services out there to assist businesses and individuals in backing up their data, often with only a few clicks of the mouse. Carbonite boasts that they are automatic, secure, and affordable with plans starting at $59 per year. Many of our clients have also been happy using Mozy for their backup vendor. Another great service is Crashplan, whose plans start at less than $20 a year.
2. Cloud-based Document Storage Services
For documents that you are constantly using and changing, you may want to consider a cloud storage option, such as Google Drive or Dropbox. Both of these options offer two-step verification for added security, as well as a small amount of free storage. More storage space is also available for purchase from both of these vendors.
3. Self-service Storage
If a paid service doesn’t fit your budget, you can also backup your data yourself. Technology retailers have storage devices available for purchase and you can talk to a customer service representative to decide which storage device is right for you. The only downside to this is, of course, that you have to actually remember to back up your data on a regular basis.
How do website vendors protect your data?
Our staff here at Appletree MediaWorks, LLC has seen viruses take out websites before, we’ve seen malicious activity cripple a site and we’ve seen website plugin updates wreak havoc on entire websites, but in the end it all came down to restoring the website and databases from backup. We keep your website and databases backed up nightly and the information is always stored in a safe place. As for the rest of the data and pictures on your personal computer; please see our advice above or give us a call, we’d be happy to one of our developers help you setup a backup plan.
Then you won’t have to ask the question, how do I recover my data after a computer crash?
UPS Stores and Banks Were Hacked
UPS Stores were hacked
UPS stores were hacked in a data breach recently, with stores in 24 states subject to the data breach between March 26 and August 11. “No fraud has yet been discovered, UPS said, but customer names, postal addresses, email addresses and payment card information were compromised. ”
Banks hit by Hackers
Several large banks, including JP Morgan Chase & Co., which lead to theft of data associated with accounts. The theft involved significant amounts of data which could potentially lead to serious financial fraud.
More than a Billion Passwords Stolen by Russian Gang
Ready to change your passwords again?
If you didn’t bother changing your password when you heard about “Heartbleed” leaking out passwords, you might want to consider changing your online passwords today. In the largest known collection of stolen internet credentials, a Russian tech gang has reportedly acquired an estimated 1.2 billion username and password combinations, along with over 500 email addresses.
A security firm based out of Milwaukee, Wisconsin conducted an 18 month study of the security breach. It has not announced specific sites that were hit, citing non-disclosure agreements and concerns for websites that still may still be vulnerable. An independent security expert confirmed the claims as authentic.
The hackers used unsuspecting zombie computers with viruses to allow a single operator to control a large group of virus infected computers to test for SQL vulnerabilities on servers.
When vulnerability was discovered on a website or server, hackers then executed SQL injections to send malicious commands to the website. In this way they were able to collect databases full of user names and passwords. Small and large websites have been affected worldwide by this hack.
So far, the stolen data has only been sold in small quantities on the black market, and used to access social media to send out spam messages. Hold Security had originally offered to check security breaches for a fee of $120 but seem to be revising their efforts after some criticism.
So what’s a person to do when it seems like keeping data secret is a losing battle?
- Change your passwords, and make sure they are strong, secure passwords with capital letters, lower case letters, numbers, and special characters.
- Businesses should run a check with the webmaster to see if their websites are vulnerable to SQL attack.
- Don’t use the same username/password combination for all the sites you access, particularly important ones like banking.
- Don’t panic, and have a plan in place in case you are a victim of data theft.
For more information on keeping your data secure, visit our blog posts on Heartbleed, and Preventing your Email from Getting Hacked. Or you can contact us here at Appletree MediaWorks for more information.
Internet and Security Updates
Heartbleed Followup
Lest you think the Heartbleed concerns were merely a false alarm: 4.5 Million Patient records were stolen by hackers, presumably due to the exploit.
The hackers took advantage by finding a device that had not been patched, exploiting the bug in order to steal user credentials. They used this data later to login into the network of Community Health Systems and captured patient names, phone numbers and social security numbers.
If you are concerned that your information might be among what was stolen, our recommendation is to invest in an identity monitoring type program or to lock down your credit report so that credit cannot be opened in your name.
As we’ve said before… Update your passwords often. Keep them unique – do not use the same passwords for every online account you own. Make them challenging – include numbers, letters, different cases, and symbols if allowed. Use password management software to keep track of all this. And it is always a good idea to keep an eye on your credit report.
More Data Theft from Stores
Unrelated to Heartbleed, SuperValu, the Minnesota parent company of Cub Foods, Farm Fresh, Hornbacher’s, Shop ’n Save, and Shoppers Food and Pharmacy, Albertsons, Jewel-Osco, announced that 180 stores in North Carolina, Maryland, Virginia, Illinois, Missouri, North Dakota, and Minnesota were affected. The stores are reporting they quickly fixed the security breach and it’s safe to use credit cards in their stores again.
There’s no sign yet of the data being sold on the black markets. Credit card data is said to be selling at $20-100 per card, often purchased in bulk as one-time use.
It’s always a good idea to keep track of credit card statements; credit cards carry theft protection, and if theft is detected they should be contacted quickly as possible. It’s also wise to prepare for data and identity theft in advance, with the assumption that it will eventually happen. Make a plan of action: Contact credit-reporting agencies, get a copy of your credit report, and in the case of identity theft, file an identity theft report.
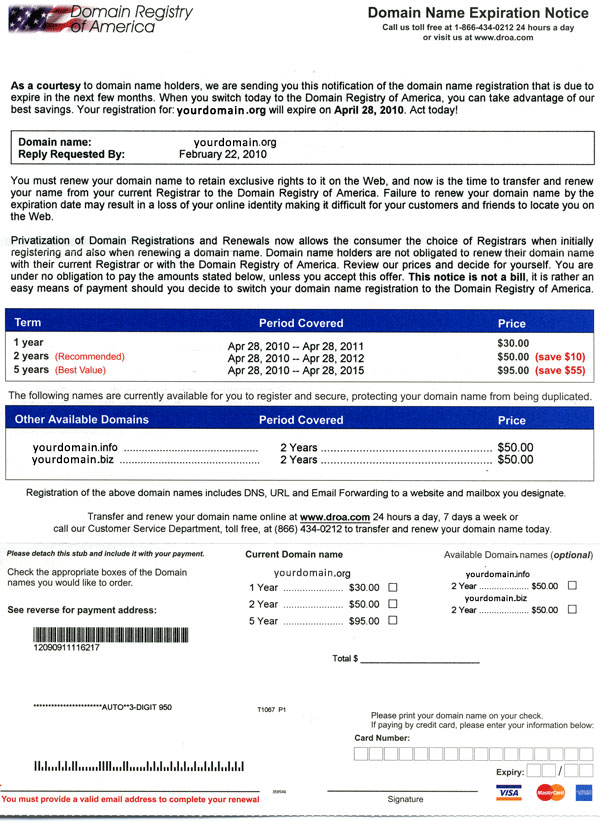
Domain Registry of America and Domain Slamming
Domain Registry of America and Domain Slamming
If you have ever registered a domain name of your own, you may have received an alarming letter or ‘bill’ alerting you that your domain name is about to expire, and giving you an ‘easy way’ to renew it. The letters look legit at first glance. But checking with your host will usually indicate your domain is fine and does not need an urgent renewal. Even if it does, you can do so through your registrar for the normal price.
So what gives?
Is this a scam? How did they get that info, and is this even legal?
The answers are a little nebulous, like so many scams. We’ll shed some light on just what is going on here.
Domain Registry of America (among other names) is a borderline-legal scam designed to convince you to switch your web hosting for inflated prices. The company itself generally has a post office box in the United States, but seems to have other addresses in other countries and is presumed to come from abroad. This makes the legality more difficult.
Your postal address and information is obtained from “WHOIS,” a public database of registered domain names. The letter is not actually a bill, but carefully written document designed to persuade the domain owner to switch domain hosting to their company at highly inflated prices.
What to do?
If you receive one of these notices, the best thing to do is just ignore it. But let’s go into some detail on how you can be SURE you are not going to lose your domain name.
1) Know the name of your registrar. The registrar may or may not be the same as your web host, but know who your domain is registered through. If you get notices from anyone other than your registrar, you can generally dismiss and ignore them. As a note, your domain name and host may not expire at the same time.
2) Know when your domain name expires. This can save you the potential loss of a domain name and all the trouble that comes with that, and it can also spare you quite a bit of anxiety, wondering when the expiration date is going to happen. Some companies will email you to let you know, but it’s good to remember this anyway.
3) Put your domain name on autorenewal if at all possible. You can’t just do this and forget it – credit cards expire as well, and it’s good to check up on things, but if your domain is set to autorenewal it’s less likely to slip past you.
What happens if you lose your domain name?
Other than purchasing it back for generally much higher costs, there are not a lot of options after losing a domain name, beyond getting a new one, changing your business card and information everywhere, and making up for lost emails. The single best option is to educate yourself, not fall for the scams, to keep track of your own domain name renewal so as not to risk losing it to begin with.
Don’t let Domain Registry of America alarm you. This and many other scams are out to make a dollar (or many). Education is key. When you know what you’re reading, you know what you can ignore. And for more information on various scams, visit us here at Appletree MediaWorks.
Heartbleed
What Heartbleed is, and What You Should Do
What is it?
Heartbleed sounds scary by the name alone. It’s all over the news, but just what is it? What should the average Internet user do about it? Heartbleed is complicated and involves some Internet security understanding, but here we’ll strip out most of those details and get to the essentials.
Heartbleed is a bug – a mistake in security code – that has potentially allowed in-the-know hackers to exploit the problem and grab unencrypted usernames, emails, passwords, and other random sensitive information a bit at a time through small packets of data, nicknamed “heartbeats.” The bug has been around for two years, but it was only just discovered by companies Codenomicon and Google.
Who is Affected
Any “secure” website using the security software OpenSSL which had the buggy code (an update within the last two years) could potentially be compromised. Nobody knows for sure if they HAVE been compromised. It is possible that up to two thirds of the web could have this bug. There are a lot of unknowns.
Some big websites may have been affected: Yahoo, Google , and Facebook. Though these websites have already updated their software, they suggest that users still take the time to change their passwords.
Some websites never used the vulnerable software: big banks were less likely to use the open source software, Microsoft said it was unaffected, and LinkedIn seems to have been safe.
Why Should You Be Worried?
You should be worried because if someone has exploited the bug, your usernames, emails, passwords, security questions, and other sensitive information could have been available to malicious users for the past two years. If you use the same passwords (or similar passwords) on multiple sites, this could give them access to those other websites as well.
If a website with the compromised code does not update, they are still an open gate. If a website has updated but you have not changed your password, someone might have that info to use when they see fit – if someone has grabbed that info in the past, they still have it.
We don’t know how extensive the problem is – entire website databases could have been compromised. The good news is that the bug was brought it to our attention rapidly after it was discovered, allowing word to get out before the bug was exploited on a wider scale.
Recommendations
There is only so much a user can do. The biggest problems lie on the website side of things, and it is the responsibility of those website owners to update their keys. If the website has not run updates on their side, the bug can still be exploited even if you change your passwords.
Most big companies updated their software right away and recommend changing your passwords. Unfortunately, not all companies are being clear about whether or not they were vulnerable to the problem, and if they have since patched the bug.
Our recommendations are to do the following:
- Update your passwords on all of the websites you use, especially ones where you store sensitive or personal information.
- Make sure all your passwords are different – do not use the same one for each website.
- Be prepared to change your passwords again in case a site has been slow to update.
Best Practices Going Forward
It’s hard to remember many complicated passwords (and complicated passwords are the most secure), so we recommend using a program like LastPass or KeePass to keep track. While nothing is entirely failsafe, they are a lot more secure than trying to remember many simple passwords or even worse, using the same password everywhere.
It is also good practice to update your passwords periodically.
When, Not If
The internet is complex and only getting more so, and for better or worse much of it is unregulated. When it comes to any kind of security breach or data theft, expect that something could potentially happen, and work out a plan for what to do when it does.
Follow Appletree Mediaworks on Twitter or like us on Facebook. Visit our website for more information on data and security and what to do about breaches, and about what’s happening on the web.
—–
Common Sites You Should Change Your Passwords For
Password Changes Suggested (They have updated their SSL)
Facebook
Tumblr
Google/Gmail
Yahoo
Turbotax
Dropbox
SoundCloud
Okay/Don’t need to change passwords*:
LinkedIn
Amazon
AOL
Outlook/Hotmail
Paypal
Target
Most big banks
Taxes/Accounting sites (except Turbotax)
Evernote
Unclear: (Have not made an official statement – they claim to be okay, in some cases)
Twitter
Apple
Ebay
Netflix
* It can’t hurt to change your passwords anyway. Just be prepared to do it again if necessary.
Technical Details of Heartbleed: http://heartbleed.com/
Phishing for Paypal
Have you ever received an email from PayPal, informing you that your account has been limited or compromised, and to click on a link to correct things? Been tempted to follow the instructions to fix the problem? Or did you recognize the scam when you saw it and deleted the email?

The Paypal Phishing scam is one of the most prevalent email scams on the web today and the spoof emails often look legitimate, using an email address that seems to match Paypal, using Paypal’s own logo and graphics that match the website.
But How Does It Work?
The trick to the scam is to get an unsuspecting user to click on the link. This link takes the user to a spoof site that may look very close to the real thing. Here the user will be prompted to log in (handing over their Paypal login credentials), and then enter personal data including banking and credit card information. This information will be sold later on the internet black market.
How Can I Tell?
How can you spot the scam? It can be tricky to find the clues, and generally it’s just easier to circumvent the problem entirely. Paypal won’t write you an email entitled ‘dear member’ or ‘dear customer’ – the company uses your real name or company name. They also won’t use a variant URL although this can be tricky to spot. Instead, there are appropriate steps to take if you do think you are receiving a scam email.
What Should I do?
1) Don’t click on the link. This will take you to a spoof site. Instead, if you wish to log into your Paypal account, go to your web browser and type in the Paypal URL by hand.
2) Don’t download any attachments or programs. This goes for virtually any unfamiliar email attachment, but especially Paypal: the company will not send you these things.
3) Go to Paypal’s website and search help for ‘scam’ where the company will provide you with an email to forward to Paypal so they can follow up on who’s putting out that particular scam.
4) If you think your info has been stolen or you find suspicious activity on your account, there are steps to take as quickly as possible, to minimize the damage done. Paypal has set up a Security Guide on the steps to take to combat fraud, if you believe you have been a victim.
Update 2/24/2015
Google has been sending out emails making reference to Google Play Phishing. This is exactly the same technique we mention above, but it’s directed toward Google Play Developers, designed to get them to click quickly, without thinking.
Remember, when in doubt, navigate through your browser to the proper website and check things out – do not click on readily supplied email links.
How Do You Prevent Your Email From Getting Hacked?
Duplicating Usernames and Passwords is Risky
Database vulnerability
The truth is many online databases do not encrypt your username and password at all. So one dishonest employee can have thousands of passwords in one quick database export. If one online shop gets compromised, then all of the places you use that username and password are now vulnerable. Use a different password for every website login you create and use a specialized program to store those big beautiful passwords.
Brute force attacks
Many attacks are brute force attacks in which a computer program is used to try lots of combinations of passwords rapidly. The simpler your password, the easy to ‘guess’ by the program. Again, if your password is figured out and you use the same on multiple websites, your risk is increased exponentially. Use different passwords to prevent getting your email hacked.
- Use different login credentials and complex passwords on every website you use. We featured an article on our blog featuring more information and tips about passwords.
- Just say no to browsers storing passwords! When Internet Explorer or Mozilla asks to store a password for you, ALWAYS say NO.
- To remember all your new passwords, use a service like 1Password or KeePass to create and store login information. KeePass is free!
Keep Your Software Updated
Out of date software is risky, especially web browsers and other web-based programs including browser plugins. Usually updates are released for software in response to a security hole or technology expansion. Many programs update automatically, but set your phone or calendar to remind you to check on these things every few weeks.
- Keep Windows and your antivirus software up to date.
- Run updates for your programs when they ask. If a program is asking to access your computer that you don’t recognize, choose No for now and check out Google to see what is suggested for that update name.
Pay Attention to Login Sessions
Some sites will tell you the last time you logged in successfully. Change your passwords if things seem fishy. Some programs such as Facebook and Gmail monitor your logins, other programs will let you setup verification by text messages.
- Use verification by text message, if a program asks if you’re using a public computer to login, say yes if you are.
- Do not create obvious security questions in which people can find the answers by searching Facebook or other sites.
Think Before You Click
If you receive an ambiguous or unexpected email, even from a relative or close friend telling you to click a link. Don’t do it. Contact the person over the phone and ask what the email message. Same goes for attachments. If the email does not look like something your contact would send you, QUESTION it!! Email spoofing is common too, for example there have been very real looking emails floating around that appear to be from the IRS, but the attachment is a virus.
- Ignore and delete strange emails even if they’re from friends, family, and banks. Don’t click the link or open the attachment – it’s a surefire way to get a virus.
- If you find out your account has been hacked and an email was sent from your account, first change your password. 2nd follow up with those that received your hacked email message. Tell them your email was hacked and that they should DELETE the email they received from you.
Watch Where You Login From
Be careful if you are logging in from a public computer or a network that is not secure. Do not stay logged in, when you are done with the website be sure to log out. Connecting to public WiFi can open the door to hackers.
- Be sure your computer has a strong firewall. The annoying extra click to allow something to access or update your computer is better than a hacking mess from keeping the door open.
How do you prevent your email from getting hacked? As identity theft and account hacking becomes more rampant, there is no foolproof way, but you can minimize risks by using our suggestions. It is best to set up your accounts so that if one gets compromised not all of them do. Have a plan set up on what to do if an email gets hacked or a credit card gets stolen, and know that it is extremely common, if problematic.
If You Do Get Hacked
- Change your password if you can still get in to your account.
- Follow the directions in the help center of the website you’re trying – most sites have guides on what to do.
- Scan your computer for viruses and malware, then schedule future scans to happen weekly.
- Let people know you got hacked and not to click on links, and pass along info on what to do if they did.
- Report the incident to the website. You may get access to identity protection services through the hacked site.
Extra Credit
Protecting your credit card information online goes hand in hand with your email getting hacked. We suggest using a payment service such as Paypal to store your credit card number rather than typing your credit card number directly into a website. Websites and stores are not supposed to store credit card numbers in their databases….but there are no internet police enforcing this.
Follow Appletree MediaWorks on Facebook or subscribe to our website blog RSS feed to keep up on topics like this.
Facebook Data Use Policy Updates

What is the Facebook Data Use Policy?
Facebook is updating its policies again, a move which will inevitably lead to another round of people declaring that the company is selling their 852 photos of Jr. and posting custom legalese on their timelines in an attempt to contradict whatever new policies the company has written.
Is Facebook using your private gallery in advertising? Will establishing your own copyrights in a post make any difference? The answers are no, but what really goes on behind the scenes regarding Facebook advertising, privacy, and its Data Use Policy can be a bit murky and complex, if not a little insidious. The current round of proposed updates includes more attempts at clarifying what already exists with new language so there’s not much new there. But just what are they doing, and how can you control your own data?
It Starts With You
First and foremost, as a Facebook user you must take control of your privacy settings. Facebook’s biggest crime is a tendency to make their users ‘opt out’ of sharing information, rather than opting in. It is up to an individual user to learn about privacy settings and who will be able to access and use their information. Facebook changes things around a lot, which makes keeping track of your permissions (and finding the settings) more complex than it has to be. Even so, Facebook will not share more than you allow – the trick is to knowing what you are allowing.
Public Information: Anyone can see your public information. It is what people use to search for others, and it’s what makes the social network social. Some information is always public, no matter how private you make your profile: your name, your profile picture and cover photos, your network, your gender, and your Username/ID. If you upload a picture of your kid as your own profile image or as your cover photo, that image WILL be visible to all.
Other Public Info vs. Private Info: From here, you choose whether to make your wall and other information public, shared with your friends, or customized. The little globe icon right next to the post button indicates that something is public, the icon of two people means ‘Friends’, and the gear means that a custom permission has been set (you can customize who sees what; for example, if you want to keep your family oblivious to your more off-the-wall hobbies). However, despite what you place as your settings, the publicity of your actions depends on what you do and where you post as well. If your friend makes a public post and you comment on it, then you should expect your response to be public. If you are posting to a public group, then other people may see it.
Your Friends
Your friends will see what you post to your wall, what you like, and what you share. Your friends may also affect the advertising you see, they can add you to groups, and they can affect your Facebook life in other ways – such as tagging awful pictures of you. Keep track of who you friend and how you plan to interact with that person. Sometimes the interaction can get out of hand in unexpected ways.
Likes Vs. Shares – And how Social Advertising Throws This Off
When you Share something on Facebook, you expect other people to see it and pass it along – this is a given. Facebook is social after all, and you want to share things you enjoy. Keep in mind, however, that when you Like something on Facebook, you are endorsing it – which may affect the way Facebook advertises to you. Your profile and image may also appear to your friends on that or other affiliated websites. Additionally, your endorsement may appear in the advertisements that your friends see in Facebook.
Did you click ‘like’ two years ago on a friend’s photography fan page? That photography page might show up in another friend’s news feed, endorsed by you – which could get awkward depending on the content of their photography, for example.
Social Advertising has the internet in a tizzy these days. While Snopes has put the rumor that Facebook is using your private images in public advertisements to rest, what you decide to share might very well be everybody’s business, depending on your privacy settings. Things you share and your likes will be shared with your friends. Likewise, the information that you allow apps to access will be sent to those 3rd party companies.
Data Mining
Even if Facebook is not stealing your images to use in public advertising (and your content DOES belong to you) Facebook’s data gathering is complicated, and may reach well beyond the scope that many people realize.
Everything you do on the Facebook platform is tracked – what you click on, what you like, the information you post about yourself, where you are, and your general behaviors. This information is intended to personalize the targeted advertising to you – it’s all about the ads. Say your public information states that you are a 28 year old male in Flint, that you like a given restaurant and you like ice hockey. Even with your personal identifiers are removed, that information is still highly detailed. If someone is looking to advertise a Flint Generals event at a given restaurant, you might fit into the demographic, sparking an oddly specific advertisement to appear on your news feed.
Even if you yourself rarely click a Like button, your friends can be used to fill in the gaps. (This is why we mentioned being careful about the people you are Friending.)
Beyond the Web
Data mining is not limited to Internet activity alone. Remember those little customer loyalty cards you scan at the store for discounts? The information gathered from these cards can be fed into one of several big data mining companies who can then associate it with your Facebook account (using a hashed email or phone number). If you purchase a car at a local dealership, you may be shown an advertisement for that car dealership on Facebook even if you never Liked anything related to it.
What to Do
Does this make you uncomfortable? If not, continue on your merry way. If so, however, there are steps that can be taken to minimize your use to advertisers in this way.
Update Privacy Settings: On Facebook you should regularly update your privacy settings and check out the new features. The little lock icon in the right hand corner of Facebook’s blue nav bar along the top will take you to the privacy page which allows you to manage everything from your timeline and tagging to deleting old apps and editing your Facebook Ads permissions. This is where you control social advertising.
Audit Your Likes: If you are worried about what might show up in advertising you can go through and delete old Likes, hide or delete wall posts, and otherwise clean up your account. Even if you’ve set your security to private, this can minimize future awkward advertising and associations, and avoid giving free advertising to companies that you don’t actually want to endorse.
Addon Help: Facebook utilizes cookies and browser storage. There are a variety of browser addons and extensions that will reduce your cookie tracks throughout the web, and there are also addons that will allow you to adjust what you see and use on Facebook.
Opting Out: The real-world data mining can be controlled to a degree as well. Using a different phone number (Google Voice offers secondary phone numbers) or an alternate email than the one used with Facebook can reduce the ability for companies to associate the two. The Electronic Frontier Foundation has written a guide on how to opt out of data mining for some of the big data companies.
Calling it Quits
If all this data mining combined with concerns over the NSA’s information gathering make you want to reach for your tinfoil hat, deleting your Facebook account is an option as well. This takes about a month to do and you may still have data in their servers for up to 90 days, but it is always an option to consider. While things you have posted on other peoples’ walls or comments may not entirely disappear, it will definitely reduce your digital footprint.
Protecting Your Facebook Passwords and Account
Let’s face it, any website that houses the daily drama of over 1 billion users1 is going to become a pretty huge target for myriad hackers, pranksters, and scam artists alike. That’s right, Facebook has over a billion users, most of whom have no idea how to protect themselves. According to a report by the Escapist Magazine, over 600,000 Facebook accounts are compromised every single day2. Want to avoid becoming a statistic? Following these simple guidelines will greatly reduce your vulnerability and help you stay as safe as possible.
Use Strong Facebook Passwords
No matter how many security measures you take, if you don’t use a strong Facebook password, your door is wide open. Strong passwords should contain at least 8 characters and have a mixture of lower- and upper-case letters, symbols, and numbers. Too hard to remember? Why not try using phonetics? For example, tooeasy123 is a bad password. But To03asy!2E is a fantastic one.
Contrary to popular practice, passwords should always be something random and unrelated to you. Too often, people use their pet’s name, their child’s name, or a hobby. Keep in mind that such things are easy to guess or look up. Also, if your password can be found in a dictionary, it will easily fall prey to a simple dictionary attack. Again, obfuscating phrases with numbers and symbols is a great way to strengthen your passwords.
We also recommend changing your passwords about once every 3 months. If you have trouble remembering passwords, you might consider using a password manager such as 1Password or LastPass to help you keep track.
Think Before You Click That Link!
If a friend sends you a link via email, text message, or instant message, make certain that you know what you are clicking on before you do it. Short links such as bitly are especially vulnerable, since you are not given any clues as to what you are clicking on before it’s too late. Don’t worry, your friends will understand (and often appreciate) when you ask them what they are sending you. Often when an account gets compromised, the original owner may not even be aware that links are being sent out in their name. If they don’t remember sending any links, chances are good that they have been compromised (and you just avoided sharing in all the hassle!)
Don’t Believe Everything You Receive
I always tell people – never send anything via email that you do not want to see on the front page of the newspaper tomorrow morning. Even as the Internet has evolved, email itself remains one of the most insecure protocols on the planet.
It is frighteningly simple to spoof email and make it appear to come from somebody that had nothing at all to do with it. We’ve all probably received a scam email or two from a “stranded Nigerian prince” who just needs us to help him out so he can get back to his fortune and reward us for our random assistance. This has become one of the most tired scams in the book.
But thanks to Facebook, we are now seeing a fun little twist to this tale of sorrow and woe. Instead of appearing to originate from someone in Nigeria, the latest strategy is to pose as one of your friends from your Facebook friends list! Be aware that the next time one of your friends appears to be asking for a big favor via email, it is likely a scam. Before you click on any links or respond to the message, always call your friend and make sure that it is real.
These guidelines will help start you down the path towards better Facebook (and Internet) security. However, always remember that security is a constant battle. Hackers and scammers are very clever opponents, by definition. We must always be vigilant and keep our eyes open for suspicious behavior. Facebook’s Help Center offers a wide array of additional security suggestions and tips. And of course, Appletree MediaWorks is always available to assist in keeping your accounts secure.
1. Forbes reported in October of 2012 that Facebook now has an account for one out of every seven people on planet earth.
2. Reported by The Escapist Magazine in October of 2011, these numbers were first compiled into an infographic by Sophos Security. It is worth noting that although 600,000 is a very large number, it is only .06% of Facebook’s total user base.











