iCloud Hack and Compromising Data
Take a photo – it will last longer. But do you really want it to?
By now practically everyone has heard about the hacker that managed to acquire private, compromising celebrity photos and post them to distribute on websites. While all the details are still being worked out, the most common theory is that the hacker managed to get to these photos through the use of brute force software and an exploit or hack in iCloud, Apple’s iPhone cloud service.
This particular episode in questionable internet security is making news because of the enraged celebrity targets and the wildfire pace at which the images are making their rounds, but this sort of data breach could happen to anyone. And until Apple and investigators figure out and announce just what happened, users are left trying to keep things secure as possible.
What can you do to keep your data secure?
Strong Passwords
Email is inherently unsecure. Do you really need a backup of all of your emails sent up to a vulnerable cloud too? It’s likely your work email is backed up by your employer and usually personal email providers backup their own email servers, so don’t allow your email to be copied to a cloud too. If you truly need an important email for reference later? Go old school: print it out and store it in a safe or forward it to an encrypted email server for storage.
Photo Stream
Cloud storage is not inherently the most secure way to keep data, and it’s also known as a potential target for hackers. Incidentally, if you have an Apple phone or tablet, Photo Stream may be active and you might not even know it.
You can disable the Photo Stream by doing the following: Go to “Settings,” then “Storage & Backup” and stop the “Photo Stream” feature. This will stop all your photos from automatically uploading to the cloud.
Android and other phones have their own means of cloud backups to check into as well. Some require setting up manually, and others may prompt you to activate them. Read the messages you are given, and check into your settings from time to time.
2-Step Verification
Although it may not have helped in the case of the iCloud hack, 2-Step Verification increases security in devices, and many services including Apple, Twitter, and Gmail have it. 2-Step verification requires that after the user enters a password, you go through an additional step of verification (such as entering a code you are texted) on new devices.
Precautions
Without blaming the victim, keeping compromising photos off easily accessible devices warrants mentioning as well. While phones make it easy to take and send a quick snapshot, this is not inherently secure. And on the user-end, even if your own tech is secure remember that any photo you send to someone else could end up on the wilds of the internet.
If you want to take those potentially compromising photos? A camera may be a better option.
How Do I Recover My Data After A Computer Crash?
Set your mind at ease and back up your files now.
One of the most important (but also the most neglected) areas of computing is backing up your data. Most people assume they’re safe because they’ve never experienced a disaster in the past, but they are sadly mistaken. It’s not a matter of if, it’s a matter of when. Laptops get wet, hard drives die, viruses are caught, tablets are stolen, at some point you will be kicking yourself if you neglect the important task of backing up your data.
What does it mean to “backup?”
“Backing up” refers to the copying and archiving of computer data so it may be used to restore the original data after a data loss event. When a computer user backs up their data, they are storing a copy of their information in a safe and secure place. There are many options when it comes to backing up your data, and most of them are reasonably priced.
Why is backing up important?
Backups protect you from hardware failure, viruses, theft, accidental deletion, fires, floods and other disasters. If you were to experience any of these events without first backing up your data, you run the risk of losing all your work and important files. It is suggested that you have at least two off-site backup copies of your data; however, many people get by with just one.
What products are recommended for making backups?
1. Subscription Backup Services
There are many services out there to assist businesses and individuals in backing up their data, often with only a few clicks of the mouse. Carbonite boasts that they are automatic, secure, and affordable with plans starting at $59 per year. Many of our clients have also been happy using Mozy for their backup vendor. Another great service is Crashplan, whose plans start at less than $20 a year.
2. Cloud-based Document Storage Services
For documents that you are constantly using and changing, you may want to consider a cloud storage option, such as Google Drive or Dropbox. Both of these options offer two-step verification for added security, as well as a small amount of free storage. More storage space is also available for purchase from both of these vendors.
3. Self-service Storage
If a paid service doesn’t fit your budget, you can also backup your data yourself. Technology retailers have storage devices available for purchase and you can talk to a customer service representative to decide which storage device is right for you. The only downside to this is, of course, that you have to actually remember to back up your data on a regular basis.
How do website vendors protect your data?
Our staff here at Appletree MediaWorks, LLC has seen viruses take out websites before, we’ve seen malicious activity cripple a site and we’ve seen website plugin updates wreak havoc on entire websites, but in the end it all came down to restoring the website and databases from backup. We keep your website and databases backed up nightly and the information is always stored in a safe place. As for the rest of the data and pictures on your personal computer; please see our advice above or give us a call, we’d be happy to one of our developers help you setup a backup plan.
Then you won’t have to ask the question, how do I recover my data after a computer crash?
UPS Stores and Banks Were Hacked
UPS Stores were hacked
UPS stores were hacked in a data breach recently, with stores in 24 states subject to the data breach between March 26 and August 11. “No fraud has yet been discovered, UPS said, but customer names, postal addresses, email addresses and payment card information were compromised. ”
Banks hit by Hackers
Several large banks, including JP Morgan Chase & Co., which lead to theft of data associated with accounts. The theft involved significant amounts of data which could potentially lead to serious financial fraud.
IMAP vs POP Mail
IMAP vs POP Mail: Your Choices for Accessing Emails
If you use computer-based email clients like Microsoft Outlook, or you have a web host that gives you email addresses, you may have heard these terms. Their use is pretty straightforward – you plug in the right info, and emails come to your email client for you to read. But just what IS IMAP and POP, and what is the difference? Which one should you choose? Read on for more info!
POP Mail
POP stands for “Post Office Protocol” and this works by downloading your emails, images, and attachments to your computer and Outlook. Once an email message is downloaded, it’s there on your computer, although you can have the server store copies online as well if you wish to access your mail from a webmail client, or another computer. The result here is that the messages will stay on the server and re-download to the new client.
IMAP Mail
IMAP means “Internet Message Access Protocol.” Where POP downloads the emails to your computer, IMAP effectively allows the client to view emails while they are on the server. This means that what you view from your client will be the same from different computers. If you move email messages or delete things, you are deleting them from the server itself. If you leave emails alone, there they stay.
Which Is Better?
The decision to use POP or IMAP depends heavily on your intended use for email. Do you plan on accessing your email from just one computer? Or you may have to access your email at times that you don’t have internet access? POP is the best choice here, since everything just downloads straight to Outlook, or your client of choice.
On the other hand, if you access your email from your phone, your tablet, your laptop, and your office computer, IMAP is almost certainly the way you’re going to want to go. Managing email on multiple devices can be overwhelming – you do not want to view and delete multiple copies of sent and received email. However, if you need to access things away from the internet you may not have access to all prior messages, images, and attachments if you’re using IMAP settings.
Where Does Web Mail Come In?
Web mail – be it your own host, or Gmail, Yahoo, or any other web mail client – is email that you access from an internet browser. You open Internet Explorer or your web browser of choice, go to the webpage, log in your credentials, and view your emails from there.
This email is essentially sitting on the server until you do something to it and is accessible only if you are on the internet. Additionally, many of these services give you optional POP or IMAP access. Plug the appropriate info (which the client’s website will generally provide) into your computer or phone’s email client, and you can use these web mail clients there as well.
Remember that in the case of POP mail, unless you make a point to leave things on the server, everything will empty from your web email’s mailbox onto your computer. In the case of IMAP? Whatever you do in your web mail will be reflected in Outlook or Windows Live Mail, and vice-versa.
More than a Billion Passwords Stolen by Russian Gang
Ready to change your passwords again?
If you didn’t bother changing your password when you heard about “Heartbleed” leaking out passwords, you might want to consider changing your online passwords today. In the largest known collection of stolen internet credentials, a Russian tech gang has reportedly acquired an estimated 1.2 billion username and password combinations, along with over 500 email addresses.
A security firm based out of Milwaukee, Wisconsin conducted an 18 month study of the security breach. It has not announced specific sites that were hit, citing non-disclosure agreements and concerns for websites that still may still be vulnerable. An independent security expert confirmed the claims as authentic.
The hackers used unsuspecting zombie computers with viruses to allow a single operator to control a large group of virus infected computers to test for SQL vulnerabilities on servers.
When vulnerability was discovered on a website or server, hackers then executed SQL injections to send malicious commands to the website. In this way they were able to collect databases full of user names and passwords. Small and large websites have been affected worldwide by this hack.
So far, the stolen data has only been sold in small quantities on the black market, and used to access social media to send out spam messages. Hold Security had originally offered to check security breaches for a fee of $120 but seem to be revising their efforts after some criticism.
So what’s a person to do when it seems like keeping data secret is a losing battle?
- Change your passwords, and make sure they are strong, secure passwords with capital letters, lower case letters, numbers, and special characters.
- Businesses should run a check with the webmaster to see if their websites are vulnerable to SQL attack.
- Don’t use the same username/password combination for all the sites you access, particularly important ones like banking.
- Don’t panic, and have a plan in place in case you are a victim of data theft.
For more information on keeping your data secure, visit our blog posts on Heartbleed, and Preventing your Email from Getting Hacked. Or you can contact us here at Appletree MediaWorks for more information.
Internet and Security Updates
Heartbleed Followup
Lest you think the Heartbleed concerns were merely a false alarm: 4.5 Million Patient records were stolen by hackers, presumably due to the exploit.
The hackers took advantage by finding a device that had not been patched, exploiting the bug in order to steal user credentials. They used this data later to login into the network of Community Health Systems and captured patient names, phone numbers and social security numbers.
If you are concerned that your information might be among what was stolen, our recommendation is to invest in an identity monitoring type program or to lock down your credit report so that credit cannot be opened in your name.
As we’ve said before… Update your passwords often. Keep them unique – do not use the same passwords for every online account you own. Make them challenging – include numbers, letters, different cases, and symbols if allowed. Use password management software to keep track of all this. And it is always a good idea to keep an eye on your credit report.
More Data Theft from Stores
Unrelated to Heartbleed, SuperValu, the Minnesota parent company of Cub Foods, Farm Fresh, Hornbacher’s, Shop ’n Save, and Shoppers Food and Pharmacy, Albertsons, Jewel-Osco, announced that 180 stores in North Carolina, Maryland, Virginia, Illinois, Missouri, North Dakota, and Minnesota were affected. The stores are reporting they quickly fixed the security breach and it’s safe to use credit cards in their stores again.
There’s no sign yet of the data being sold on the black markets. Credit card data is said to be selling at $20-100 per card, often purchased in bulk as one-time use.
It’s always a good idea to keep track of credit card statements; credit cards carry theft protection, and if theft is detected they should be contacted quickly as possible. It’s also wise to prepare for data and identity theft in advance, with the assumption that it will eventually happen. Make a plan of action: Contact credit-reporting agencies, get a copy of your credit report, and in the case of identity theft, file an identity theft report.
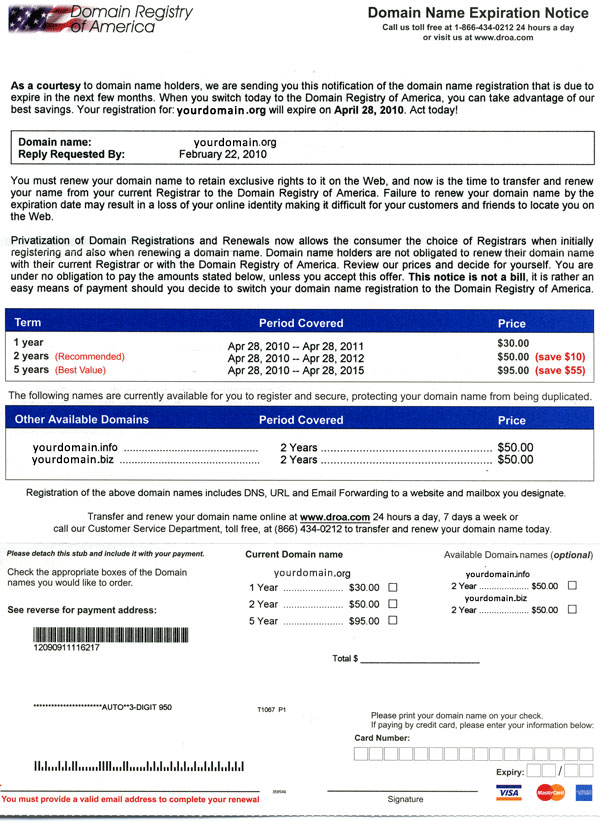
Domain Registry of America and Domain Slamming
Domain Registry of America and Domain Slamming
If you have ever registered a domain name of your own, you may have received an alarming letter or ‘bill’ alerting you that your domain name is about to expire, and giving you an ‘easy way’ to renew it. The letters look legit at first glance. But checking with your host will usually indicate your domain is fine and does not need an urgent renewal. Even if it does, you can do so through your registrar for the normal price.
So what gives?
Is this a scam? How did they get that info, and is this even legal?
The answers are a little nebulous, like so many scams. We’ll shed some light on just what is going on here.
Domain Registry of America (among other names) is a borderline-legal scam designed to convince you to switch your web hosting for inflated prices. The company itself generally has a post office box in the United States, but seems to have other addresses in other countries and is presumed to come from abroad. This makes the legality more difficult.
Your postal address and information is obtained from “WHOIS,” a public database of registered domain names. The letter is not actually a bill, but carefully written document designed to persuade the domain owner to switch domain hosting to their company at highly inflated prices.
What to do?
If you receive one of these notices, the best thing to do is just ignore it. But let’s go into some detail on how you can be SURE you are not going to lose your domain name.
1) Know the name of your registrar. The registrar may or may not be the same as your web host, but know who your domain is registered through. If you get notices from anyone other than your registrar, you can generally dismiss and ignore them. As a note, your domain name and host may not expire at the same time.
2) Know when your domain name expires. This can save you the potential loss of a domain name and all the trouble that comes with that, and it can also spare you quite a bit of anxiety, wondering when the expiration date is going to happen. Some companies will email you to let you know, but it’s good to remember this anyway.
3) Put your domain name on autorenewal if at all possible. You can’t just do this and forget it – credit cards expire as well, and it’s good to check up on things, but if your domain is set to autorenewal it’s less likely to slip past you.
What happens if you lose your domain name?
Other than purchasing it back for generally much higher costs, there are not a lot of options after losing a domain name, beyond getting a new one, changing your business card and information everywhere, and making up for lost emails. The single best option is to educate yourself, not fall for the scams, to keep track of your own domain name renewal so as not to risk losing it to begin with.
Don’t let Domain Registry of America alarm you. This and many other scams are out to make a dollar (or many). Education is key. When you know what you’re reading, you know what you can ignore. And for more information on various scams, visit us here at Appletree MediaWorks.
Unions Need to Cover All Their Bases Online for a Grand Slam in Communications
Union Web Communication
First Base – a Website
Every local or organization needs a website to be the backbone and the known area for accessing information. Things move quickly through a social media page, but your membership will know it can always check the website for complete information on events and other local happenings.
Unions and organizations should be filling their website with the positive actions and photos of their membership. Big media prefers to post the negative about unions because it sells. So unions need to showcase their positive contributions. Your membership’s local action in giving back to the community should always be shared on your website. Every event, no matter how small should be shared on your website.
Always encourage participants to take pictures at events and ask them to email them to you or post them to your social media page so they can be transferred over to the website too. Website articles are more likely to be picked up by search engines than short social media posts. Writing articles doesn’t require a degree in journalism, just cover the who, what, where, why and when about the event and you’ll have a couple of paragraphs to go with your pictures. Putting a couple of minutes into Search Engine Optimization is worth it, too.
Posting articles to a website also shouldn’t require a college degree in web development. When we make a website for an organization we make it easy for their committees to post articles, even from their phones!
Second Base – Email Newsletters
Asking your membership to sign up for your email alerts should be a priority. Sending emails to your organization can be done for free using programs like Mail Chimp. Other low cost solutions include Vertical Response or Constant Contact. Emails are great for announcements and keeping your local up to date. Remember to keep emails short and your pictures small in size for your mobile readers. Instead of putting long articles in an email, offer an excerpt and a link to the article on your website.
A big win is that you can limit your email list to include only your membership, unlike most social media or a website where the public can view messages.
Third Base – Social Media
Right now, the top 5 Social Media Sites are Facebook, Twitter, LinkedIn, Pinterest, and Google+. The trick to unions using social media is to create an article on your website, then share it on your social media outlets and watch it spread virally. A good website setup includes automatic “share” buttons, so once an article is posted, its just a matter of clicking a button to share the post out to your social media channels.
Home Run – Communication Management
Managing all these communication outlets can be overwhelming. We recommend having a specific staff member or officer be your communications leader, and then set up a general email box for your membership to send their news to. From there, website posts can be scheduled in programs like WordPress. Emails can be scheduled in programs like Vertical Response and social media can be scheduled using Hootsuite or other social media management platforms. There you have it – a grand slam in online communications, and none of these tools are costly, most of them are free. If you’re looking for more information on any of these communication tools or you’d like a quote on a website for your union or organization, the Appletree Mediaworks is ready to explore your needs in depth and build a plan to achieve your goals.
An Extra RBI:
Keep your eye on the new, fast growing social media sites that focus on people meeting new people with similar interests including Tagged, Meet Me, and Meetup. We’ve got our eye on Meetup where groups of people with similar interests in a local area can make plans to participate in their hobby together. This could be big for unions to come together in a local area to make a huge impact.
For more information on union web communication, contact us – we can answer any questions you have!
Ebizmba.com, (2014). Top 15 Most Popular Social Networking Sites. [online] Available at: http://www.ebizmba.com/articles/social-networking-websites[Accessed 8 May. 2014].
Cat Tech Tips: Cleaning the Computer
 Cleaning the Computer
Cleaning the Computer
Dust collects around electronics. You may notice this when you dust around the TV or DVD player, or even around the computer. Have you stopped to think about how much dust collects inside that desktop computer of yours?
You might be shocked to find out just how much dust – and pet hair – has accumulated on the fans and internal components, trapping in heat around the fans that are supposed to keep the machine cool.
Canned air can be purchased at most places that sell electronics, and dusting out the back fan and the vents is a good step in the right direction.
If you are feeling particularly ambitious and brave, you can even crack that computer open to witness the horror which lurks inside. If you choose to do this, grab a dust mask and read through these tips first.
We are not responsible for any foolishness resulting from possessing canned air, owning vacuum cleaners, or taking apart an expensive machine. But if you are careful, and with proper maintenance, you’ll improve the health and life of your computer.
- Turn off and unplug your computer and all the parts. For that matter, pull the whole thing out of its home at your desk, and clean up around it while you’re at it. It’s probably gotten a bit dusty down there anyway and could use the clean.
- Make sure you are aware of static discharge and do not touch the insides of your computer if you can avoid it. Touch the metal casing outside first either way.
- Canned air and a clean, dry paint brush are good tools to get those dust bunnies, pet hair, and the rest of that mess out of your machine. Keep the area ventilated – you will kick up a lot of dust. Your contact lenses may suffer.
- Hold the canned air right-side-up and don’t spray too close to your components – the liquid inside is very cold and may cause damage. (And on that note, do not spray the canned air on your friends, pets, etc. The temptation may be strong, but don’t do it.)
- Don’t use a vacuum until you’re cleaning up the floor afterwards, and definitely not on the computer’s innards. To repeat, static is bad and your vacuum kicks up a lot of it.
Heartbleed
What Heartbleed is, and What You Should Do
What is it?
Heartbleed sounds scary by the name alone. It’s all over the news, but just what is it? What should the average Internet user do about it? Heartbleed is complicated and involves some Internet security understanding, but here we’ll strip out most of those details and get to the essentials.
Heartbleed is a bug – a mistake in security code – that has potentially allowed in-the-know hackers to exploit the problem and grab unencrypted usernames, emails, passwords, and other random sensitive information a bit at a time through small packets of data, nicknamed “heartbeats.” The bug has been around for two years, but it was only just discovered by companies Codenomicon and Google.
Who is Affected
Any “secure” website using the security software OpenSSL which had the buggy code (an update within the last two years) could potentially be compromised. Nobody knows for sure if they HAVE been compromised. It is possible that up to two thirds of the web could have this bug. There are a lot of unknowns.
Some big websites may have been affected: Yahoo, Google , and Facebook. Though these websites have already updated their software, they suggest that users still take the time to change their passwords.
Some websites never used the vulnerable software: big banks were less likely to use the open source software, Microsoft said it was unaffected, and LinkedIn seems to have been safe.
Why Should You Be Worried?
You should be worried because if someone has exploited the bug, your usernames, emails, passwords, security questions, and other sensitive information could have been available to malicious users for the past two years. If you use the same passwords (or similar passwords) on multiple sites, this could give them access to those other websites as well.
If a website with the compromised code does not update, they are still an open gate. If a website has updated but you have not changed your password, someone might have that info to use when they see fit – if someone has grabbed that info in the past, they still have it.
We don’t know how extensive the problem is – entire website databases could have been compromised. The good news is that the bug was brought it to our attention rapidly after it was discovered, allowing word to get out before the bug was exploited on a wider scale.
Recommendations
There is only so much a user can do. The biggest problems lie on the website side of things, and it is the responsibility of those website owners to update their keys. If the website has not run updates on their side, the bug can still be exploited even if you change your passwords.
Most big companies updated their software right away and recommend changing your passwords. Unfortunately, not all companies are being clear about whether or not they were vulnerable to the problem, and if they have since patched the bug.
Our recommendations are to do the following:
- Update your passwords on all of the websites you use, especially ones where you store sensitive or personal information.
- Make sure all your passwords are different – do not use the same one for each website.
- Be prepared to change your passwords again in case a site has been slow to update.
Best Practices Going Forward
It’s hard to remember many complicated passwords (and complicated passwords are the most secure), so we recommend using a program like LastPass or KeePass to keep track. While nothing is entirely failsafe, they are a lot more secure than trying to remember many simple passwords or even worse, using the same password everywhere.
It is also good practice to update your passwords periodically.
When, Not If
The internet is complex and only getting more so, and for better or worse much of it is unregulated. When it comes to any kind of security breach or data theft, expect that something could potentially happen, and work out a plan for what to do when it does.
Follow Appletree Mediaworks on Twitter or like us on Facebook. Visit our website for more information on data and security and what to do about breaches, and about what’s happening on the web.
—–
Common Sites You Should Change Your Passwords For
Password Changes Suggested (They have updated their SSL)
Facebook
Tumblr
Google/Gmail
Yahoo
Turbotax
Dropbox
SoundCloud
Okay/Don’t need to change passwords*:
LinkedIn
Amazon
AOL
Outlook/Hotmail
Paypal
Target
Most big banks
Taxes/Accounting sites (except Turbotax)
Evernote
Unclear: (Have not made an official statement – they claim to be okay, in some cases)
Twitter
Apple
Ebay
Netflix
* It can’t hurt to change your passwords anyway. Just be prepared to do it again if necessary.
Technical Details of Heartbleed: http://heartbleed.com/











