Websites and the CryptoPHP Infection
 Could Your Site Be Infected?
Could Your Site Be Infected?
If your website uses a content management system such as WordPress, Joomla, or Drupal, you will want to be aware of the CryptoPHP infection. Like many infections of this nature, the CryptoPHP infection is both sneaky, and can spread the maliciousness once it’s there, so it’s good to be aware of it if you may have the potential to encounter it.
So Just What Is it?
CryptoPHP is an infection that works like a botnet. It is a sophisticated program that uses your website to conduct illegal “black-hat” SEO tactics such as adding links to other, possibly malicious websites. It can also upgrade itself, and since it communicates with other servers it can update itself and behave as a drone that could do anything from sending spam to attacking other sites.
How Do You Get it?
CryptoPHP is acquired by downloading and installing a theme to their WordPress, Joomla, or Drupal site – specifically a free theme found online. The infected theme has a nulled script that contains a line of code that appears to include PHP but instead appears to call on an image. Hidden inside the image is the real, malicious code.
How Can I Prevent It?
There are a few simple ways to avoid infection:
- Don’t use free downloaded themes on your site – it is difficult to tell what is infected and what is not.
- Don’t accumulate extra “unused” themes just sitting around on your site. It’s easy to collect dozens of these while trying them out, but best to reduce this number as much as possible. Your current theme and ones in development are all you really need.
- The sites we here at Appletree Mediaworks LLC create are CryptoPHP-free.
How To Know If You’re Infected
For WordPress: Install the Wordfence plugin and enable the option to scan images – CryptoPHP hides in a png image, but is actually obfuscated code. This will detect the infection.
Other sites: Download all source code and search for this line:
<?php include(‘assets/images/social.png’); ?>
Our sites here at Appletree MediaWorks LLC are CryptoPHP-free. If you have concerns over your own sites, or have any questions on keeping your website up to date and secure, contact us or visit our blog for more information.
—
For More Information on CryptoPHP – http://www.wordfence.com/blog/2014/11/wordpress-security-nulled-scripts-cryptophp-infection/
How to Clean Up Your Computer
 Have you ever noticed your computer starting to run slower for no apparent reason? Does Windows seem to take a while to boot up when it has no business crawling along like that? Has your browser become bogged down with a half-dozen tool bars of dubious origin?
Have you ever noticed your computer starting to run slower for no apparent reason? Does Windows seem to take a while to boot up when it has no business crawling along like that? Has your browser become bogged down with a half-dozen tool bars of dubious origin?
Keeping your computer cleaned up is not always something that comes to mind, but a little regular maintenance will keep it running smoothly.
Virus Protection
All PCs should have some form of virus protection and most, in fact, do. Newly purchased computers might come with McAfee or Norton Antivirus, but these programs often have special features that are free for a limited time, but then proceed to nag you once they expire. Fortunately, there are several free and reliable antivirus programs available, including Avast and AVG. Microsoft also distributes Microsoft Essentials for free, which runs quietly and discreetly in the background.
Whatever you decide to do, make sure to uninstall any antivirus program you may already have before installing another – doubling up on antivirus software can create more problems than it prevents. If your computer is sluggish, check to make sure that you have only one antivirus program installed.
Your job is to make sure your antivirus is running, up to date, and scheduled to scan regularly.
Popup Blockers
Most browsers come with popup blockers, but malware often finds its way in through ads, so installing an add-on such as Adblock Plus can reduce the likelihood of malicious advertising infecting your computer. However, do not go overboard with the addons. Occasionally, legitimate plugins will be purchased and compromised by shifty companies that use them to inject malware into your computer. Consider each plugin wisely, and uninstall them when you don’t need them anymore.
Anti-Malware Software
I know what you’re thinking – what is this and what about the antivirus software? The problem with malicious programs is that there are many kinds, and they evolve and change, so that old protection software may not catch everything. Further, there are many kinds – from tracking spyware to software that hijacks your browser. While doubling up on antivirus software may do more harm than good, having secondary anti-malware software does help – this is where MalwareBytes comes in.
MalwareBytes should be updated and run on a regular basis. It digs out things that your antivirus might not have caught, and then may ask to reset your computer to further dislodge any bad software it finds. Let it do its job – it’s one of the better pieces of software out there.
Taking Out the Trash
Another handy piece of software for keeping your computer running smoothly, CCleaner will get rid of old temporary files, history files, clean up the remains of uninstalled software, and much more. It also has an option to uninstall software you don’t need any more and makes it easy to deactivate programs that run in the background, eating up valuable system resources.
Deactivating software that runs in the background when your computer first starts up will speed up the process drastically. Be careful with this tool because you might need unexpected things (your antivirus software, some drivers and video software) – but do you really need parts of Adobe Acrobat checking for updates every time you turn on the computer? Probably not.
Driver Updates
Speaking of updates – drivers rarely bother you, but they can benefit from occasional updates as well. Updating your hardware drivers can boost computer performance and keep things running smoothly, especially in an older computer. Slimdrivers is a free program that will scan your computer and detect when drivers need updating. It will even download the correct drivers and initiate the update process without having to leave the program.
Software Updates
A lot of your software will update automatically, but it is still a good idea to keep track of what’s been updated, and manually update what is behind. Windows, Firefox, Chrome, and IE can be checked for updates. Flash, Acrobat, and Java will prompt you for updates, quite frequently. Go ahead and update them as they come in. Updates often patch security holes.
Defrag, Defrag, Defrag
When you’re all done, defrag that thing. Defrag is part of Windows (though you can get better or more visually appealing versions of the software). It crunches together fragmented files, giving your computer a little added boost. If you’re using a Mac, fire up Disk Utility and Verify and Repair your disk permissions.
Dust That Thing
If you’re feeling bold and don’t mind cracking your desktop computer open, get some canned air and dust out the machine. You’ll be amazed (and maybe a little scared) at just how much dust gathers on electronics – dust gums up the works and holds in heat that your computer does not need.
Be smart about it though – if your computer is under warranty you may not want to go meddling around inside. Warranties aside, always make sure the computer is unplugged before prying open the case. It also helps to ground yourself on something so you don’t inadvertently shock some delicate computer chip with a static charge from your finger. Also, remember that you’re messing with delicate electronic equipment. You don’t want to bring an industrial shop vac to the machine (yes, sadly, this has been done). It is possible to knock things loose if you bump or nudge cards or cords, so make sure they are seated properly before closing everything back up.
While you’re at it, take a look at that keyboard. It may need a little more than canned air.
Wrapping It All Up
Once everything is taken care of, it never hurts to create a backup or restore point, in case something malicious does find its way onto your computer. Along with good practices for keeping nuisance programs off your computer (I’m looking at you, toolbars and ‘free games’), regularly cleaning your computer can keep it running smoothly for years.
Net Neutrality in a Nutshell
[iconsweet icon=”megaphone” color=”black” size=”32″] Listen to Appletree MediaWorks talk about Net Neutrality on The Union Edge Radio Show.
What Is Net Neutrality?
Net Neutrality is the idea that internet providers should treat all internet traffic the same way, wherever it comes from-whether it be a corporation like Google or Netflix, a small business website, or a start up. ISPs should not be able to charge more for access to certain services or create tiered systems that allow access to certain data and block or throttle others. Internet providers claim they are not against Net Neutrality, but their actions have shown otherwise.
Why Is This a Problem?
The current proposed two-tier system would allow that companies which can afford it would have access to an internet ‘fast lane.” The concern is that this would hurt startups and innovation and companies that do not have the resources to spend on the fast lane would be left with the slow lane where their ideas may never get off the ground.
Internet provider companies are dabbling in this already. Early last year, Verizon successfully challenged a court case that allowed it to disregard FCC regulations regarding blocking or ‘discrimination’ of internet traffic.
Broadband providers are classified as “information services” and NOT “common carriers” so the FCC lacks legal authority to regulate them as they do radio and television. If an ISP were classified as a common carrier instead, this would allow the FCC to ban “paid prioritization” or otherwise set rules in place.
Is It a Real Concern?
Companies have already gone the paid prioritization route. As a recent and noteworthy example, streaming media like Netflix and Hulu use large amounts of bandwidth. Comcast had been throttling Netflix – speeds declined nearly 30 percent – until Netflix agreed to pay up. Some agreed that Netflix should pay up due to higher bandwidth use – others disagreed and called this out as extortion and an abuse by the ISP.
Who Is For It? Who Is Against It?
Generally speaking, if you are a streaming service or use streaming services, run websites, use things like Facebook and Google, or ARE companies like Facebook or Google, you tend to be Pro-Net Neutrality. If you distrust the cable companies, think the upcoming Comcast/Time-Warner deal is too monopolistic, and want the internet to keep functioning as it has been, you are pro-Net Neutrality.
If you are a large ISP such as Verizon, Time Warner, or Comcast you are against Net Neutrality. If you heavily promote free market ideals and believe the market should work itself out, or if you have more distrust of the federal government than large telecom and cable companies, you tend to question Net Neutrality.
The President Steps In
The Net Neutrality issue has been contentious, with the FCC soliciting opinions from all manner of users on the FCC website.
Then early this week President Obama stepped up officially in favor of Net Neutrality, asking the FCC to classify it as a public utility. Obama has asked for the internet to be treated with regulatory protections as if it were classified under the Title II of Telecommunications Act. He has presented a four-tier plan: No blocking, no throttling, increased transparency, no paid prioritization.
President Obama, even if he appointed FCC Chairman Wheeler to the position, has no control directly over the FCC. Wheeler has balked at the suggestions, expressing frustration at the President’s statements. The FCC Chairman likely sees himself as being between a rock and a hard place, being a former lobbyist for the cable industry and longtime supporter for Obama campaigns. The FCC is unlikely to make a decision until 2015.
What Does This Mean For Us?
The internet may change as we know it, but nobody is quite sure on the long term ramifications. It may be harder to access specific sites, they may be slower. Startups may not have the opportunity to get off the ground. Cable companies say nothing will be slowed or throttled (we have seen this to be false) – just sped up in the case of the faster lane. We may have to pay for premium internet packages which permit us access to certain internet features, or menus of selected features. This is only speculation.
Specifically, concerns that Net Neutrality fail include: degraded service, higher costs, less innovation, uneven service (faster for some, slower for others – a local media outlet might have more trouble), greater technological divide by income and demographic.
What You Can Do
The best thing you can do is contact the FCC – you can go to their website and contact them online or call them. Write or call your members of congress. And learn more about the issue, become informed, and speak out. Savetheinternet.com has information on actions you can take.
[iconsweet icon=”megaphone” color=”black” size=”32″] Listen to Katie Dexter talk about Net Neutrality on The Union Edge Radio Show.
More Info
http://www.cnbc.com/id/102173519
http://gawker.com/what-is-net-neturality-and-why-should-i-care-the-non-g-1657354551
http://www.webpronews.com/obama-asks-fcc-to-reclassify-the-internet-2014-11
How to Avoid Getting Your Email Hacked
How Do You Avoid Getting Your Email Hacked?
- Duplicating usernames and passwords is risky. If you use the same username or password on several different websites, only one of those sites being compromised can make all of your accounts vulnerable. Many hackers use brute force or dictionary attacks in which a program is set up to attempt countless password combinations rapidly. The simpler your password, the easier it will be to “guess” by the program.
- Suggestions: Set up unique login credentials on each website or service you use, making sure to create complex passwords. To remember all of them, use a program or service such as 1Password, LastPass, or KeePass to help manage and keep track of your information. Once you’re set up with a password manager, creating 40-character passwords (and never forgetting them) becomes a breeze!
- Keep your software up to date. Out of date software is risky, especially when it comes to web browsers, browser plugins, and other web-based software. Make sure to keep your operating system and antivirus software up to date. Run anti-spyware programs regularly.
- Suggestions: Many programs update automatically. Still, it is a good idea to set your phone or calendar to remind you to check on these things every few weeks.
- Pay Attention to Login Sessions. Make sure that you are the only person logging into your accounts. You can often monitor recent activity with popular online services such as Facebook and Gmail.
- Suggestions: Change your passwords if things seem fishy. Do not create obvious security questions that people can find the answers to simply by searching Facebook or other sites.
- Think Before You Click! If you receive an ambiguous or unexpected email asking you to click a link, even if it appears to come from a relative or close friend – don’t do it. Contact the person over the phone and ask whether or not they actually sent it. The same goes for attachments.
- Suggestions: Ignore and delete emails like this, even if they appear to come from friends, family, or banks. Don’t click the link or open the attachment – it’s a surefire way to get your info stolen.
- Watch where you log in from. Be careful if you are logging in from a public computer or a network that is not secure. Be sure to log out of any services you used and clear the browser’s cache before walking away from any public computer.
- If Two-Step Authentication is an option, use it! Two-step authentication often requires an extra step, such as inputting a code you are texted, particularly on a new machine. If your email service has this feature, it may very well be worth the effort.
Know that none of this is absolutely foolproof as identity theft and account hacking becomes more rampant. It is best to set up your accounts so that if one gets compromised, the rest remain secure. Have a plan set up for what to do if an email gets hacked or a credit card gets stolen. Keep in mind that this is an extremely common, if problematic.
If your account gets hacked:
- Scan your computer for viruses, malware, and keystroke loggers. It is important to do this first before changing passwords, or the same problem could occur again if your computer itself has been compromised.
- Change your passwords and security questions if you can still access your account.
- If you cannot access your account, follow the directions in the site’s help center – most sites have guides about what to do.
- Report the incident. You may get access to identity protection services through the site.
- Let people know you got hacked and not to click any links appearing to come from you until the problem has been sorted out.
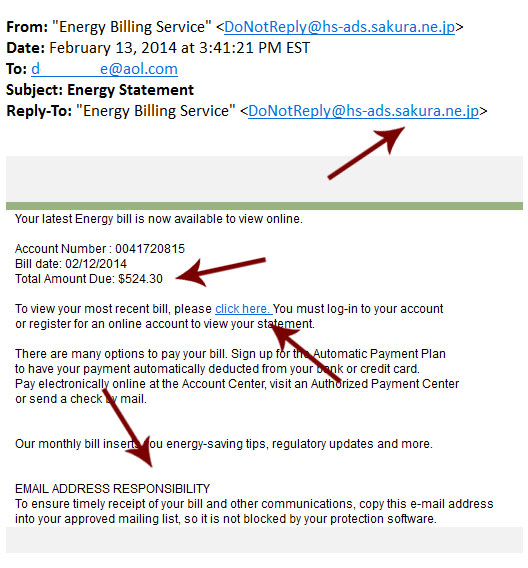
Scams: Energy Bill Service Scam
Lets Have A Look At An Energy Bill Service Scam
Here we have a classic scam email captured in its natural environment, which presents a good opportunity to learn how to spot them. This one is rather straightforward and deceptive. Note the alarming nature of the email, intent on distracting attention away from the fact that your “energy bill” is being sent from Japan. It is worth noting that email addresses are notoriously easy to spoof, so it won’t always be so obvious. Scam emails can just as easily appear as if they came from a legitimate source.
A better tell might be the obligatory “click here” link. If you hover over it with your mouse, the link itself is suspicious – the URL has nothing to do with an energy company. Link targets are much more difficult to fake, but can sometimes look very similar to a more legitimate address, so look closely!
This scammer even has the nerve to instruct you to add their email address to your approved mailing list so that future scams won’t be blocked by your spam filter. It is never a good idea to do this unless you are 100% certain the email is legit.
As always, if you receive an email like this, do not immediately click on the link. Instead, open up your web browser separately and navigate to your actual utilities company’s website if you are concerned. Delete the email and go about your normal business.
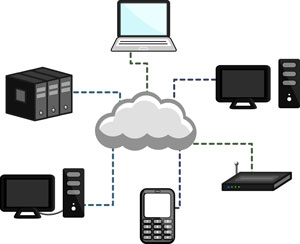
The Good and the Bad of Cloud Computing
Cloud Computing
Cloud computing seems inescapable. Phones and devices have cloud servers for files, any user can get free cloud backups for their own computers, and even federal and state governments are investing in cloud computing for their own data. But just what is it, and is it safe?
What Is It?
First, we had computers that had hard drives with information and programs on them, and then we used discs to move that information from computer to the next. These discs were small, so we took to thumb drives, but this was problematic if you forgot your thumb drive at home or work or school. Those of us who had web mail account like Yahoo or Hotmail recognized we could just email ourselves the data, and open it from wherever.
This was the early stage of Cloud Computing.
Cloud computing is the practice of using a network of remote servers hosted on the internet to store and manage data, rather than a local server, or a personal computer. Given that few of us stick to just one computer these days –between home, work, school, laptops, tablets, and other devices – having ready access to that information on any device is important. This is where cloud computing comes in.
Where is it stored?
Cloud computing is named as such because information or even programs are used or run from a number of application or storage servers kept and backed up off site, and accessed through multiple computers where the user logs into an interface for access. A simple example of this is web-based email which is accessible through a web browser and website, but available through any computer.
Individuals and companies often resort to third-party cloud storage, such as iCloud, Dropbox, Google Drive and others. Companies may wish to back up not only files, but whole computers, databases, or programs for use.
When are people going to use this tech?
This sort of technology has been used since the ‘90s when people backed up files on web hosts or used web-based email clients. With the ever increasing use of mobile computing, cloud hosting has become more prevalent and will continue to do so for the foreseeable future.
Why is this needed?
The more mobile people become with their computing, the more important it will be to have access to files, data, and programs remotely. While devices and computers have ever-increasingly large hard drives and can hold more info, hauling around secondary drives and copying information over is redundant and unnecessary.
For companies and industries, a base location for all information is valuable in the interests of saving money and time. Instead of a slowly depreciating server under a desk or stuck in the back room, all information is available and reliably backed up offsite. This also allows for people in multiple locations, branches, or buildings, to have access to and immediately update information as needed.
What are the potential pitfalls and drawbacks?
Cloud computing has some very real drawbacks and concerns, and some of them do not have good solutions at this time:
- Access: To access the cloud (whatever form of cloud you are accessing at the moment), the user needs internet access. Without wifi or otherwise, access to files and software severely limits what can be done. This is becoming less and less a problem as time goes on, but still could come up as an issue.
- Security: Every day the news broadcasts another company or institution getting hacked. And as security gets more sophisticated, hackers always seem one step ahead. Information could be accessed and stolen during a number of points in the cloud computing process, whether it be a hacker discovering a means of getting in, or a user with a weak password.
- Privacy: Housing your data somewhere on the web inevitably means someone else may have access to it. Along with the aforementioned hackers, NSA access to various servers and databases has been argued and discussed extensively throughout the last year. While a company may not have anything to hide, they may not want that data accessible in general.
- Third Party Control: Ultimately, in handing over data and programs to a third party, a company or institution is handing the keys over to someone else. Not everyone likes this or feels comfortable with it, and would prefer to have complete control over their information.
Despite the potential hazards of cloud computing, large companies and even government and official institutions more and more are turning in that direction due to reduced costs and ease of use. The debate and concern over the security of private information will only increase as hackers are more sophisticated and computing becomes more ubiquitous. But cloud computing is not going away any time soon.
For more information on cloud computing and internet security in general, follow the Appletree Media blog.
More On Cloud Computing:
http://computer.howstuffworks.com/cloud-computing/cloud-computing.htm
http://www.moneycrashers.com/cloud-computing-basics/
http://www.thefiscaltimes.com/2014/10/14/States-Turn-Cloud-Computing-Cost-Savings
http://www.whitehouse.gov/sites/default/files/omb/assets/egov_docs/25-point-implementation-plan-to-reform-federal-it.pdf
http://www.itproportal.com/2014/10/13/whitepaper-five-myths-cloud-computing/