NSA Surveillance and Online Privacy
Who are the NSA?
The National Security Agency (NSA) is a powerful United States intelligence organization. Basically, they are responsible for collecting, processing, and monitoring global data for intelligence purposes. The NSA has a stated role to advance national security while protecting the freedoms, civil liberties, and privacy rights guaranteed by the Constitution and federal law.
What is the issue?
Many studies, cases, and documents show that the US government is spying on American citizens using online NSA surveillance. As Americans, this invades our Freedom of Speech and our Right to Privacy. The ACLU has called this activity “unconstitutional surveillance of Americans’ communications”.
Some Examples
An internal NSA audit from 2012 revealed they committed 2,776 incidents of unauthorized surveillance of Americans or foreign targets in the US over a one-year period.

On May 20, 2013, Edward Snowden released files from the NSA which described, as he put it, “systematic surveillance of innocent citizens.” Based on Snowden’s documents, the NSA has at least nine major tech companies gathering data on selected surveillance targets. This revelation caused online privacy concerns to increase dramatically in the US.
Then on Dec 24, 2014, a Freedom of Information lawsuit filed by the ACLU revealed NSA documents from 2001 to 2013. Overall, these documents showed that there were instances of unauthorized surveillance of US organizations, spouses or love interests, and more American citizens.
What is a Digital Pat Down?
The inner workings of an intelligence machine like the NSA can be difficult to grasp. From leaked documents so far, we can surmise that the NSA is performing secret “digital pat downs” on American citizens somewhat regularly. This happens without our knowledge or consent.
First, an NSA analyst identifies a target and submits a request to the FBI’s Data Intercept Technology Unit. Next, dedicated employees at various tech companies receive the request and gather the requisite data. This may include emails, chat logs, and videos. Once the data is compiled, it is sent back to the FBI for analysis.
The National Security Agency is also piggybacking on the tools that enable Internet advertisers to track consumers, using “cookies” and location data to pinpoint targets for government hacking and to bolster surveillance. We’ve talked in detail about mobile phone tracking tools previously.
They are also collecting location data transmitted by mobile apps. An NSA program, code-named HAPPYFOOT, helps the NSA to map Internet addresses to physical locations more precisely than is possible with traditional Internet geolocation services.
 How do Americans feel?
How do Americans feel?
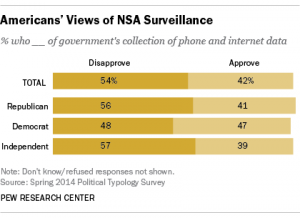
PEW research shows what Americans think about online privacy and the NSA.
Overall, 54% of Americans disapprove of the US Government collecting telephone and Internet data for anti-terrorism efforts.
74% said they should not give up their privacy and freedom for the sake of safety.
93% think it is important to control who can get their information.
38% think they have only some control over their own information.
Cyber Legislation
CISPA had alarmed the privacy community by giving companies the ability to share cyber security information with federal agencies, including the NSA, “notwithstanding any other provision of law.” That means CISPA’s information-sharing channel, created for responding quickly to hacks and breaches, could also provide a loophole in privacy laws that would enable warrant-less intelligence and surveillance. The information they gather, including all hacked data and any incidental information swept up in the process, would be added to a massive database. The FBI, CIA, and NSA would then be free to query this data at their leisure.
This is how CISPA would create a huge expansion of the “backdoor” search capabilities that the government uses to skirt the 4th Amendment and spy on Internet users without warrants and with virtually no oversight.
How to prevent being spied on by the NSA and other data collectors without going off the grid
It may be impossible to completely prevent the NSA from spying on you, but you can try and make it much harder.
- Avoid popular Online Consumer services – These include Google, Facebook, and DropBox.
- An alternative to DropBox is SpiderOak.
- A common alternatives to Google is DuckDuckGo.
- Mashable has published a list of private social networks to help you avoid the Facebook plague.
 Encrypt your hard drive – You may have password protection on your files but you should go a whole step further and encrypt the entire hard drive.
Encrypt your hard drive – You may have password protection on your files but you should go a whole step further and encrypt the entire hard drive.
- Avoid online tracking – On you browser you can use the do-not-track setting but you can go a step farther and use a plugin to stop tracking. Some reputable plugins for this include:
- Encrypt your email and chat messages – Encrypt your messages before you send them. Some common email clients with encryption include:
- Microsoft Outlook – This has encyption options if you want to use them.
- Runbox (a Norwegian secure email client) – Claims to be unreachable by the NSA.
- HushMail – Not as popular but is completely encypted.
If you chat on the Internet, you can encypt those messages too.
- ChatCrypt – Encrypts the message when it sends and can only be read by the end user, also known as end-to-end encryption.
If you use common instant messaging through Google, AOL, Yahoo or Microsoft you can use a chat extension called OTR (Off the record) which enables end-to-end encryption.
- Use TOR for online browsing – TOR stands for The Onion Router. Like an onion, it layers multiple levels of security. Basically, it bounces communication around a network of relays which makes it very difficult to track.
 Many browsers also have a private mode.
Many browsers also have a private mode.
- Firefox – Private Browsing
- Chrome – Incognito mode
- Internet Explorer – InPrivate feature
Online Privacy in Europe
A recent draft of the British Investigatory Powers Bill will require companies to store information for up to a year. Communications companies would hold details of which websites and apps a person uses.
 Recently, the European Union has decided to invalidate the current voluntary safe harbor because they believe the US cannot adequately protect its privacy. There have been reports that European companies are transferring data out of US territory for safe keeping.
Recently, the European Union has decided to invalidate the current voluntary safe harbor because they believe the US cannot adequately protect its privacy. There have been reports that European companies are transferring data out of US territory for safe keeping.
EU-US Privacy Shield
The US Government released full text of the new European Union-US Privacy Shield on Feb 29. This is not yet law.
Citizen complaints – The new agreement gives companies and citizens the chance to complain and dispute any mishandling of records and personal information.
Targeted spying – This will now be limited to: detect and counter threats from espionage, terrorism, weapons of mass destruction, threats to the armed forces, or transnational criminal threats.
The proposed framework includes the following features:
- Companies must provide greater transparency with respect to their data collection, use, and sharing practices through more robust and detailed privacy policies
- If a company handles human resource (employee) data, it must agree to cooperate and comply with EU Data Protection Authorities (DPAs)
- Companies transferring personal data to third-party service providers remain fully responsible for the proper handling of personal data; must conduct appropriate due diligence concerning its service provider; and must properly monitor and re-mediate any deficiencies of its service providers relating to the handling of personal data
Our Advice
Ideally, companies should give consumers control over the information they divulge. This becomes even more urgent since corporations so freely share information with government authorities. Until consumers begin reading those 30-page privacy policies rather than blindly accepting them, they will continue falling for the same traps. Generally, as consumers we must understand that the “free” services we consume are actually very expensive. It often comes at the price of our privacy. So take a long hard look at the next privacy policy you’re asked to accept. You may be better served just paying cash instead.
Social Media Copyright Issues: Fair Use or Infringement?
Social media copyright issues have become a hot topic in recent months. Nearly everyone has shared something on social media that was copyrighted by someone else. But what is fair to use on social media and what infringes on the rights of the copyright holder?
Is it fair use or infringement?
If you do not get a license from the copyright holder then the only way to use the content is through something called “fair use”.
What is fair use?
Generally, fair use covers any copyrighted material that was shared with a “transformative” purpose. This might constitute a comment, criticism, or parody accompanying material. Such sharing can take place without permission from the copyright owner.
Categories of Fair Use
- Commentary and Criticism – Commenting upon or critiquing copyrighted material. Examples include online reviews, news reports, education courses, or court case.
- Parody – A parody takes copyrighted material and ridicules it in a comedic way.
Fair Use Checklist
Not sure if you’re allowed to share something under “fair use”? Run it through this checklist to be sure before you post.
☐ Purpose and Nature of Use
The use of copyrighted material must be “transformative”. This means you took the time to add new meaning or value to the copyrighted material with new information, aesthetics, insights, or understandings.
Example of Fair Use: Google images – All Google images are copyrighted by the owner. Google’s use is considered “transformative” because it displays pictures in a different way, for a new purpose.
Example of Fair Use: Scary Movie Series – This movie series is a parody which borrows copyrighted material in order to ridicule it. Producers added value using new information, aesthetics, insights, and understandings.
Example of Infringement: Posting a copyrighted image on social media is for aesthetic or entertainment purposes. This is likely NOT a different use than the copyright holder intended and does not transform the work.
☐ Nature of the Work
Using copyrighted information has more leeway in fair use than copyrighted creative works. Also, there is more leeway in using published work rather than unpublished work.
☐ Amount and Substantiality of the Portion Used
Less is more. Meaning the less you use of the copyrighted material the more likely it will be considered fair use.
Exception: Using the most memorable (although small) part of a copyrighted work, such as the opening riff of “Sweet Child O’ Mine” by Guns N’ Roses.
Exception: Parodies – Quite a bit of a copyrighted material, even the heart of the material, can be used for parody. The Supreme Court acknowledges that “the heart is also what most readily conjures up the [original] for parody, and it is the heart at which parody takes aim,” as decided in Campbell v. Acuff-Rose Music,510 U.S. 569 (1994)
☐ Effect of Use Upon Market or Value
If you deprive the copyright holder income or undermine copyrighted work that could have potential market it is not fair use and you are most likely looking at a lawsuit. This holds true even if you are not using the copyrighted work directly.
Example of Infringement: An artist used a copyrighted photo to produce wood sculptures and earned a lot of money selling them. Even though the photographer did not plan on make sculptures it was considered a potential market and the court ruled in favor of the photographer.
[alertbox color=”blue”]MYTH
If you list a source, using copyrighted material is permissible.[/alertbox]
This is probably the most popular myth about copyrighted material. Even if you list your source, using copyrighted work without permission is still an infringement, especially if you are making income from it.
☐ Check Original Source
Sometimes the original source will have copyright notices. If you are unsure, be safe and obtain a license from the copyright holder.
 ☐ Check Social Media Terms and Conditions
☐ Check Social Media Terms and Conditions
When someone posts original work on social media, you should check the authorization to re-post, re-tweet, or re-pin that content. Read our blog article Social Media Content Rights for more detail.
Example: Pinterest’s term of service states that if a user posts content on Pinterest they are providing a license to all other users to use that content on Pinterest.
☐ Post a link instead of content
On social media, post a link to the original source of the material instead of the material itself. While this is still infringement, the chances of a complaint are much lower (especially since everyone does it). This does support a fair use defense.
☐ Keep Sharing Within Network
When you find content on social media you want to share, keep it within that network. Always read the terms and services before sharing.
[alertbox color=”blue”]
MYTH
Content posted on social media is fair game.
[/alertbox]
Some may think that if the content is on social media then it is fair game to use. This is not the case – the copyright still belongs to the copyright holder.
 You can be held at fault for posting copyrighted material or even sharing something someone else posted that was copyrighted. This seems to happen so frequently on social media that the chances of litigation are low, but it’s still a risk.
You can be held at fault for posting copyrighted material or even sharing something someone else posted that was copyrighted. This seems to happen so frequently on social media that the chances of litigation are low, but it’s still a risk.
U.S. Copyright Office Fair Use contains comprehensive information if you’d like additional information.
Is Your Smart Phone Spying on You?
Is your smart phone spying on you? In short, yes. Follow the simple guide below to find out how to protect yourself.
Apple
 Frequent Locations
Frequent Locations
iPhones track your location data down to the minute.
Who uses this information:
- Third party advertisement: If you visit a shoe store, you might receive shoe advertisements.
- Apps: Apps may request permission to access your frequent locations. This may be useful for some things such as viewing local weather or calculating ETAs from your location.
![]() How to stop it:
How to stop it:
- Settings > Privacy > Location Services > System Services > Frequent Locations
- There is a toggle for turning on and off frequent Locations and Improve Maps
 Identifier for Advertising (IDFA)
Identifier for Advertising (IDFA)
This allows developers and marketers to track your activity. They use this data for targeted advertising on apps and web pages.
![]() How to stop it:
How to stop it:
- General > About > Advertising
- There is a toggle to turn on Limit Ad Tracking
Microsoft
 Windows 10
Windows 10
The new updated Windows 10 tracks just about everything you do.
Here is a section of the Windows 10 terms:
Finally, we will access, disclose and preserve personal data, including your content (such as the content of your emails, other private communications or files in private folders), when we have a good faith belief that doing so is necessary to: 1.comply with applicable law or respond to valid legal process, including from law enforcement or other government agencies; 2.protect our customers, for example to prevent spam or attempts to defraud users of the services, or to help prevent the loss of life or serious injury of anyone; 3.operate and maintain the security of our services, including to prevent or stop an attack on our computer systems or networks; or 4.protect the rights or property of Microsoft, including enforcing the terms governing the use of the services – however, if we receive information indicating that someone is using our services to traffic in stolen intellectual or physical property of Microsoft, we will not inspect a customer’s private content ourselves, but we may refer the matter to law enforcement.
![]() How to stop it:
How to stop it:
Many methods are available, with varying effectiveness:
- InPrivate Mode – Setting you browser to InPrivate mode does not completely cover your tracks
- Unchecking all tracking pages upon opening – This has been tested (even with a DisableWinTracking tool) and found it still tracked some information.
Google/Android
 Voice Commands
Voice Commands
Every voice command you make on your android phone is logged. These recordings should only be available to you but the idea of possibly having any personal information stored may be unnerving to some. Every Google device records and stores voice commands.
![]() How to stop it:
How to stop it:
- Settings > Account > Google > Sign In > Personal Info & privacy > Activity Controls > Voice & Audio Activity
- There is a toggle to turn this off. You can also delete all saved recordings.
 Location Tracking
Location Tracking
Just Like Apple, Android tracks your location. Google doesn’t limit their tracking to cell phones. They continue tracking you from your desktop computer, if you leave your Google account logged in.
Who uses this information:
- Third party advertisement: If you visit a shoe store, you might receive shoe advertisements.
- Apps: Apps may request permission to access your frequent locations. This may be useful for some things such as viewing local weather or calculating ETAs from your location.
![]() How to stop it:
How to stop it:
- Settings > Account > Google > Sign In > Personal Info & privacy >Google Location History
- The you can toggle this off and you can delete location history
 Android Advertising ID
Android Advertising ID
Similar to Apple’s Identifier for Advertising, Google takes information from your search activity to use for targeted advertising. You see these within apps downloaded from Google Play.
![]() How to stop it:
How to stop it:
- Settings > Account > Google > Sign In > Personal Info & privacy > Ads Services
- This will take you to a web page to manage the ad settings. Then you can toggle it off.
- You can also reset the ID which clears past data. This can be helpful if you still want to see ads tailored to you but not about something you recently searched about. You can even delete and add interests to better tailor the ads.
This will not stop the ads but will stop the targeted ads based on your search history.
Do Not Track
In 2010, the Federal Trade Commission (FTC) had pledged to give Internet users the power to decide if or when websites were allowed to track their behavior called the ‘Do Not Track’ initiative.
This concept allowed a user to opt out of letting any of their online data to be tracked and found by anyone on the Internet. Similar to the ‘Do Not Call’ initiative of 2007, today we still do not see the ‘Do Not Track’ initiative doing what the FTC pledged it would.
Last Month, two members of congress filed a bill called the ‘Do Not Track Online Act of 2015’
This act would “require companies to allow consumers to stop collection of personal information”.
The ‘Do Not Track Act’ prevents privacy abuse and gives back control over personal lives online. People deserve to be empowered to stop trackers who collect and store their personal, private information.” – US Senator Richard Blumenthal
Every online click consumers make provides a detailed and private picture of their personal lives, and Americans should have control over the collection and use of this personal, sensitive information.” – US Senator Edward Markey
Where did the FTC go wrong?
Standard Never Finalized – 5 years later and the industry group have not finalized a standard for how ‘Do Not Track’ would work. Even those working with them to finalize this have given up their efforts.
Relied on Powerful Internet Companies – The FTC relied on powerful Internet companies such as Google, Facebook, and Yahoo. This presents a conflict of interest since these businesses want to track information for use in online advertising.
Unfair Set of Rules – Eventually, a team proposed a set of rules last August that let these powerful Internet companies track their consumers as long as they did not pass it along to any third parties. This caused those third party companies to feel they had an unfair competitive disadvantage.
Loss of Help – Companies such as The Digital Advertising Alliance, Consumer, Watchdog, The Electronic Frontier Foundation, and many more all gave up the efforts that the working group would come to a solution.
 Mobile Browser Tracking
Mobile Browser Tracking
Mobile phone carriers Verizon and AT&T are tracking your mobile online web activity. They do this by using “Supercookies” which collect information on your browsing habits. These cookies, unlike ordinary cookies, cannot be deleted by clearing your browsing history. This feature also ignores any ‘Do Not Track’ settings. Using a private browser does not help with this type of cookie.
Verizon Users
Since 2012, Verizon gives this tracked information to marketing companies that send out targeted advertisements based on your browsing habits. Verizon uses a process called X-UDIH to collect this data. The Electronic Frontier Foundation has become concerned about “what this technology allows others to find out about users’ web activity,” because of how insecure and dangerous for privacy it is.
AT&T Users
Similar to Verizon, the information AT&T collects is visible to third parties for targeted ads but they are testing a new way to track customers. They claim to be working on a privacy-protective measure on their tracking.
What Kind of Information is Collected
 Web browsers collect 2 different types of cookies. First-Party cookies and Third-Party cookies.
Web browsers collect 2 different types of cookies. First-Party cookies and Third-Party cookies.
First-Party cookies include:
- Shopping cart items ie. amazon.com
- Log-in name
- Language
- Location
- Preferences/settings
ie. saved places on weather.com - High games scores
Third-Party cookies include:
- Browsing History
- Searches through search Engines
ie. Google.com - Search result from other sites
ie. Amazon.com
Browser cookies can also store your name, home address, and telephone number, but only if you provide it.
Third parties can track social media information such as your name, friend list, and even more.
How to Block Tracking
Browser Tracking Blockers – Chrome and Firefox
- Adblock Plus
- Ghostery
- Do Not Track Plus
- ScriptNo (Chrome)
- NoScript (Firefox)
 Mobile Browser
Mobile Browser
Tracking Blockers and Tips
- Set browser setting to “Privacy Mode”
- Use apps instead of the web
- Dolphin Browser (Android)
Visit our online privacy article to learn more on ways to prevent data collection and online spying
Safe Harbor Rule Invalidated, How it Affects You
The Data Safe Harbor Rule
 The Safe Harbor Rule was established in 2000 between the European Union (EU) and the United States (US). This agreement allowed businesses to legally funnel information across the Atlantic. Such data is normally transferred during global commerce, email correspondence, and even social media communication. Europe has stricter privacy guidelines to protect its citizens than the US does. Under the Safe Harbor agreement, US companies could “self-certify” that they met Europe’s stricter privacy standards in order to gain access to European markets.
The Safe Harbor Rule was established in 2000 between the European Union (EU) and the United States (US). This agreement allowed businesses to legally funnel information across the Atlantic. Such data is normally transferred during global commerce, email correspondence, and even social media communication. Europe has stricter privacy guidelines to protect its citizens than the US does. Under the Safe Harbor agreement, US companies could “self-certify” that they met Europe’s stricter privacy standards in order to gain access to European markets.
In early October, the European Court of Justice ruled that the US approach to domestic surveillance was not up to European standards. Basically, this happened because the court was concerned that the US would compromise the data of European citizens swept up in our country’s growing mass surveillance machine. Consequently, this ruling made the Safe Harbor pact invalid virtually overnight.
The Safe Harbor Agreement 2.0
The European Union and the Unites States will be meeting on December 17th to create a new agreement for the Safe Harbor. They plan to conclude this agreement in January of 2016. The EU would like to see some changes in the new agreement such as:
- Privacy watchdogs to challenge US companies’ handling of EU data
- European citizens should be able to complain directly to national authorities about data protection
What Does an Invalid Ruling of Safe Harbor Mean?
This affects businesses and consumers from both the European Union and United States. Over 4,000 companies rely on the Safe Harbor for their data transfers, including:
Effects on Companies:
This affects any US-based company doing online business in the EU.
 Many companies that relied on the Safe Harbor “Self Certification” will now have to obtain independent certification.
Many companies that relied on the Safe Harbor “Self Certification” will now have to obtain independent certification.
In Europe, EU standards from 1995 are now being used to determine whether a company’s data sharing is permissible. As of now, the EU operates under the Data Protection Directive. This requires that companies only transfer data to countries that offer adequate privacy protection.
For More Information: With Safe Harbor now “Invalid,” Companies Must Change Data Practices
Effects on Consumers:
Consumers in the US might not notice a substantial difference. European consumers may be cut off from US companies for a time, depending on how stringent the new rules become. It may take some time before US based companies have made the necessary adjustments to do business with the EU again.
Microsoft’s Solution
 Microsoft has stated they will be storing data in a German company, Deutsche Telekom, for their European cloud computing customers. Microsoft will not be able to access the data without permission of either the customer or the company.
Microsoft has stated they will be storing data in a German company, Deutsche Telekom, for their European cloud computing customers. Microsoft will not be able to access the data without permission of either the customer or the company.
This solution may be too expensive for many companies. As a result, the US has started offering customers and partners the opportunity to enter into ‘data processing addendums’. However, these are only a temporary solution. Consequently, many companies are awaiting to hear what’s in the new Safe Harbor Rule.
Scam Emails
 Scam emails are a very popular and while most email services have a spam sorting feature built in, not all will be sorted properly. Scams can look like they came from a friend, a business you interact with or do not interact with, federal agencies, charities, or complete strangers.
Scam emails are a very popular and while most email services have a spam sorting feature built in, not all will be sorted properly. Scams can look like they came from a friend, a business you interact with or do not interact with, federal agencies, charities, or complete strangers.
There are ways to notice whether the emails are legitimate or not. There are extra precautions you can take for those that may not be as noticeable but still suspicious. However sometimes you do fall victim to these and there are some steps to take if that happens.
Common Types of Scams
There are so many types of email scams out there but some of the popular ones include bogus offers, phishing, Trojan Horse, and request for help.
Bogus Offers
These usually involve discounted or free items or too good to be true products or services. Your best bet if it sound too good to be true then you are probably right.
Bogus Business Opportunities
 Subject Lines: Make a Regular Income with Online Auctions, Put your computer to work for you!, Get Rich Click, or Use the Internet to make money.
Subject Lines: Make a Regular Income with Online Auctions, Put your computer to work for you!, Get Rich Click, or Use the Internet to make money.
Scam: Most of these contain links that either contain malware, bring you to bogus sites that ask you to enter personal information or pay for an “information kit”
Health and Diet Scams
Subject Lines: Need to lose weight for summer?, Reduce body fat and build lean muscle without exercise, CONTROL YOUR WEIGHT!!, or Takes years off your appearance.
Scam: Most contain links that contain malware. Some may contain fake customer testimonials to convince you.
Easy Money or Free Items
Always avoid anything with these similar titles. It is almost always a scam.
Scam: They usually lead to a website you have to enter your information in to steal it or ask for some sort of fee for “processing” or “shipping”.
Phishing
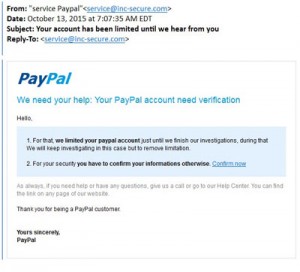 The definition is in the name, these are people “fishing” for your information. These types of scams exploit existing companies that you may or may not interact with. Using a popular companies name can make you believe the email is real.
The definition is in the name, these are people “fishing” for your information. These types of scams exploit existing companies that you may or may not interact with. Using a popular companies name can make you believe the email is real.
Account or Credit Information
Subject Lines: Your account is going to expire!, You’re Pre-Approved, or Guaranteed credit card
Scam: This will most likely contain a link that downloads malware, more specifically a keystroke logging malware so when it directs you to the convincing but fake website it steals your sensitive information.
Trojan Horse
These are emails that contain attachments. They usually promise something funny, a photograph, or a patch for software vulnerability.
Subject Line: Funny, Hi Friend, Check it out!
Scam: These attachments contain malware making your device vulnerable and possible installs software stealing your information.
Requests for Help
Disaster Relief
Fake charity websites are created to get people to donate money to a disaster such as 9-11 or Katrina.
Scam: Link inside email will direct you to offer your bank or credit card information to steal.
Nigerian – 419
These are very common scam emails that include sob stories, unfailingly polite language, and a promise of a big payoff.
Subject Lines: My Dearest Friend, Contact my secretary, and from the desk of.
Scam: Most offer huge payout if you help. Only problem is you need to pay a fee or “tax” to get the money. This allows scammer to take your money and identity.
Most Recent Reported Scams
 WhatsApp Scam Email
WhatsApp Scam Email
This email poses as a popular mobile phone app called “WhatsApp” claiming it has an incoming voice message for the user. Inside the email is a video message that if played will add malware to your device or bring you to a site that will add malware.
Credit Card Chip Scam Email
With new credit card chips on the rise, scammers have created an email that say you need to update your information to receive your new card. This is a method of phishing, and scammers even use the credit company’s logos. “… card companies won’t be giving you a heads-up, you’ll simply get your new card in the mail…”
How to recognize that an email is a scam?
- Sounds too good to be true
- Include words like easy, free, fast, and quick
- All capital letters
- Sounds urgent
- Uses misspelled words or slang
Sender
- Email account name does not match sender name.
 Example:
Example:
From: Meijer (ShopForMore@mymeijer.com) – The name of sender and email account match well enough to show some trust from the sender
Example:
From: Allied & NAVL (79JN@kipwring.com) – Most businesses have their business name after @ and before .com and start with either info, support, and noreply.
Body of Email
- Information is extremely vague – Especially when pertaining to subject lines about account expiration or upgrade, is a tactic to get you to click on link because of your confusion. This is also common in the ‘get rich quick scams’ and ‘lose weight fast’ using you curiosity to their advantage.
- Image is only thing in body – A real email will try to use a good mix of images and text.
- Plain text is only thing in body – Once again a real email will try to use a good mix of images and text.
How to avoid these scam emails?
 Install/Update Antivirus Software – This will help block any email-born viruses
Install/Update Antivirus Software – This will help block any email-born viruses
- Android Antivirus Apps
- iOS Antivirus Apps
- Desktop Antivirus
Install/Update Personal Firewall – This will also help block any email-born viruses
Setup Email Spam Filtering – A lot of emails offer spam filtering which does a fairly good job. This is not 100% effective though so do not rely on spam filtering.
 Setup Email Security – A lot of emails automatically have a security set up for spam but some you may need to configure yourself. Anytime you make an account on the internet you need to always check the security and privacy options to protect yourself.
Setup Email Security – A lot of emails automatically have a security set up for spam but some you may need to configure yourself. Anytime you make an account on the internet you need to always check the security and privacy options to protect yourself.
Do Not Trust Unsoliciated Email – These are individuals or organizations that are unknown. Most likely they are not a trustworthy sender.
Tip: Anything of real importance will contact you by phone or mail. Anything federal/Government related will only contact you by mail.
Be Cautious About Attachments – This is a very easy way to download malware onto your device. To be safe, only open attachments from trusted senders.
 Do Not Click Links – This is another easy way to download malware onto your device. Even though the link name may look familiar, mimicking a real business, it does not mean it is real.
Do Not Click Links – This is another easy way to download malware onto your device. Even though the link name may look familiar, mimicking a real business, it does not mean it is real.
Click link to see an example: https://www.youtube.com – Looks like a real link to YouTube but it didn’t take you to YouTube
Tip: Not sure if a link is safe? Type it into your browser instead of clicking on the link.
If you have been a victim of fraud email
- Run a antivirus scan
- Contact Credit Agency – You can place an alert with any one of the three major credit bureaus signals to potential creditors that you could be a victim of identity theft.
- Update Account Logons – Change passwords on as many accounts as possible
- Report it to Action Fraud
- Fill a complaint at the Federal Bureau of Investigation Internet Crime Complaint Center and review recent press releases
- File a report with the Federal Trade Commission
[stylebox color=”gray” bgcolor=”#7ad0ff” textcolor=”#000000″]
TIPS:
- IRS and court appearances will never contact you by email. They will most likely use paper mail.
- Type links into your browser instead of clicking on the link. This will prevent a redirected link.
- Do not open attachments unless from a trusted sender.
- If it is free or too good to be true then do not trust it.
- Before you donate to charity, research the company to make sure it is real. Use the Guidestar Nonprofit Directory to search for registered charities.
- Do not send money to people you do not know.
- If the subject line says urgent it’s most likely a scam.
- If buying any items, use scamAdviser to check website trust ratings.
[/stylebox]
The OPM Hack and Data Breach
The recent Office of Personnel Management hack was a data breach and espionage on a large scale – but who orchestrated it, and how could it come to pass? Read on for more info on what might be a modern day case of spying on an international level.
What was hacked?
The Office of Personnel Management within the federal government was hacked. Specifically, two systems were breached, according to Ars Technica. One was the Electronic Official Personnel Folder. The second was the central database behind EPIC, software that collects data for government employee and contractor background investigations.
Officials say the hack likely affected 14 million people – specifically personnel data and background investigation data. The stolen data included social security numbers, names, dates, birth places, and addresses as well as detailed background security clearance related information including finances, criminal history, and past drug use.
When did this happen?
The breaches were identified over a four month period in 2014 by two OPM investigative contractors, USIS and KeyPoint Solutions.
Who was responsible?
Current evidence points to a Chinese Cyber-espionage group dubbed “Deep Panda.” According to NPR, this has not been formally announced because, while they are convinced this is the case, this is the sort of espionage that many governments do and calling China out may be problematic.
Why did they do it?
Unlike credit card data breaches that we have seen recently, this was likely espionage. The information could be used as blackmail, given the depth of data that was stolen and the potential risk to people whose information was leaked. Anyone with security clearance could potentially have had their info stolen.
 How did the info get out and why wasn’t it caught?
How did the info get out and why wasn’t it caught?
According to Wired.com, multiple levels of failures were involved in the data breach. The OPM had no IT security staff until 2013. Equipment lacked appropriate encryption and inventory lists of servers and databases. The agency failed to use multi-factor authentication for systems abroad and when it was used, it was not encrypted appropriately. Arstechnica also explains nearly half the major IT systems were run by contractors which OPM’s security team had limited visibility into, but even internal systems lacked the basic security measures and security testing. Ars Technica says that some of the contracted companies may even have employed Chinese nationals from overseas as subcontractors.
It is also thought that an inspector general’s report released in November 2014 might have identified some of the problems in security with the OPM, and may have tipped off the hackers.
Investigations are also focused on the government shutdown in October 2013, where workers were furloughed and those who would have monitored FEC networks were not on the job at the time. It is possible a Chinese breach that occurred at the time might have helped hackers find vulnerabilities in that system to use later.
Court Notice Scam
“Court Notice” Mail Scam
 One of the more alarming new scams going around involves court notice emails prompting the user to open an attachment.
One of the more alarming new scams going around involves court notice emails prompting the user to open an attachment.
Lets take a look at the especially scary-sounding court notice scam to learn how to identify it, and avoid becoming a victim to this and other email scams like it.
It Says I Need To Go To Court!
This piece of spam arrived in a client’s email box to inform him that he had to appear in court.
The email did not explain why. It didn’t include any information on how to contact the court. It didn’t even mention a name.
It did, however, have an attachment.
When the attachment was opened the antivirus software kicked into gear, giving a malware warning.
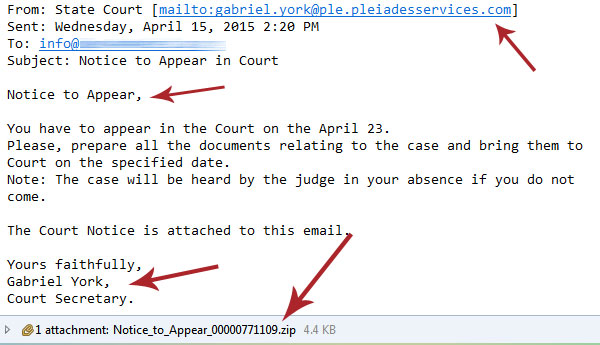
How You Can Tell This is Spam
There are a few things to watch for in suspicious emails; this one avoids some, but hits on others.
- What Is it? Would you be receiving this as an email? A notice to appear in court is a formal affair. You would receive a letter by mail, not just an unclear email with no name. And you generally opt in to receiving important correspondence through email anyway.
- The Recipient: In this case the email is being sent to an info@ email that is not addressed to any one person.
- The Sender: Check the sender’s address to see if it is consistent with what you would expect from a court email. In this case it is ambiguous; in some, it’s an obvious fake.
- Grammar: Are there typos, or is grammar terrible? In this case there are no typos and grammar is solid, but a lot of spam can be identified by grammar.
- The Attachment: The attachment is the big warning. In most notices a word document would suffice (even if they are not inherently safe). In this case a zip file is sent. Zip files can easily contain EXE files, programs that can put malicious software on your computer.
- Antivirus: Clicking on the file triggered the antivirus and told the user that malware was trying to infect his computer. He was lucky – software may not always catch everything, and opening attachments is not advisable.
[alertbox color=”yellow”]Always have some form of antivirus software on your computer, and make sure it’s automatically updating. [/alertbox][space10]
 What can you do?
What can you do?
- Mark Them As Spam: This may teach the email client that emails of this sort are no good. In the future they might go straight to the spam box.
- Antivirus: Everyone should have some kind of antivirus software on their computer these days, with no exceptions. Windows 8 comes with its own antivirus software, and anything older has plenty of options. Make sure your computer has one, and that it’s automatically updating.
- Call the Agency: If there is no agency, like this email? Odds are pretty good it’s a spoof.
- Don’t Respond: Responding to the email just tells the sender that your email address is ‘live’ and can be put on other spam lists.
Be aware of similar email and phishing scams:
- FedEx/Shipping Scam – These inform you that there is a problem with your delivery and that your shipping label is attached. The label is a zip file. Don’t open the zip file. If you are expecting something go to your original tracking mail or the website. If you aren’t waiting on a package? Disregard.
- Friends in Distress – These scams may use a friend’s email or name to alarm you into thinking they are stranded somewhere and need help or money. Contact your friend directly to see if this is a scam.
- Spear Phishing – This is one of the phishing scams that may target your organization or you as an individual and appear to be from a trusted source. It uses your name and sounds personal. The trick here is to be careful of your private info, and if something sounds suspicious, contact the presumed sender to confirm.
Email scams are not going away. The more you educate yourself on how to spot them and what to do about them, the less likely you’ll be to fall for them when distressed and alarmed.
[alertbox] Want to know more about email and internet scams? Visit our articles on Paypal Phishing, Domain Slamming, Ransomware, Energy Bill Service Scams, and Facebook Password Scams. [/alertbox]
Good WordPress Administrator Names
 Good WordPress Administrator Names
Good WordPress Administrator Names
WordPress lets you select your administrator name and by default, historically we have seen ‘admin’ come up as the most often used name. But using ‘admin’ as your username for WordPress is a potential security breach in the making. When hackers try to brute-force their way into a site, the first name they try is the old standby. There are better and more secure choices. Read on, for some options on good WordPress Administrator names.
Do’s:
- Your private email address; pick one you use that will not be placed
prominently on the site. - A memorable phrase; something with a few words that you won’t forget but won’t be apparent to a site visitor.
- A name with numbers or characters; any numbers will help.
- WordPress also permits symbols in its usernames.
Dont’s:
- Keep the default ‘Admin’
- An email address displayed on your site itself
- Your domain name
Wordfence monitors brute-force attacks, and we see ‘admin’ used in hacking attempts more than anything. You don’t have to make your WordPress username as complex as a password, but making it a little more creative and difficult to guess will make your site much more secure.
[alertbox]
For more on safe username and password use, read up on Protecting Your Facebook Passwords, Preventing Your Email From Getting Hacked, Securing Your Social Media, and a Facebook Password Reset Scam. [/alertbox]
Facebook Password Reset Scam!
Scam of the Day: Facebook Password Reset Scam
 [space10]
[space10]
The Email:
 Many of the phishing scams you may see in your mailbox are designed to alarm you into clicking, but look genuine enough at a glance so you don’t look that close. In a rush to fix things and at a cursory glance, you just click the links and do as instructed. Today’s phishing example, the Facebook Password Reset Scam does just that. And it’s rather sneaky about it.
Many of the phishing scams you may see in your mailbox are designed to alarm you into clicking, but look genuine enough at a glance so you don’t look that close. In a rush to fix things and at a cursory glance, you just click the links and do as instructed. Today’s phishing example, the Facebook Password Reset Scam does just that. And it’s rather sneaky about it.
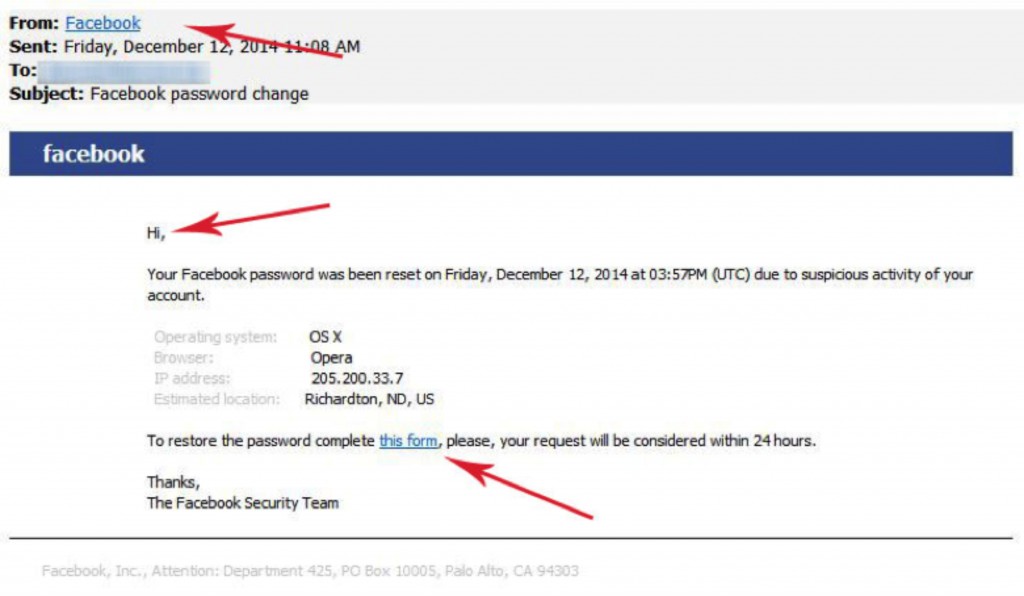
The email in question claims to be from Facebook and the subject simply says “Facebook password change.” Then comes the familiar blue Facebook header and the name.
The message gives cursory information with little detail and instructions you to click on a link and fill out a form in order to restore your password.
The Facebook Reset Scam:
This is a traditional email scam designed to get you to click on the link. The link does not go to Facebook. Instead, clicking either sends you to a form to submit private information, or the link may lead you to a site that will put malware on your computer.
How to Know:
This email is tricky and easy to mistake for the real thing but there are a few details to look for that can tip you off to understanding this is a scam.
1. Hover your mouse over the email link after “From”. In this case it claims to be from Facebook. Hovering over the blue link with your mouse turns up something different: At the bottom of your screen, you see that “@armcandys.co.uk” is the domain from the provided email, not Facebook!
2. Hover your mouse arrow over the other link in the email, “this form”, the one you are instructed to click on to reset your password. Instead of clicking, look again at the provided URL. In this case, we have an entirely different and unknown URL.
3. Often, social media, banks, and other sites that you have an account with will greet you by the name you have signed up through them with. It is uncommon that you will receive a serious piece of correspondence without any indication as to who the email is addressed to.
What To Do:
If you get an email like this and you’re not sure if it’s real or a scam, there are a couple ways to follow up.
1. Do NOT click on the link and follow instructions. Instead, go to your browser, type in the proper URL to the real site and see if you can log in. If you have no problem logging in, then your password has not been reset.
2. Ignore and delete the phishing email.
3. If you would like to follow up on it further, go to the Facebook website and see if they have any information on phishing. They may ask you to send a copy of the scammy email, and give you further instructions on what to do.
Scams of this nature, and phishing emails in general, tend to revolve around surprise and fear, operating under the assumption that the user will click and act without thinking.
We here at Appletree Mediaworks will continue to keep you informed on the nature of these scams so when one of them lands in your mailbox, you are better informed, can stop and think about what you are seeing, and be much better prepared.
[alertbox] Want to know more about email and internet scams? Visit our articles on Paypal Phishing, Domain Slamming, Ransomware, Energy Bill Service Scams, and Court Notice Scams. [/alertbox]