EU-US Privacy Shield Still Not Protecting Your Privacy
EU-US Privacy Shield Still Not Protecting Your Privacy
Full text of the new draft EU-US Privacy Shield was released February 29th but has not been signed yet. They have made some changes from the previous Safe Harbor Agreement. While some are good improvements, some seem to have not changed how our data is handled at all. A conclusion on if the draft agreement will be acceptable should be made by mid-April to the end of April.
History: Safe Harbor Agreement
Before going in to the Privacy Shield here is the history of why we needed a new agreement between the European Union and United States. In an earlier blog, Safe Harbor Ruled Invalid, How it Affects You, we talked about the invalid ruling of the Safe Harbor Agreement and how it affected businesses and consumers. So here’s a little history on the old Safe Harbor Agreement:
The European Union (EU) and the United States (US) established the Safe Harbor Pact in 2000. This allowed businesses to legally funnel info across the Atlantic. Common data storage and transfers might include global commerce, sending and receiving emails, and even posting on social media. US companies can “self-certify” that they meet the stricter European privacy standards.
In early October of 2015, the European Court of Justice found the US approach to domestic surveillance and absence of legislation governing certain privacy rights was not up to European standards following a case brought by an Austrian student Max Schrems. The EU then made the Safe Harbor pact invalid. They believe the US has compromised their data and would like for some changes to happen to ensure the US is not spying on their citizens.
What’s New
 While there are some improvements to the Trans-Atlantic data transfer deal many say it does not differ much from the original Safe Harbor and does not address the “core concerns and fundamental flaws of US surveillance law and the lack of privacy protections under US law.”
While there are some improvements to the Trans-Atlantic data transfer deal many say it does not differ much from the original Safe Harbor and does not address the “core concerns and fundamental flaws of US surveillance law and the lack of privacy protections under US law.”
Key Positive Takeaways:
[space10]Citizen and Company Complaints
 The new agreement gives companies and citizens the chance to complain and dispute any mishandling of records and personal information. Governments must resolve such complaints within 45 days or use a free “alternative Dispute Resolution”.
The new agreement gives companies and citizens the chance to complain and dispute any mishandling of records and personal information. Governments must resolve such complaints within 45 days or use a free “alternative Dispute Resolution”.
Ombudsman
An ombudsman is a public advocate representing the interests of the public by investigating and addressing complaints. An ombudsman within the US State Department will handle any allegations of privacy violations.
Key Negative Takeaways:
[space10]Collecting Data in “Bulk”
In a Press Release from February 29th the European Commission states there will be “no indiscriminate or mass surveillance by national security authorities.” But then is contradicted by this:
6 exceptions where US can collect data “in bulk”:
- Detecting and countering certain activities of foreign powers
- Counterterrorism
- Counter-Proliferation
- Cybersecurity
- Detecting and countering threats to US or allied armed forces
- Combating transnational criminal threats, including sanctions evasion
US Judicial Redress Act
 In addition to the Privacy shield, President Obama signed the U.S. Judicial Redress Act on February 24th that will “give EU citizens access to US courts to enforce privacy rights in relation to personal data transferred to the U.S. for law enforcement purposes. ” […] The Judicial Redress Act will extend the rights U.S. citizens, and residents enjoy under the 1974 Privacy Act also to EU citizens.”
In addition to the Privacy shield, President Obama signed the U.S. Judicial Redress Act on February 24th that will “give EU citizens access to US courts to enforce privacy rights in relation to personal data transferred to the U.S. for law enforcement purposes. ” […] The Judicial Redress Act will extend the rights U.S. citizens, and residents enjoy under the 1974 Privacy Act also to EU citizens.”
At first that sounds good. After further research on the Privacy Act of 1974, many believe that the Privacy Act is “worthless”, with similar views from the Electronic Frontier Foundation (EFF),. There are many exceptions including 32 CFR 322.7 which exempts the NSA from rules of privacy on records maintained on individuals, according to 5 U.S. Code § 552a.
“Essential Equivalence” Non-Existent
 One of the most important parts of changing this agreement was to have “essential equivalence” of European data protection in the US. Max Schrems points out that this deal falls short:
One of the most important parts of changing this agreement was to have “essential equivalence” of European data protection in the US. Max Schrems points out that this deal falls short:
“The new deal does not even address the matter of private sector data misuse, despite the fact that there would have been much more leeway than in the government sector. There are tiny improvements, but the core rules on private data usage are miles away for EU law.”(TechCrunch)
 Privacy Shield Certified
Privacy Shield Certified
Under the Privacy Shield a business can become ‘certified’ to establish “adequate” protections for Trans-Atlantic data transfers. While this helps to protect your business from data transfer problems, it does not protect you completely.
The new agreement allows Data Protection Authorities (DPAs) to suspend data flow regardless of a business being Privacy Shield Certified. This would mean you cannot secure continuous data flow for your company.
The Outlook
 The EU-US Privacy Shield still needs to be approved by the EU’s WP29, also known as the Article 29 Working Party, and from the privacy issues others have already found in the draft it does not seem likely it will be approved.
The EU-US Privacy Shield still needs to be approved by the EU’s WP29, also known as the Article 29 Working Party, and from the privacy issues others have already found in the draft it does not seem likely it will be approved.
“They tried to put 10 layers of lipstick on a pig, but I doubt the court and the DPA’s now suddenly want to cuddle with it”
-Max Schrems
NSA Surveillance and Online Privacy
Who are the NSA?
The National Security Agency (NSA) is a powerful United States intelligence organization. Basically, they are responsible for collecting, processing, and monitoring global data for intelligence purposes. The NSA has a stated role to advance national security while protecting the freedoms, civil liberties, and privacy rights guaranteed by the Constitution and federal law.
What is the issue?
Many studies, cases, and documents show that the US government is spying on American citizens using online NSA surveillance. As Americans, this invades our Freedom of Speech and our Right to Privacy. The ACLU has called this activity “unconstitutional surveillance of Americans’ communications”.
Some Examples
An internal NSA audit from 2012 revealed they committed 2,776 incidents of unauthorized surveillance of Americans or foreign targets in the US over a one-year period.

On May 20, 2013, Edward Snowden released files from the NSA which described, as he put it, “systematic surveillance of innocent citizens.” Based on Snowden’s documents, the NSA has at least nine major tech companies gathering data on selected surveillance targets. This revelation caused online privacy concerns to increase dramatically in the US.
Then on Dec 24, 2014, a Freedom of Information lawsuit filed by the ACLU revealed NSA documents from 2001 to 2013. Overall, these documents showed that there were instances of unauthorized surveillance of US organizations, spouses or love interests, and more American citizens.
What is a Digital Pat Down?
The inner workings of an intelligence machine like the NSA can be difficult to grasp. From leaked documents so far, we can surmise that the NSA is performing secret “digital pat downs” on American citizens somewhat regularly. This happens without our knowledge or consent.
First, an NSA analyst identifies a target and submits a request to the FBI’s Data Intercept Technology Unit. Next, dedicated employees at various tech companies receive the request and gather the requisite data. This may include emails, chat logs, and videos. Once the data is compiled, it is sent back to the FBI for analysis.
The National Security Agency is also piggybacking on the tools that enable Internet advertisers to track consumers, using “cookies” and location data to pinpoint targets for government hacking and to bolster surveillance. We’ve talked in detail about mobile phone tracking tools previously.
They are also collecting location data transmitted by mobile apps. An NSA program, code-named HAPPYFOOT, helps the NSA to map Internet addresses to physical locations more precisely than is possible with traditional Internet geolocation services.
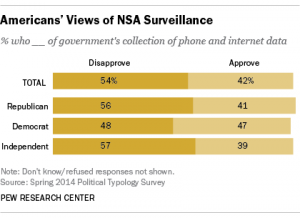 How do Americans feel?
How do Americans feel?
PEW research shows what Americans think about online privacy and the NSA.
Overall, 54% of Americans disapprove of the US Government collecting telephone and Internet data for anti-terrorism efforts.
74% said they should not give up their privacy and freedom for the sake of safety.
93% think it is important to control who can get their information.
38% think they have only some control over their own information.
Cyber Legislation
CISPA had alarmed the privacy community by giving companies the ability to share cyber security information with federal agencies, including the NSA, “notwithstanding any other provision of law.” That means CISPA’s information-sharing channel, created for responding quickly to hacks and breaches, could also provide a loophole in privacy laws that would enable warrant-less intelligence and surveillance. The information they gather, including all hacked data and any incidental information swept up in the process, would be added to a massive database. The FBI, CIA, and NSA would then be free to query this data at their leisure.
This is how CISPA would create a huge expansion of the “backdoor” search capabilities that the government uses to skirt the 4th Amendment and spy on Internet users without warrants and with virtually no oversight.
How to prevent being spied on by the NSA and other data collectors without going off the grid
It may be impossible to completely prevent the NSA from spying on you, but you can try and make it much harder.
- Avoid popular Online Consumer services – These include Google, Facebook, and DropBox.
- An alternative to DropBox is SpiderOak.
- A common alternatives to Google is DuckDuckGo.
- Mashable has published a list of private social networks to help you avoid the Facebook plague.
 Encrypt your hard drive – You may have password protection on your files but you should go a whole step further and encrypt the entire hard drive.
Encrypt your hard drive – You may have password protection on your files but you should go a whole step further and encrypt the entire hard drive.
- Avoid online tracking – On you browser you can use the do-not-track setting but you can go a step farther and use a plugin to stop tracking. Some reputable plugins for this include:
- Encrypt your email and chat messages – Encrypt your messages before you send them. Some common email clients with encryption include:
- Microsoft Outlook – This has encyption options if you want to use them.
- Runbox (a Norwegian secure email client) – Claims to be unreachable by the NSA.
- HushMail – Not as popular but is completely encypted.
If you chat on the Internet, you can encypt those messages too.
- ChatCrypt – Encrypts the message when it sends and can only be read by the end user, also known as end-to-end encryption.
If you use common instant messaging through Google, AOL, Yahoo or Microsoft you can use a chat extension called OTR (Off the record) which enables end-to-end encryption.
- Use TOR for online browsing – TOR stands for The Onion Router. Like an onion, it layers multiple levels of security. Basically, it bounces communication around a network of relays which makes it very difficult to track.
 Many browsers also have a private mode.
Many browsers also have a private mode.
- Firefox – Private Browsing
- Chrome – Incognito mode
- Internet Explorer – InPrivate feature
Online Privacy in Europe
A recent draft of the British Investigatory Powers Bill will require companies to store information for up to a year. Communications companies would hold details of which websites and apps a person uses.
 Recently, the European Union has decided to invalidate the current voluntary safe harbor because they believe the US cannot adequately protect its privacy. There have been reports that European companies are transferring data out of US territory for safe keeping.
Recently, the European Union has decided to invalidate the current voluntary safe harbor because they believe the US cannot adequately protect its privacy. There have been reports that European companies are transferring data out of US territory for safe keeping.
EU-US Privacy Shield
The US Government released full text of the new European Union-US Privacy Shield on Feb 29. This is not yet law.
Citizen complaints – The new agreement gives companies and citizens the chance to complain and dispute any mishandling of records and personal information.
Targeted spying – This will now be limited to: detect and counter threats from espionage, terrorism, weapons of mass destruction, threats to the armed forces, or transnational criminal threats.
The proposed framework includes the following features:
- Companies must provide greater transparency with respect to their data collection, use, and sharing practices through more robust and detailed privacy policies
- If a company handles human resource (employee) data, it must agree to cooperate and comply with EU Data Protection Authorities (DPAs)
- Companies transferring personal data to third-party service providers remain fully responsible for the proper handling of personal data; must conduct appropriate due diligence concerning its service provider; and must properly monitor and re-mediate any deficiencies of its service providers relating to the handling of personal data
Our Advice
Ideally, companies should give consumers control over the information they divulge. This becomes even more urgent since corporations so freely share information with government authorities. Until consumers begin reading those 30-page privacy policies rather than blindly accepting them, they will continue falling for the same traps. Generally, as consumers we must understand that the “free” services we consume are actually very expensive. It often comes at the price of our privacy. So take a long hard look at the next privacy policy you’re asked to accept. You may be better served just paying cash instead.





