How the Internet Helps in a Crisis
Everyone has heard about the recent Paris Attacks on November 13th. Many people have found that the Internet helps in a crisis. The Internet can help to coordinate relief efforts while providing essential communication services to the unfortunate individuals involved in a disaster.
Google Crisis
![]() Google has created some powerful tools to help save the day in times of crisis.
Google has created some powerful tools to help save the day in times of crisis.
Crisis Response – Because Google’s crisis response team analyzes each crisis, each response may be slightly different.
A specific response may include:
- Creating a Resource Page – This is a simple web page containing the most relevant emergency information and tools available for a given crisis.
- Launching Google Person Finder – This is an application which connects friends and loved ones following a disaster. This is useful when there is a large number of missing people and traditional communication lines are unavailable.
- How it works: Google’s Person Finder page lists current disasters. Click on a disaster and you can then choose from either “I’m looking for someone” or “I have information about someone”.
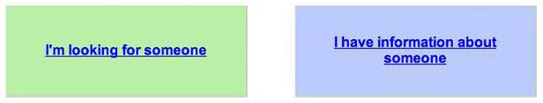
- How it works: Google’s Person Finder page lists current disasters. Click on a disaster and you can then choose from either “I’m looking for someone” or “I have information about someone”.
 Hosting a Crisis Map – This is a map that displays information concerning the disaster such as storm paths, flood zones, evacuation routes, shelter locations, and power outages. This includes official content and user-generated content.
Hosting a Crisis Map – This is a map that displays information concerning the disaster such as storm paths, flood zones, evacuation routes, shelter locations, and power outages. This includes official content and user-generated content.
Tools For Responders – Do you think your organization may be able to help in a disaster? Google also provides some tools for responders.
- Google Public Alerts – An organization can send emergency alerts if they are relevant to an ongoing crisis. These alerts will appear on Google’s search results, maps, and android devices (using Google Now).
- Person Finder – This can be embedded into your company’s website.
- Crisis Map – This can be embedded in your company’s website.
- Other Google Tools – Docs, spreadsheets, and Earth are all useful tools for responders.
Facebook Safety Check Tool
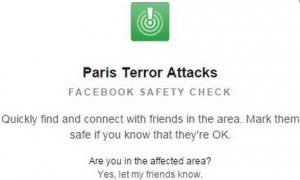 The Facebook Safety Check Tool was originally created for natural disasters. After the Paris Attacks, it has opened up to man made disasters as well. Basically, the Safety Check tool notifies friends and loved ones that you’re safe during a disaster.
The Facebook Safety Check Tool was originally created for natural disasters. After the Paris Attacks, it has opened up to man made disasters as well. Basically, the Safety Check tool notifies friends and loved ones that you’re safe during a disaster.
This was original inspired by the 2011 Tohoku earthquake and tsunami and was then released on October 15th, 2014.
How It Works:
- Affected Area Notification – Facebook sends you a notification if you are in an affected area and asks if you are safe.
- “I’m Safe” –
 After receiving the notification, if you click or tap “I’m Safe” it adds a green “I’m Safe” box next to your name so others can see your status. Other friends may also confirm whether or not you are safe.
After receiving the notification, if you click or tap “I’m Safe” it adds a green “I’m Safe” box next to your name so others can see your status. Other friends may also confirm whether or not you are safe. - Safe Friends Notification – After the tool has been activated you will then receive notifications when your friends have marked themselves as safe.
 Ways Facebook responded to Paris Attacks:
Ways Facebook responded to Paris Attacks:
- Enabled their safety check
- Created a profile picture filter of blue, white, and red
Twitter Alerts
 What? This is an alert that contains vital real-time information during a fast moving emergency. Since this feature is intended for crisis, disaster, and emergency communications, these alerts consist of:
What? This is an alert that contains vital real-time information during a fast moving emergency. Since this feature is intended for crisis, disaster, and emergency communications, these alerts consist of:
- Warnings of imminent dangers
- Preventive instructions
- Evacuation directions
- Urgent safety alerts
- Information on access to essential resources
- Information on critical transit and utility outages
- Crowd and misinformation management.
- Who? Only these groups are authorized to send an alert:
- Law enforcement
- Public safety agencies
- Emergency management agencies
- City and municipal governments
- County and regional agencies
- Select state, federal, and nation agencies and NGOs
- When? Twitter Alerts are used when traditional ways of communication are not available. Such emergencies may include:
 Natural disasters
Natural disasters- Severe weather
- Biological incidents
- Chemical or hazardous materials emergencies
- Nuclear
- Radiological incidents
- Explosions
- Food and agricultural incidents
- Cyber incidents
- Terrorism incidents
- Crime
- Major transportation incidents
- Where? Twitter Alerts send as SMS notifications. Also, an orange bell displays next to alerts on your timeline.
Think your organization qualifies? Complete the Twitter Alert Enrollment Form
How do I get Twitter alerts? Twitter Alert Setup
Ways Twitter responded to Paris Attacks:
- Use of hastags
- #PorteOuverte – Translates to Open Doors. This means you need a safe place to stay or you have a safe place (with open doors).
- #PrayForParis – Used to show support for Paris
- #RechercheParis – Translates to Search Paris. Friends and loved ones used this to find each other.
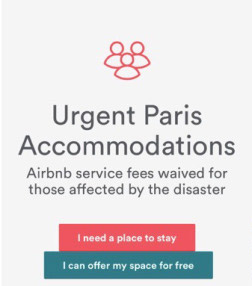
Airbnb Disaster Relief Program
 As a result of Hurricane Sandy in October 2012, many people in New York opened their doors to stranded individuals.
As a result of Hurricane Sandy in October 2012, many people in New York opened their doors to stranded individuals.
Airbnb, the unique online rental listing company, wanted to do the same during a disaster. They eventually created their very own disaster relief program. Airbnb even partnered with local government agencies and disaster relief organizations to make this program as effective as possible.
How it works Airbnb first sends out emails to room hosts in affected areas asking if they are in a position help. Hosts may then choose whether or not to participate. Finally, participating hosts open their doors (for free) to help people affected by the disaster.
- Airbnb still offers 12/7 customer support, trust & safety tools, host guarantee and all other services.
- Airbnb also uses their network to provide disaster information to the guests and hosts.
Ways Airbnb responded to Paris Attacks:
- Activated their disaster relief program and many hosts in the affected areas opened their doors to help keep people safe.
Other companies that helped during the crisis
Uber – Turned off their city price surge.
Verzion, T-Mobile, Sprint, AT&T, Google, and Skype – Made calling and texts from United States to France available for free
Google Event. The Good and The Bad.
Google held their press event on Tuesday, September 19th in San Francisco announcing many new products such as the Nexus 6P and 5X, the new Chromecast 2, Chromecast Audio, and the Pixel C. They also announced their new Operating System.
 Nexus 6P
Nexus 6P
This was the most anticipated product coming out of Google and is considered the “flagship”. While there are a lot of great features in this new phone some have found minor complaints about the Nexus 6P
5.7 Inches
1440 Resolution
Metal Exterior
Gorilla Glass 4
7.3mm Thick
Snapdragon 810 Processor
Complaint: Users disappointed in this version of Snapdragon
Android 6.0 Marshmallow Operating System
3GB RAM
Complaint: Future is looking at 4GB and some worry this will not be enough RAM
Project Fi (WIFI) Availability
Updated Camera – 8 Megapixel front-facing and 12.3 Megapixel Back facing (4K video and slow-motion shots)
Complaint: There is a camera bump (similar to the iPhone bump) and an “ugly” black bar
Complaint: Does not have optical image stabilization (OIS)
2 Front Facing Speakers
Nexus Imprint – Fingerprint sensor. Used to easily unlock phone and can be used to authorize payments on android pay or the play store.
Larger Battery
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Complaint: Future is leaning towards the wireless charging. Users disappointed that was not incorporated.
Colors – Frost White, Aluminum, and graphite
Cost – $499
 Nexus 5X
Nexus 5X
The Nexus 5X is considered the affordable alternative to the Nexus 6P over $100 cheaper. Even that being said it still has a lot of great features but the biggest worry it is not worth the update from their current phone. (ibtimes)
5.2 Inches
1080 Resolution
Gorilla Glass 3
Equipped with Android Marshmallow
Project Fi (Wireless Network) availability
Bigger battery
Nexus Imprint – Fingerprint sensor. Used to easily unlock phone and can be used to authorize payments on android pay or the play store.
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Complaint: Future is leaning towards the wireless charging. Users disappointed that was not incorporated.
Snapdragon 808 processor – Many like this processor better than Nexus 6P’s Snapdragon 810
12-megapixel camera (4k video)
Cost – $379
Chromecast 2
Chromecast has gotten some updates but luckily the price did not change. A new look along with better Wifi are only a few update. Some features are still yet to come in the next year.
Wifi Updates – Supports 5GHz Wi-Fi and has 2 antennas for better streaming
New Look – A small disc with bendable HDMI arm
Colors – red, yellow, and black
Cost – $35 (no change)
 Chromecast App Update – Universal voice search tool – “fast Play” videos google thinks you want to watch – “what’s On” popular content (youtube and Netflix) – adding new apps, showtime, sling TV, NBA, and NHL and Spotify
Chromecast App Update – Universal voice search tool – “fast Play” videos google thinks you want to watch – “what’s On” popular content (youtube and Netflix) – adding new apps, showtime, sling TV, NBA, and NHL and Spotify
Only Complaint: Does not support 4k TVs
Chromecast Audio
Google announced a brand new product called Chromecast Audio. A neat way to put life back into your old speakers. You can connect and send music. Many were happy to here Chromecast now supports Spotify. With it’s cute look it seems to be a hit.
Plugs Into Speaker – 3.5mm audio port
OS Support – iOS/Android/Chrome
Supports RCA or optical outputs
Connect and Send Music – Using google play, Pandora, NPR one, Rdio, and Spotify (controlled by phone lock screen and android smartwatch or android and chrome tab)
Cool Look -Looks like a mini vinyl record
Cost – $35
Complaint: Users are concerned with compatibility with speakers.
 Pixel C
Pixel C
Top feature of the tablet Pixel C is that fact it is light but solid. The keyboard connects well and feels stable. While there is not a release date Google promises it will be out by the holidays.
10.2 Inch Tablet
Detachable Keyboard
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Nvidia X1 Processor
Complaint: Users likes Intel Processor and not sure why they switched.
3GB of RAM
Android Marshmallow
Complaint: Users want the Chrome OS. Using a mobile OS limits some of the things that can be done on the tablet.
Cost – $499
Keyboard cost – $149
Complaint: Enter and delete key take time to getting used to placement.
Complaint: No touch pad. Sometimes the touchscreen is not optimal e.i. word documents.
 Android 6.0 Marshmallow
Android 6.0 Marshmallow
Android’s new ‘M’ operating system is the 6.0 Marshmallow. It comes with some desirable improvements.
Notifications – More consistent
Improves Battery Life
Fine-Grained Privacy Controls
Now on Tap – Google searches and voice interaction in individual apps
Doze – Power-saving mode – shuts down processes when hasn’t been moving or used
Not released to enough phones to have any known complaints
Devices to get Android Marshmallow:
End of 2015 – HTC One M9, One M8
Early 2016 – HTC M9+, HTC E9, HTCME, HTC E8, HTC M8 EYE, HTC Butterfly 3, HTC Desire 826, HTC Desire 820, HTC Desire 815
Samsung has yet to say except their new devices will not be launching with it. – techRepublic
Protect Your Smartphone From Malware
With the recent scares about Android’s ‘StageFright 2.0’ bug, that you get by opening a MP3 or MP4 file, it might get your wondering more about whether you have or had a bug on your phone. Different malware includes adware, bug, spyware, Trojan horse, virus, and many more (Learn more about Malware types ) There are some signs that your phone is being attacked and many ways to prevent your smartphone from getting malware. Already have a virus? There are ways to get your phone back in your control.
Has your phone been bugged? Here are some signs your phone is being tapped into:
- Difficulty Shutting Down – You may experience a delay in shutting down your phone. Often you will notice the back-light is still on even after it’s shut off.
- Odd Activity – This can consist of distortions on your screen or even application being installed by itself.
 Call Interference – During phone calls there may be unexplained background noises, clicks, echoes, or static.
Call Interference – During phone calls there may be unexplained background noises, clicks, echoes, or static.- Data Use Increase – Drastic increases in data without a good explanation. Not sure how to tell… “Look at how much data your device is using, and see if there’s a big discrepancy between how much data you’re using, and how much your applications are using. Any difference involving 10MB or more might be a sign of ‘parasitic activity’” – DarkReading
- Low Battery and High Temperatures – Both paired together could be caused by a constantly running application tapping into your phone.
- Coded Text Messages – This is a strong sign your phone has been tapped
The 2015 Internet Security Threat Report from Symantec showed that data breaches surged by 23 percent last year, and nearly a million new pieces of malware (“malicious software”) were created per day. Almost 1 in 5 Android apps available last year were actually malware in disguise, says the same report. The more popular smartphones and downloading apps become, the more popular malware and other viruses are becoming as well. Be smart and keep your smartphone safe from these bugs.
How do you prevent your phone from getting infected?
Strong Lockscreens – The stronger your passcode to get your phone unlocked the more secure your phone is.
- Not sure how to set up a lockscreen…

- Android Lockscreen Setup
- iPhone Lockscreen Setup
- Top lockscreen apps…
Get A Security Program – Ultimately the best ones would include anti-virus, anti-malware, anti-spam, anti-phishing defense, and a firewall.
- Android Antivirus Apps
- iOS Antivirus Apps
Update Your OS – There is a reason they come out with updates and new operating systems. The longer you put off updating your phone, the more susceptible it is.
Use Trustworthy Companies – If you are downloading applications, ringtones, wallpapers, etc. always use trustworthy companies, take the time to read reviews too.
Avoid Suspicious Websites – If you feel suspicious there’s good reason.
- How do you tell a website is unsafe? (SpyRambly)
- Poor layout
- Bright and flashing buttons, banners, or images
- Constant pressure to download
- Manipulation used to click on unsafe links
Turn Off Bluetooth – When you are not using the Bluetooth, have it set to off
Take Out Battery – Although this make not as practical for frequent users but if you know you won’t be using your phone for a while, take out the battery.
Don’t Jailbreak – If you jailbreak your phone this leaves you much more susceptible to viruses.
Use the Two Step Verification – This is an extra security step.
- Not sure how to set it up…
- Google 2-Step Verification
- Apple 2-Step Verification
Encrypt Sensitive Information – Another extra security step to help keep you safe.
- How do you encrypt?
 TIP: Backup Your Information – No matter how hard you try to prevent it there is still a chance you will get infected. It is always a good idea to have your information backed up in case you have to wipe your phone clean.
TIP: Backup Your Information – No matter how hard you try to prevent it there is still a chance you will get infected. It is always a good idea to have your information backed up in case you have to wipe your phone clean.
- How do you backup your phone?
- Android Backups
- iPhone Backups
My phone is infected! What do I do now?
- Take out your SIM card at first sign of malware
- Restart your phone in ‘Safe Mode’
 Depending on the severity of the infection:
Depending on the severity of the infection:
- Uninstall the application or remove file/software from where the malware came from
- Reset to factory settings – you can do this on your own or take it to your provider (This is where backing your information up is important)
- Run an anti-virus scan
That Window in the System Tray
Windows 10 Is Coming
What is that little square windows icon in the corner? Where did it come from and why isn’t it going away?
 Microsoft is going to release Windows 10 in the near future. Since they want everyone to upgrade, they are using that square in the system tray – that icon – a notice to get people to ‘reserve a copy’ in advance. If you click on the icon it will walk you through the ‘reservation’ and Microsoft will let you know when Windows 10 is available. They released the icon with the last Windows upgrade.
Microsoft is going to release Windows 10 in the near future. Since they want everyone to upgrade, they are using that square in the system tray – that icon – a notice to get people to ‘reserve a copy’ in advance. If you click on the icon it will walk you through the ‘reservation’ and Microsoft will let you know when Windows 10 is available. They released the icon with the last Windows upgrade.
When does it come out?
Windows 10 is supposed to come out on July 29.
How much does it cost?
Windows 10 is going to be free to Windows 7 and 8 users choosing to upgrade within the first year. From there Microsoft has not been very clear on what happens. There will also be a few different versions for Phone, tablets, and higher end users.
Why is there no Windows 9?
The joke is that 7 ate 9? Every second version of Windows is not so good so they just skipped one? Seriously though, there is a lot of ambiguity there and nobody has had a very good answer.
How is Windows 10 different?
I have not used it myself, but from what I understand it is said to have a lot of the good points of 7 and 8. People were not big on the tiles for Windows and were angry the start menu went away. The start menu comes back for Windows 10 (though they still keep some of the tile use.) If anything it should be an easier jump than from 7 to 8.
 Will my old computer handle it?
Will my old computer handle it?
It is said that it is supposed to be lighter-weight and easier on resources than 8 or 7, so it should play nice with even that old laptop sitting on the shelf.
Is it going to be good or bad?
A lot of people who have used the demo version are pleasantly surprised and say it is an improvement over 8. I am definitely going to upgrade my Windows 8 machine to try it out.
Anything else?
Internet explorer is going away. They haven’t said what the new browser is yet, but the code name is ‘Spartan.’
How To Store Your Computer Files
File Storage Options Are Everywhere
 We aren’t chained to one computer for all our digital needs anymore: we might use a computer, a laptop, a mobile device, and a tablet that we use interchangeably.
We aren’t chained to one computer for all our digital needs anymore: we might use a computer, a laptop, a mobile device, and a tablet that we use interchangeably.
On top of that, you have the work computer and files shared with friends or family. Sometimes you might want access to a document or images from another device. This adds up to a lot of files in many places!
What if you want to move those files around? You have many options at your disposal.
Backing Up & Terms You Should Know
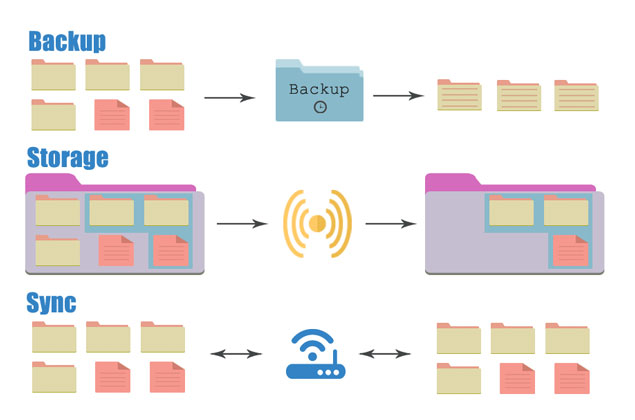
Before we go into your options, it’s important to know the difference between a backup and storage. If you have important files that you absolutely can not afford to lose, it’s important to have a comprehensive backup plan. We advocate the 3-2-1 Backup Plan: 3 copies, on 2 kinds of media, 1 of them off-site.
Backup: Backups, particularly with a backup program, are often much more comprehensive if more difficult to get to. They usually save multiple copies of a compressed file of your data.
Storage: Entails storing a given amount of data online or in a second drive. It may not be a lot of data, and it may be easy to get to again if you want to share it or access it from another device.
Sync: Synching means identical copies of your folder or device are in the second location: if you delete a file in the local folder, the file will also be deleted in the cloud or elsewhere.
Your Options for Storage
![]() External Hard Drive
External Hard Drive
It’s true that some external hard drives are large clunky bricks. Some, however, are the size of a deck of cards and easy to carry around in a bag or purse.
Pros: Lots of space. Fairly secure unless you forget it somewhere. Can be small and easy to carry.
Cons: Sometimes large and bulky. You have to remember to bring it with you. Don’t always play nice with smaller tablets and phones.
 USB Drive
USB Drive
Also known as thumb drives or flash drives, those small sticks (or cards, or tiny little plugs on a key chain) that plug into your computer or laptop, these have been used by college students for years.
Pros: Space is always increasing – a 35GB drive is easy to find and not too expensive. Small and easy to carry.
Cons: Small and easy to forget in that last computer you were using. Easy to lose or break or run through the laundry. Easy to accumulate and hard to organize. Don’t always plug into tablets or phones without a micro-USB adapter.
 NAS
NAS
Network Attached Storage is hard drive space that you reach through your own network. Some of them are small and contain one hard drive, while others are larger and more expensive, and carry the redundancy of multiple drives.
Pros: On-site. You are maintaining your own NAS and it’s right there at hand.
Cons: They tend to be expensive depending on size, with prices increasing depending on the space you need. In a perfect world you are going to want an offsite backup to go along with this.
 Optical Media: CDs, DVDs
Optical Media: CDs, DVDs
The old standbys of backup: CDs and DVDs – no doubt many of us still have a spool sitting around, ready to use.
Pros: Hard to save over. Even with rewritable discs, it takes applied effort to delete the disc’s media and then save again. CDs and DVDs are also inexpensive. Easy to move offsite and store elsewhere.
Cons: Better for one-use backups, discs also tend to degrade in time so they may not be a long term solution.
iCloud
Have an Apple device? Then you have iCloud storage ready to use, and your device is designed to play nice with Apple’s own cloud.
Pros: If you have an Apple product, you’re already set up with your own iCloud space, designed to integrate seamlessly.
Cons: Like any cloud storage, you need some kind of wireless internet access to use the cloud. And Apple’s iCloud hack some months back may leave a bad taste as the security of the system was compromised.
 Dropbox
Dropbox
Dropbox is one of the earlier forms of cloud storage/ synching and many people use it to share files with others for work or otherwise.
Pros: Many people already use it. Easy to use: you have a folder on your computer that syncs with the cloud and other machines. Good if you have multiple machines.
Cons: Too easy to use: sometimes it is easy to delete things, or sync excessively large files to all devices, taking up space.
 Google Drive
Google Drive
Google Drive started as a collection of online office tools called Google Docs. The word processing and spreadsheet tools have involved and they now include Google Drive itself, which starts at 15GB of space that you share with your Google account.
Pros: Comes with word processing tools and plays well with the other various Google products.
Cons: Not as internally organized as it could be, especially if you started using it as Google Docs.
 OneDrive
OneDrive
OneDrive is Microsoft’s answer to cloud storage. It comes already integrated with Windows 8, so long as you sign up for an account, which makes it easy to use if you are a Windows 8 person.
Pros: Easy to use with Windows 8 since it’s integrated right in. Tends to give various ways to hand out more free space.
Cons: While apps exist to let it work with other devices, it’s made for Windows 8 – if you have a scattering of other kinds of devices it may lose its appeal.
The best file storage solution is customized to your uses. If you feel more comfortable with a physical drive and no cloud use, a USB or small external hard drive may be the best way to go. However, if you have fully embraced the cloud and are less worried about security, utilizing the cloud that plays nice with your devices is likely the most appealing solution. Just remember to back up, and you’ll be all set to go.
How to Avoid Mobilegeddon on Your Website
Google is now ranking mobile-friendly websites higher than those that are not mobile ready.

[space50][space20]
Is Your Site Ready for Google?
Listen in to Appletree MediaWorks on TheUnionEdge.com on 4/28 at 1:30pm for help.
Is Your Website Mobile-Friendly?
If not, Google may now penalize your ranking for it.
The other day while browsing the web on my phone during lunch, I clicked on a link to an article that sounded interesting, only to find that the site was impossible to read. The text was tiny – I could zoom way in, but then I had to scroll to the side repeatedly to read anything. It was a frustrating experience, and I hit the ‘back’ button before getting far.
 Don’t let users have that same experience on your website.
Don’t let users have that same experience on your website.
How can you tell if your site is mobile-friendly?
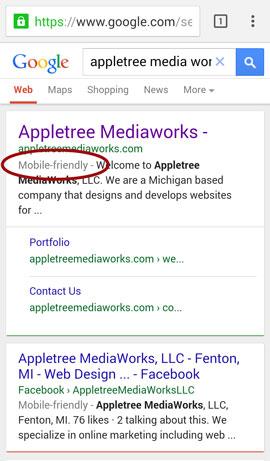
1) If you search for your site in a mobile web-browser, do you see the words, “Mobile-Friendly” next to your search entry in Google search? If not, Google isn’t seeing your site as mobile-friendly.
2) If you view your page, is text very small? Do you have to pinch-and-drag to read the site?
3) Do things seem too wide to view properly?
4) Is your site very difficult to navigate without zooming way in? Are links small and too close together to touch accurately with your finger?
 If you still aren’t sure, Google has a Mobile-Friendly Test to check your site out on.
If you still aren’t sure, Google has a Mobile-Friendly Test to check your site out on.
What if your site isn’t mobile-friendly?
The Mobile-Friendly Test will give links and tips on why your site isn’t mobile-friendly, and what to do about it. The most complicated issues can generally be resolved by converting a website to a responsive WordPress theme.
Mobile-Friendliness is not the only the thing to determine Google rank, but small businesses and organizations are most likely to lose out since the change. And with many people using their phones to look up information and local websites, making sure your website is accessible to everyone can only help.
We here at Appletree MediaWorks use responsive, mobile-ready themes when building our most recent websites for clients. If you’d like some help, give us a call and we can work you through your options.
Verizon Tracking Cookies Turned Zombie
 Remember those permanent Verizon tracking cookies? They’re causing a stir now that they’re being abused. According to Ars Technica, an advertiser named Turn exploited the Verizon tracking cookies to ‘turn back on’ tracking cookies on its own.
Remember those permanent Verizon tracking cookies? They’re causing a stir now that they’re being abused. According to Ars Technica, an advertiser named Turn exploited the Verizon tracking cookies to ‘turn back on’ tracking cookies on its own.
ProPublica released an article about the Zombie Cookies, which used Verizon’s tracking number to re-spawn tracking cookies that users had deleted. Verizon worked damage control by updating its site terms regarding the tracking cookies.
Later, Verizon stated it would expand its opt-out.
For more information visit:
Staff, Ars. “Verizon Will Now Let Users Kill Previously Indestructible Tracking Code.” Web. 3 Feb. 2015. <http://arstechnica.com/information-technology/2015/02/verizon-will-now-let-users-kill-previously-indestructible-tracking-code/>.
How to Clean Up Your Computer
 Have you ever noticed your computer starting to run slower for no apparent reason? Does Windows seem to take a while to boot up when it has no business crawling along like that? Has your browser become bogged down with a half-dozen tool bars of dubious origin?
Have you ever noticed your computer starting to run slower for no apparent reason? Does Windows seem to take a while to boot up when it has no business crawling along like that? Has your browser become bogged down with a half-dozen tool bars of dubious origin?
Keeping your computer cleaned up is not always something that comes to mind, but a little regular maintenance will keep it running smoothly.
Virus Protection
All PCs should have some form of virus protection and most, in fact, do. Newly purchased computers might come with McAfee or Norton Antivirus, but these programs often have special features that are free for a limited time, but then proceed to nag you once they expire. Fortunately, there are several free and reliable antivirus programs available, including Avast and AVG. Microsoft also distributes Microsoft Essentials for free, which runs quietly and discreetly in the background.
Whatever you decide to do, make sure to uninstall any antivirus program you may already have before installing another – doubling up on antivirus software can create more problems than it prevents. If your computer is sluggish, check to make sure that you have only one antivirus program installed.
Your job is to make sure your antivirus is running, up to date, and scheduled to scan regularly.
Popup Blockers
Most browsers come with popup blockers, but malware often finds its way in through ads, so installing an add-on such as Adblock Plus can reduce the likelihood of malicious advertising infecting your computer. However, do not go overboard with the addons. Occasionally, legitimate plugins will be purchased and compromised by shifty companies that use them to inject malware into your computer. Consider each plugin wisely, and uninstall them when you don’t need them anymore.
Anti-Malware Software
I know what you’re thinking – what is this and what about the antivirus software? The problem with malicious programs is that there are many kinds, and they evolve and change, so that old protection software may not catch everything. Further, there are many kinds – from tracking spyware to software that hijacks your browser. While doubling up on antivirus software may do more harm than good, having secondary anti-malware software does help – this is where MalwareBytes comes in.
MalwareBytes should be updated and run on a regular basis. It digs out things that your antivirus might not have caught, and then may ask to reset your computer to further dislodge any bad software it finds. Let it do its job – it’s one of the better pieces of software out there.
Taking Out the Trash
Another handy piece of software for keeping your computer running smoothly, CCleaner will get rid of old temporary files, history files, clean up the remains of uninstalled software, and much more. It also has an option to uninstall software you don’t need any more and makes it easy to deactivate programs that run in the background, eating up valuable system resources.
Deactivating software that runs in the background when your computer first starts up will speed up the process drastically. Be careful with this tool because you might need unexpected things (your antivirus software, some drivers and video software) – but do you really need parts of Adobe Acrobat checking for updates every time you turn on the computer? Probably not.
Driver Updates
Speaking of updates – drivers rarely bother you, but they can benefit from occasional updates as well. Updating your hardware drivers can boost computer performance and keep things running smoothly, especially in an older computer. Slimdrivers is a free program that will scan your computer and detect when drivers need updating. It will even download the correct drivers and initiate the update process without having to leave the program.
Software Updates
A lot of your software will update automatically, but it is still a good idea to keep track of what’s been updated, and manually update what is behind. Windows, Firefox, Chrome, and IE can be checked for updates. Flash, Acrobat, and Java will prompt you for updates, quite frequently. Go ahead and update them as they come in. Updates often patch security holes.
Defrag, Defrag, Defrag
When you’re all done, defrag that thing. Defrag is part of Windows (though you can get better or more visually appealing versions of the software). It crunches together fragmented files, giving your computer a little added boost. If you’re using a Mac, fire up Disk Utility and Verify and Repair your disk permissions.
Dust That Thing
If you’re feeling bold and don’t mind cracking your desktop computer open, get some canned air and dust out the machine. You’ll be amazed (and maybe a little scared) at just how much dust gathers on electronics – dust gums up the works and holds in heat that your computer does not need.
Be smart about it though – if your computer is under warranty you may not want to go meddling around inside. Warranties aside, always make sure the computer is unplugged before prying open the case. It also helps to ground yourself on something so you don’t inadvertently shock some delicate computer chip with a static charge from your finger. Also, remember that you’re messing with delicate electronic equipment. You don’t want to bring an industrial shop vac to the machine (yes, sadly, this has been done). It is possible to knock things loose if you bump or nudge cards or cords, so make sure they are seated properly before closing everything back up.
While you’re at it, take a look at that keyboard. It may need a little more than canned air.
Wrapping It All Up
Once everything is taken care of, it never hurts to create a backup or restore point, in case something malicious does find its way onto your computer. Along with good practices for keeping nuisance programs off your computer (I’m looking at you, toolbars and ‘free games’), regularly cleaning your computer can keep it running smoothly for years.
Net Neutrality in a Nutshell
[iconsweet icon=”megaphone” color=”black” size=”32″] Listen to Appletree MediaWorks talk about Net Neutrality on The Union Edge Radio Show.
What Is Net Neutrality?
Net Neutrality is the idea that internet providers should treat all internet traffic the same way, wherever it comes from-whether it be a corporation like Google or Netflix, a small business website, or a start up. ISPs should not be able to charge more for access to certain services or create tiered systems that allow access to certain data and block or throttle others. Internet providers claim they are not against Net Neutrality, but their actions have shown otherwise.
Why Is This a Problem?
The current proposed two-tier system would allow that companies which can afford it would have access to an internet ‘fast lane.” The concern is that this would hurt startups and innovation and companies that do not have the resources to spend on the fast lane would be left with the slow lane where their ideas may never get off the ground.
Internet provider companies are dabbling in this already. Early last year, Verizon successfully challenged a court case that allowed it to disregard FCC regulations regarding blocking or ‘discrimination’ of internet traffic.
Broadband providers are classified as “information services” and NOT “common carriers” so the FCC lacks legal authority to regulate them as they do radio and television. If an ISP were classified as a common carrier instead, this would allow the FCC to ban “paid prioritization” or otherwise set rules in place.
Is It a Real Concern?
Companies have already gone the paid prioritization route. As a recent and noteworthy example, streaming media like Netflix and Hulu use large amounts of bandwidth. Comcast had been throttling Netflix – speeds declined nearly 30 percent – until Netflix agreed to pay up. Some agreed that Netflix should pay up due to higher bandwidth use – others disagreed and called this out as extortion and an abuse by the ISP.
Who Is For It? Who Is Against It?
Generally speaking, if you are a streaming service or use streaming services, run websites, use things like Facebook and Google, or ARE companies like Facebook or Google, you tend to be Pro-Net Neutrality. If you distrust the cable companies, think the upcoming Comcast/Time-Warner deal is too monopolistic, and want the internet to keep functioning as it has been, you are pro-Net Neutrality.
If you are a large ISP such as Verizon, Time Warner, or Comcast you are against Net Neutrality. If you heavily promote free market ideals and believe the market should work itself out, or if you have more distrust of the federal government than large telecom and cable companies, you tend to question Net Neutrality.
The President Steps In
The Net Neutrality issue has been contentious, with the FCC soliciting opinions from all manner of users on the FCC website.
Then early this week President Obama stepped up officially in favor of Net Neutrality, asking the FCC to classify it as a public utility. Obama has asked for the internet to be treated with regulatory protections as if it were classified under the Title II of Telecommunications Act. He has presented a four-tier plan: No blocking, no throttling, increased transparency, no paid prioritization.
President Obama, even if he appointed FCC Chairman Wheeler to the position, has no control directly over the FCC. Wheeler has balked at the suggestions, expressing frustration at the President’s statements. The FCC Chairman likely sees himself as being between a rock and a hard place, being a former lobbyist for the cable industry and longtime supporter for Obama campaigns. The FCC is unlikely to make a decision until 2015.
What Does This Mean For Us?
The internet may change as we know it, but nobody is quite sure on the long term ramifications. It may be harder to access specific sites, they may be slower. Startups may not have the opportunity to get off the ground. Cable companies say nothing will be slowed or throttled (we have seen this to be false) – just sped up in the case of the faster lane. We may have to pay for premium internet packages which permit us access to certain internet features, or menus of selected features. This is only speculation.
Specifically, concerns that Net Neutrality fail include: degraded service, higher costs, less innovation, uneven service (faster for some, slower for others – a local media outlet might have more trouble), greater technological divide by income and demographic.
What You Can Do
The best thing you can do is contact the FCC – you can go to their website and contact them online or call them. Write or call your members of congress. And learn more about the issue, become informed, and speak out. Savetheinternet.com has information on actions you can take.
[iconsweet icon=”megaphone” color=”black” size=”32″] Listen to Katie Dexter talk about Net Neutrality on The Union Edge Radio Show.
More Info
http://www.cnbc.com/id/102173519
http://gawker.com/what-is-net-neturality-and-why-should-i-care-the-non-g-1657354551
http://www.webpronews.com/obama-asks-fcc-to-reclassify-the-internet-2014-11
The Good and the Bad of Cloud Computing
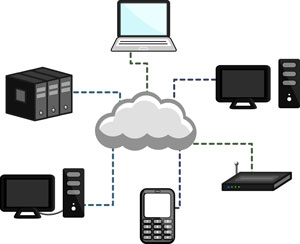
Cloud Computing
Cloud computing seems inescapable. Phones and devices have cloud servers for files, any user can get free cloud backups for their own computers, and even federal and state governments are investing in cloud computing for their own data. But just what is it, and is it safe?
What Is It?
First, we had computers that had hard drives with information and programs on them, and then we used discs to move that information from computer to the next. These discs were small, so we took to thumb drives, but this was problematic if you forgot your thumb drive at home or work or school. Those of us who had web mail account like Yahoo or Hotmail recognized we could just email ourselves the data, and open it from wherever.
This was the early stage of Cloud Computing.
Cloud computing is the practice of using a network of remote servers hosted on the internet to store and manage data, rather than a local server, or a personal computer. Given that few of us stick to just one computer these days –between home, work, school, laptops, tablets, and other devices – having ready access to that information on any device is important. This is where cloud computing comes in.
Where is it stored?
Cloud computing is named as such because information or even programs are used or run from a number of application or storage servers kept and backed up off site, and accessed through multiple computers where the user logs into an interface for access. A simple example of this is web-based email which is accessible through a web browser and website, but available through any computer.
Individuals and companies often resort to third-party cloud storage, such as iCloud, Dropbox, Google Drive and others. Companies may wish to back up not only files, but whole computers, databases, or programs for use.
When are people going to use this tech?
This sort of technology has been used since the ‘90s when people backed up files on web hosts or used web-based email clients. With the ever increasing use of mobile computing, cloud hosting has become more prevalent and will continue to do so for the foreseeable future.
Why is this needed?
The more mobile people become with their computing, the more important it will be to have access to files, data, and programs remotely. While devices and computers have ever-increasingly large hard drives and can hold more info, hauling around secondary drives and copying information over is redundant and unnecessary.
For companies and industries, a base location for all information is valuable in the interests of saving money and time. Instead of a slowly depreciating server under a desk or stuck in the back room, all information is available and reliably backed up offsite. This also allows for people in multiple locations, branches, or buildings, to have access to and immediately update information as needed.
What are the potential pitfalls and drawbacks?
Cloud computing has some very real drawbacks and concerns, and some of them do not have good solutions at this time:
- Access: To access the cloud (whatever form of cloud you are accessing at the moment), the user needs internet access. Without wifi or otherwise, access to files and software severely limits what can be done. This is becoming less and less a problem as time goes on, but still could come up as an issue.
- Security: Every day the news broadcasts another company or institution getting hacked. And as security gets more sophisticated, hackers always seem one step ahead. Information could be accessed and stolen during a number of points in the cloud computing process, whether it be a hacker discovering a means of getting in, or a user with a weak password.
- Privacy: Housing your data somewhere on the web inevitably means someone else may have access to it. Along with the aforementioned hackers, NSA access to various servers and databases has been argued and discussed extensively throughout the last year. While a company may not have anything to hide, they may not want that data accessible in general.
- Third Party Control: Ultimately, in handing over data and programs to a third party, a company or institution is handing the keys over to someone else. Not everyone likes this or feels comfortable with it, and would prefer to have complete control over their information.
Despite the potential hazards of cloud computing, large companies and even government and official institutions more and more are turning in that direction due to reduced costs and ease of use. The debate and concern over the security of private information will only increase as hackers are more sophisticated and computing becomes more ubiquitous. But cloud computing is not going away any time soon.
For more information on cloud computing and internet security in general, follow the Appletree Media blog.
More On Cloud Computing:
http://computer.howstuffworks.com/cloud-computing/cloud-computing.htm
http://www.moneycrashers.com/cloud-computing-basics/
http://www.thefiscaltimes.com/2014/10/14/States-Turn-Cloud-Computing-Cost-Savings
http://www.whitehouse.gov/sites/default/files/omb/assets/egov_docs/25-point-implementation-plan-to-reform-federal-it.pdf
http://www.itproportal.com/2014/10/13/whitepaper-five-myths-cloud-computing/