There’s an App for Labor Organization
![]() Businesses large and small have been told they need an app to take their marketing to the next level. It makes sense that labor unions are investing in apps to help promote their events and also help with organizing.
Businesses large and small have been told they need an app to take their marketing to the next level. It makes sense that labor unions are investing in apps to help promote their events and also help with organizing.
Yep There’s an App for That
I have so many apps on my phone I have to use the search feature to find one. But that’s ok; it’s still a nice central place from which I can access all of my favorite services and businesses. No searching the internet or flipping through saved emails for information. Of course we do need to caution you, before downloading any app learn where to download from and do your research.
Here are the big reasons why apps are so popular and necessary!
- The average person spends more than 2 hours a day on their mobile device. Your app is literally in their face two hours a day – your logo is sticking in their mind.
- There’s a lot of noise out there: newspaper ads, Facebook ads, websites, coupons and emails. But an app is one central location for a user to check in with your business or organization. You can also feed your website news automatically into an app.
- Apps put the information you want to share right at the user’s fingertips, no fumbling through website or old promotions.
- Push notifications – yes those short popups that get sent out and appears on phone screens get noticed and read, contrary to the trend that emails are following.
- Easy engagement – how many people prefer to communicate via a text message rather than a phone call? Your app gives them that option without searching for the correct phone number to use.
Using Apps for Your Union
Labor groups can win with an app for their union. We’ve worked with a large national union that first developed their national’s app and then offered pages of their app to each local. That was a solidarity win all the way around: no chasing faxes on bulletin boards or wondering whether the newest information was on the Facebook page or posted on a local’s website. The national’s website news was automatically fed into the app. Easy to use contact information, event information and petitions were all at their membership’s fingertips too. They also used push notifications to send out reminders about approaching deadlines and voting.
Apps to Help Organize and Inform
Apps have evolved from just delivering coupons and specials to going so far as to fight wage theft and help organize a union in the workplace. The online environment gives workers privacy and anonymity, both necessary elements in avoiding harassment, threats, retaliatory firings and increased scrutiny.
Here are some emerging apps uses that are helping labor:
Helping Fight Wage Theft
The Jornalero app for day laborers is an easy way to track payments, record details about unsafe work sites and share pictures to identify employers. Most of all, information is posted anonymously. Think Yelp or Uber for single event contractors. Input for the app came from artists, organizers, lawyers, workers and unions from across the nation.
Organizing Walmart
The WorkIt app is being used to help Walmart workers communicate with one another so they can learn about their rights as employees, as well as to develop strategies for improving workplace policies. While there are already a lot of online forums where Walmart employees gather to talk about issues at work, OUR Walmart wants to give employees a centralized hub to help them with all of their complaints and questions.
It’s obvious Walmart executives are worried about the app strengthening workers. They have gone out of their way to tell employees not to download the app. This could be the tool workers need to get the cards in and unionize this time.
Where to Get An App
There are several union app makers out there. As with any vendor, make sure their staff is union too so you’re all playing for the same team. Our staff here at Appletree MediaWorks, LLC does not build apps, but we have collaborated with several app builders and our clients to offer both technical insight and end user insight from our years of working with labor organizations. We excel at helping unions choose appropriate content for their apps and providing technical support to your maintenance staff.
Website Privacy: I Like Big Data I Cannot Lie
By now, most people understand that websites collect data behind the scenes (often without notice). You may even opt to volunteer information by filling out and submitting an online form. But what rights do the website owners have to your data? Who can they share it with? What are your rights?
These are all great questions that we’ll talk about in this article.
Privacy Policy
[space10]
Every website which collects data should publish a Privacy Policy. This is not only for the users’ sake but also to protect the website’s owners. This privacy policy should explain how the site owners may use and disclose your data, the types of collected data, and how a user can contact the owner if they have concerns.
Okay, so now you know where to look to find out how your data is being used and what your rights are. But what if you want to submit confidential information? If you own the website, how do you keep confidential information secure?
SSL Certificates
[space10]
SSL (Secure Socket Layer) certificates are the modern standard in website security technology. When you visit a site that has a properly installed certificate, a secure link is established between the web server and your browser. This link ensures that the data passed between these two points remains private and confidential. When you complete a form on an SSL secured website you can be assured that your data will be protected against interception. Even if it somehow gets intercepted by an unintended 3rd party, that person would only see garbled nonsense. Modern 256-bit encryption is so secure that even if 70 billion modern processors were focused on cracking a single value, it would still take 77 septillion years to crack it (that’s 77 followed by 24 zeros)!
You can tell if a website is protected by an SSL certificate by looking at the URL of the page you’re viewing – check if it starts with https:// (the “s” stands for secure). Also check to the left of the address to make sure a green padlock appears (or its equivalent in your browser of choice).
Data Process Protection
[space10]
As a user, once you verify that the site is SSL secured and has an agreeable Privacy Policy, clicking “Submit” still transfers control of your data over to the website’s owner. As an owner, it is important to regularly review internal protocols to make sure that you are living up to the published Privacy Policy. If your form has the potential to collect identifying healthcare information, this becomes a mandated legal requirement.
Online Form Sent to Email
[space10]
Some online forms send data directly to the recipient’s email address. Email is still one of the least secure forms of online communication. Often an email will get copied and stored in plain text on several servers during routine transit – a footprint which doesn’t disappear for years. For this reason, you should never email confidential information unless both the sender and recipient are using end-to-end encryption.
Products like Proofpoint offer email encryption for organizations. They also have products which scan incoming and/or outgoing email to ensure that their organization is not sending or receiving sensitive data – those emails get stopped by the gatekeeper. These are great tools to minimize risk.
Online Form Sent to 3rd Party Program
[space10]
There are many 3rd party products available that encrypt online form submissions and send them to a secure document server for retrieval using a private decryption key. The intended recipient may receive an email about the form but the email will not contain any actual data. You will still need to review the 3rd party product you’re subscribing to and ensure that their security procedures are adequate.
Appletree MediaWorks has experience collecting and securely storing online data and documents for our clients. We would be happy to discuss your company’s security needs.
Key points to a secure data system include:
- SSL Certificate on the entire website (this makes Google happy too)
- Secure Passwords and separate accounts for each user
- Document encryption and decryption process
- Document authentication and retrieval system
- A Web Application Firewall
- Storing documents outside of the live website
- Retrieving and viewing the uploaded documents only through SSL
- Audit report with logins, document access logs and IP addresses
- A procedure for truly deleting information off of servers and computers (multi-pass)
- MySQL injection prevention
- Training staff on proper privileged document handling procedures
Improper Data Procedures
[space10]
My family recently had an experience with an insurance company that collected lots of personal information on their paper application forms. They insisted on using paper applications because they were more “secure”. They cited concerns that the data might be hackable if it was online. As an IT professional, I knew it would be much easier to steal paper from a desk than it would be to hack it from a secure environment. But I trusted that this professional company had staff trained on proper document handling procedures.
The company then made a simple and foolish mistake. They scanned in our application and attached it to an email and sent it back to me with a question. We had a long discussion about the risk they just put our family in by sending this form over email. As IT professionals, we offered them other workflow options that did not involve sending secure data through insecure channels. They are now paying for identity theft services for our family because of their mishandling of our secure information. This is a good example of how improper training and knowledge of these issues can become very costly for a company – and how the right knowledge can help you hold companies accountable when and if your data is ever compromised.
Email is Not Secure
Email Is Not Secure Naturally.
Lately we’ve been hearing about email servers and scandals involved with email in the news. Some people have commented: “So what? Email is secure.” But it’s not, there are steps you must take to make your email secure! We have had clients ask us to email them passwords or other important information. We do not agree with being careless in the handling of very sensitive information. Instead, we pick up the phone and give them a call or use another method such as a trip to their office.
Email was not designed with any privacy or security in mind. Email was designed back when the internet was a much smaller place for simple messages.
How Can Email Get Intercepted?
Email must travel through several servers while making its way from sender to recipient. A message sometimes “hops” through more than a dozen servers on its journey. Each server it touches is mandated by law to store the message, sometimes for several years afterwards. Furthermore, the distance traveled between hops is often spent unencrypted.
The networks where your emails pass through are a series of routers and switches. All of these connections are owned by different people with varying security standards. It is safest to assume that anything you write in an email can be intercepted and read by anybody, as if it had been published to the front page of a newspaper.
Email servers are where your messages are physically stored before being downloaded to your email browser. Email servers are insecure by default. If a message was originally sent unencrypted across unencrypted networks, it’s going to come onto the server unencrypted.
Even after reaching its intended destination, many computers do not have a login screen or a lock screen code – same with many phones and tablets. If you leave your tablet at the local coffee shop with no lock code, for example, you’ve just compromised all of the email stored inside.
What Are My Options to Keep My Email Secure?
Encrypted Email
Use end-to-end encryption. This is a process which scrambles the message using a complex mathematical formula that can only be solved using a long public key stored on the receiving end. This can prove to be logistically daunting depending on the number of people you contact regularly. This is because all of them must have a copy of your public key set up in their email program in order to read your emails. Even with this type of encryption, email headers are still left open. You won’t be able to hide who you are sending an email to. The NSA has even touted scanning email headers for information during digital pat downs.
Mix It Up
You could send an email to a client letting them know that you’re texting them a password, for example. Then send the text with no additional references about what it’s for. Sending sensitive messages in multiple parts using different channels reduces the likelihood that a man-in-the-middle will receive enough information to do damage.
Use a Service
For sending passwords, LastPass is still one of the most secure services around. You can share passwords in LastPass with other LastPass users.
Messaging apps get mixed reviews from a security standpoint. For example, Skype used to be considered a good encrypted chat service. That is, until it was confirmed that Microsoft had built in a dangerous back door for themselves. Even if you trust Microsoft, back doors very seldom go unexploited once they’re known to exist.
File Services
Services like DropBox are also useful and fairly secure. Since Dropbox encrypts everything you upload and download over a secure HTTPS connection, your file transfer should be secure from start to finish, though mobile DropBox is not secure. You could also create and send an encrypted ZIP file.
Staying Secure
It’s important to continue downloading and applying updates for the services you use. Even if you are using a mainstream app, it could still be insecure if you haven’t updated it lately. For a long time, iMessage was thought to be secure. Then vulnerabilities were found and Apple had to release security patches to close those holes. If you’re not sure about a security patch, visit the provider’s website and check their support area for recent updates.
Why It’s Important to Clean Up Your Website
Dust off your mouse and grab your website administrative login, it’s time to clean up your website.
If you’re running late on your spring cleaning, it’s ok. You have a week before summer. Your website and online presence all need to be cleaned up regularly too, so why not now? There are many reasons you need to clean and update your website.
Keep Your Website Professional
Take the time to click through your website as a user. You’d be surprised how many updates you find that should be made, or realize that you have additional information available but it hasn’t been added to the website yet. If your homepage is still displaying information about a past event as “upcoming” you are wasting prime space and sending the wrong message to your visitors.
Website Load Time
Cool websites look great on a large monitor and can be programmed to be responsive to mobile screens, but there is an extra part to this: Load Time. Website speed issues will cause a visitor to leave your site before they even see what your cool website has to offer.
Some steps to take to decrease your load time:
- Get a great website host. Page speed starts with how fast files are served by your web host. While there is no one perfect solution for hosting your site, do not mindlessly sign up for a hosting plan without researching performance and reviews.
- Decrease the number of installed plugins. There’s a good chance your website is not using half of the plugins you have installed, and there are huge security issues if your plugins are not kept up to date.
- Clean up outdated posts and articles on your website. Those articles can add to load time.
- Optimize your website images. Use a photo editing program to optimize images before uploading to your website. Delete unused images from your media library.
Consumer Confidence
With fake reviews circling the internet and companies like Yelp & Amazon suing those selling or creating fake reviews, it is important to create an online experience users can trust. Start by sending review request emails to verified purchasers as a way to collect authentic content.
Don’t edit reviews, not even grammatical errors – they actually help build authenticity in the eyes of your customers.
Increase Search Engine Optimization
Keeping your website load time down is an important piece of search engine optimization. But have you given thought to what services or message your organization wants to communicate? Now is a good time to check what SEO keywords are on your website and match them to your goals. Does content match up with the assigned keywords? Do image names and alt tags coincide with your goals? Are the keywords in titles and content?
But I Hate Cleaning
Hate is a strong word. It’s more likely you just don’t have time, or it’s too overwhelming. If that’s the case for you, it’s time to bring in a professional. Give Appletree MediaWorks a call – we’ll discuss your online goals together and provide our professional services at an affordable price.
Chinese Internet Censorship Holds Back Freedom
Earlier this month we celebrated the World Day Against Cyber Censorship. This is a rally for an unrestricted internet and a fight against governments deterring and censoring online free speech.
Amnesty International notes that China “has the largest recorded number of imprisoned journalists and cyber-dissidents in the world“. They remain the leading example of the problems cyber censorship creates. The government blocks many websites, searches, and software based on content alone. Now a new rule could make Chinese Internet censorship even more restrictive for its citizens.
Search Word Blocking
China blocks searches that involve a negative take on the government, sociopolitical matters, etc. You may get a “page cannot be displayed” error or a very skewed version of the results – see below for examples
Examples of search words that will give users a “page cannot be displayed”
 Persecution
Persecution- Tibetan Independence
- Tienanmen Square
- Democracy Movements
- Oriental Red Space Time (code for an anti-censorship video)
Website Blocking
China blocks many sites simply because of their content. They block all social media except for Chinese based social media sites because of the difficulty they have complying with censorship rules. Although recently, Mark Zuckerberg has still been trying to get Facebook in China. Google also tried to make a censored version of its search engine for China but was repeatedly banned and eventually gave up.
Examples of sites that are currently blocked in China
 Google (Which includes YouTube and Gmail)
Google (Which includes YouTube and Gmail)- New York Times
- Dropbox
Microsoft’s Windows 10
Microsoft recently created a version of Windows 10 to fit the strict rules of censorship in China. They partnered with a state-run technology and defense company, CETC. Microsoft is not giving very much information away about how they have changed their product to make it comply, only that it doesn’t have the same apps, services, or additional device management and security controls.
The Internet Domain Name Management Rules
 Just when you think China’s Internet censorship cannot get more strict, its government announced on March 28th that websites will be more strictly managed within China under the draft Internet Domain Name Management Rules. The new rules would make sites register domain names with local service providers and with the authorities.
Just when you think China’s Internet censorship cannot get more strict, its government announced on March 28th that websites will be more strictly managed within China under the draft Internet Domain Name Management Rules. The new rules would make sites register domain names with local service providers and with the authorities.
It is not clear whether this is going to apply to all websites or just those that Chinese servers host. As of right now, the rule is only a draft and will be going to the Chinese Ministry of Industry and Information Technology on April 25th, which will then determine if this affects websites globally or locally.
 If this does apply to all websites then the global Internet might die at China’s border. Many domains would not make it by the new rules and authorities would block much of the content.
If this does apply to all websites then the global Internet might die at China’s border. Many domains would not make it by the new rules and authorities would block much of the content.
 If this only applies locally this would make it much more convenient for the Chinese government to censor websites.
If this only applies locally this would make it much more convenient for the Chinese government to censor websites.
To explain how restrictive the rule would be, Article 28 lists out what is not allowed to be in a domain name. Here are just a few of the stipulations:
- jeopardize national security, leaking state secrets, subverting state power, undermining national unity;
- incitement to ethnic hatred, ethnic discrimination, undermining national unity;
- spreading obscenity, pornography, gambling, violence, homicide, terror or instigate crimes;
- insult or slander others, infringe upon the legitimate rights of others;
US Search Engine vs The ‘Great Firewall’ Search Engine
You can surf the web comparing Google in the US and the comparative Baidu in China to see the difference in censorship. The traveling pop-up Firewall Internet Cafe even sets up computers specifically so its customers can experience China’s great firewall firsthand. Different results show up depending on the topic.
Photo Source hyperallergic.com
Example: Tiananmen Square
“Google pulls up the famous image of the “tank man,” among other photographs related to the June 4, 1989 massacre; Baidu, however, finds scenic snapshots of the city square. The browser also posts a line above the results that notifies users of the sensitivity of their search subject.”
How America Fights to Keep the Internet Open and Free
Net Neutrality
In America we have an open internet through Net Neutrality from the FCC. This means that we all have the right to communicate freely online, protecting our first amendment of Freedom of Speech. This also means that no internet provider can block, throttle, or discriminate against any applications or content on their networks.
Some things China has done such as blocking websites completely and filtering out results from searches, are examples of why we have Net Neutrality. This does not mean that we should take Net Neutrality for granted. In fact, it has so far withstood a barrage of attacks, specifically from Congress and cable/phone companies (Such as Comcast and Verizon).
To help Save the Internet, visit Free Press.
Proposed Acts in the US that Promote Online Censorship
Stop Online Piracy Act (SOPA)
This act would expand US law enforcement to stop copyright infringement but many worry that this promotes censorship.
PROTECT IP Act (PIPA)
The Preventing Real Online Threats to Economic Creativity and Theft of Intellectual Property Act, or PIPA, was a proposed law to give governments and copyright holders tools to curb access to “rogue websites dedicated to the sale of infringing or counterfeit goods”. This road leads directly to a censored Internet.
EU-US Privacy Shield Still Not Protecting Your Privacy
EU-US Privacy Shield Still Not Protecting Your Privacy
Full text of the new draft EU-US Privacy Shield was released February 29th but has not been signed yet. They have made some changes from the previous Safe Harbor Agreement. While some are good improvements, some seem to have not changed how our data is handled at all. A conclusion on if the draft agreement will be acceptable should be made by mid-April to the end of April.
History: Safe Harbor Agreement
Before going in to the Privacy Shield here is the history of why we needed a new agreement between the European Union and United States. In an earlier blog, Safe Harbor Ruled Invalid, How it Affects You, we talked about the invalid ruling of the Safe Harbor Agreement and how it affected businesses and consumers. So here’s a little history on the old Safe Harbor Agreement:
The European Union (EU) and the United States (US) established the Safe Harbor Pact in 2000. This allowed businesses to legally funnel info across the Atlantic. Common data storage and transfers might include global commerce, sending and receiving emails, and even posting on social media. US companies can “self-certify” that they meet the stricter European privacy standards.
In early October of 2015, the European Court of Justice found the US approach to domestic surveillance and absence of legislation governing certain privacy rights was not up to European standards following a case brought by an Austrian student Max Schrems. The EU then made the Safe Harbor pact invalid. They believe the US has compromised their data and would like for some changes to happen to ensure the US is not spying on their citizens.
What’s New
 While there are some improvements to the Trans-Atlantic data transfer deal many say it does not differ much from the original Safe Harbor and does not address the “core concerns and fundamental flaws of US surveillance law and the lack of privacy protections under US law.”
While there are some improvements to the Trans-Atlantic data transfer deal many say it does not differ much from the original Safe Harbor and does not address the “core concerns and fundamental flaws of US surveillance law and the lack of privacy protections under US law.”
Key Positive Takeaways:
[space10]Citizen and Company Complaints
 The new agreement gives companies and citizens the chance to complain and dispute any mishandling of records and personal information. Governments must resolve such complaints within 45 days or use a free “alternative Dispute Resolution”.
The new agreement gives companies and citizens the chance to complain and dispute any mishandling of records and personal information. Governments must resolve such complaints within 45 days or use a free “alternative Dispute Resolution”.
Ombudsman
An ombudsman is a public advocate representing the interests of the public by investigating and addressing complaints. An ombudsman within the US State Department will handle any allegations of privacy violations.
Key Negative Takeaways:
[space10]Collecting Data in “Bulk”
In a Press Release from February 29th the European Commission states there will be “no indiscriminate or mass surveillance by national security authorities.” But then is contradicted by this:
6 exceptions where US can collect data “in bulk”:
- Detecting and countering certain activities of foreign powers
- Counterterrorism
- Counter-Proliferation
- Cybersecurity
- Detecting and countering threats to US or allied armed forces
- Combating transnational criminal threats, including sanctions evasion
US Judicial Redress Act
 In addition to the Privacy shield, President Obama signed the U.S. Judicial Redress Act on February 24th that will “give EU citizens access to US courts to enforce privacy rights in relation to personal data transferred to the U.S. for law enforcement purposes. ” […] The Judicial Redress Act will extend the rights U.S. citizens, and residents enjoy under the 1974 Privacy Act also to EU citizens.”
In addition to the Privacy shield, President Obama signed the U.S. Judicial Redress Act on February 24th that will “give EU citizens access to US courts to enforce privacy rights in relation to personal data transferred to the U.S. for law enforcement purposes. ” […] The Judicial Redress Act will extend the rights U.S. citizens, and residents enjoy under the 1974 Privacy Act also to EU citizens.”
At first that sounds good. After further research on the Privacy Act of 1974, many believe that the Privacy Act is “worthless”, with similar views from the Electronic Frontier Foundation (EFF),. There are many exceptions including 32 CFR 322.7 which exempts the NSA from rules of privacy on records maintained on individuals, according to 5 U.S. Code § 552a.
“Essential Equivalence” Non-Existent
 One of the most important parts of changing this agreement was to have “essential equivalence” of European data protection in the US. Max Schrems points out that this deal falls short:
One of the most important parts of changing this agreement was to have “essential equivalence” of European data protection in the US. Max Schrems points out that this deal falls short:
“The new deal does not even address the matter of private sector data misuse, despite the fact that there would have been much more leeway than in the government sector. There are tiny improvements, but the core rules on private data usage are miles away for EU law.”(TechCrunch)
 Privacy Shield Certified
Privacy Shield Certified
Under the Privacy Shield a business can become ‘certified’ to establish “adequate” protections for Trans-Atlantic data transfers. While this helps to protect your business from data transfer problems, it does not protect you completely.
The new agreement allows Data Protection Authorities (DPAs) to suspend data flow regardless of a business being Privacy Shield Certified. This would mean you cannot secure continuous data flow for your company.
The Outlook
 The EU-US Privacy Shield still needs to be approved by the EU’s WP29, also known as the Article 29 Working Party, and from the privacy issues others have already found in the draft it does not seem likely it will be approved.
The EU-US Privacy Shield still needs to be approved by the EU’s WP29, also known as the Article 29 Working Party, and from the privacy issues others have already found in the draft it does not seem likely it will be approved.
“They tried to put 10 layers of lipstick on a pig, but I doubt the court and the DPA’s now suddenly want to cuddle with it”
-Max Schrems
NSA Surveillance and Online Privacy
Who are the NSA?
The National Security Agency (NSA) is a powerful United States intelligence organization. Basically, they are responsible for collecting, processing, and monitoring global data for intelligence purposes. The NSA has a stated role to advance national security while protecting the freedoms, civil liberties, and privacy rights guaranteed by the Constitution and federal law.
What is the issue?
Many studies, cases, and documents show that the US government is spying on American citizens using online NSA surveillance. As Americans, this invades our Freedom of Speech and our Right to Privacy. The ACLU has called this activity “unconstitutional surveillance of Americans’ communications”.
Some Examples
An internal NSA audit from 2012 revealed they committed 2,776 incidents of unauthorized surveillance of Americans or foreign targets in the US over a one-year period.

On May 20, 2013, Edward Snowden released files from the NSA which described, as he put it, “systematic surveillance of innocent citizens.” Based on Snowden’s documents, the NSA has at least nine major tech companies gathering data on selected surveillance targets. This revelation caused online privacy concerns to increase dramatically in the US.
Then on Dec 24, 2014, a Freedom of Information lawsuit filed by the ACLU revealed NSA documents from 2001 to 2013. Overall, these documents showed that there were instances of unauthorized surveillance of US organizations, spouses or love interests, and more American citizens.
What is a Digital Pat Down?
The inner workings of an intelligence machine like the NSA can be difficult to grasp. From leaked documents so far, we can surmise that the NSA is performing secret “digital pat downs” on American citizens somewhat regularly. This happens without our knowledge or consent.
First, an NSA analyst identifies a target and submits a request to the FBI’s Data Intercept Technology Unit. Next, dedicated employees at various tech companies receive the request and gather the requisite data. This may include emails, chat logs, and videos. Once the data is compiled, it is sent back to the FBI for analysis.
The National Security Agency is also piggybacking on the tools that enable Internet advertisers to track consumers, using “cookies” and location data to pinpoint targets for government hacking and to bolster surveillance. We’ve talked in detail about mobile phone tracking tools previously.
They are also collecting location data transmitted by mobile apps. An NSA program, code-named HAPPYFOOT, helps the NSA to map Internet addresses to physical locations more precisely than is possible with traditional Internet geolocation services.
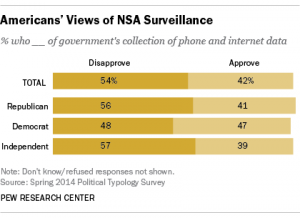 How do Americans feel?
How do Americans feel?
PEW research shows what Americans think about online privacy and the NSA.
Overall, 54% of Americans disapprove of the US Government collecting telephone and Internet data for anti-terrorism efforts.
74% said they should not give up their privacy and freedom for the sake of safety.
93% think it is important to control who can get their information.
38% think they have only some control over their own information.
Cyber Legislation
CISPA had alarmed the privacy community by giving companies the ability to share cyber security information with federal agencies, including the NSA, “notwithstanding any other provision of law.” That means CISPA’s information-sharing channel, created for responding quickly to hacks and breaches, could also provide a loophole in privacy laws that would enable warrant-less intelligence and surveillance. The information they gather, including all hacked data and any incidental information swept up in the process, would be added to a massive database. The FBI, CIA, and NSA would then be free to query this data at their leisure.
This is how CISPA would create a huge expansion of the “backdoor” search capabilities that the government uses to skirt the 4th Amendment and spy on Internet users without warrants and with virtually no oversight.
How to prevent being spied on by the NSA and other data collectors without going off the grid
It may be impossible to completely prevent the NSA from spying on you, but you can try and make it much harder.
- Avoid popular Online Consumer services – These include Google, Facebook, and DropBox.
- An alternative to DropBox is SpiderOak.
- A common alternatives to Google is DuckDuckGo.
- Mashable has published a list of private social networks to help you avoid the Facebook plague.
 Encrypt your hard drive – You may have password protection on your files but you should go a whole step further and encrypt the entire hard drive.
Encrypt your hard drive – You may have password protection on your files but you should go a whole step further and encrypt the entire hard drive.
- Avoid online tracking – On you browser you can use the do-not-track setting but you can go a step farther and use a plugin to stop tracking. Some reputable plugins for this include:
- Encrypt your email and chat messages – Encrypt your messages before you send them. Some common email clients with encryption include:
- Microsoft Outlook – This has encyption options if you want to use them.
- Runbox (a Norwegian secure email client) – Claims to be unreachable by the NSA.
- HushMail – Not as popular but is completely encypted.
If you chat on the Internet, you can encypt those messages too.
- ChatCrypt – Encrypts the message when it sends and can only be read by the end user, also known as end-to-end encryption.
If you use common instant messaging through Google, AOL, Yahoo or Microsoft you can use a chat extension called OTR (Off the record) which enables end-to-end encryption.
- Use TOR for online browsing – TOR stands for The Onion Router. Like an onion, it layers multiple levels of security. Basically, it bounces communication around a network of relays which makes it very difficult to track.
 Many browsers also have a private mode.
Many browsers also have a private mode.
- Firefox – Private Browsing
- Chrome – Incognito mode
- Internet Explorer – InPrivate feature
Online Privacy in Europe
A recent draft of the British Investigatory Powers Bill will require companies to store information for up to a year. Communications companies would hold details of which websites and apps a person uses.
 Recently, the European Union has decided to invalidate the current voluntary safe harbor because they believe the US cannot adequately protect its privacy. There have been reports that European companies are transferring data out of US territory for safe keeping.
Recently, the European Union has decided to invalidate the current voluntary safe harbor because they believe the US cannot adequately protect its privacy. There have been reports that European companies are transferring data out of US territory for safe keeping.
EU-US Privacy Shield
The US Government released full text of the new European Union-US Privacy Shield on Feb 29. This is not yet law.
Citizen complaints – The new agreement gives companies and citizens the chance to complain and dispute any mishandling of records and personal information.
Targeted spying – This will now be limited to: detect and counter threats from espionage, terrorism, weapons of mass destruction, threats to the armed forces, or transnational criminal threats.
The proposed framework includes the following features:
- Companies must provide greater transparency with respect to their data collection, use, and sharing practices through more robust and detailed privacy policies
- If a company handles human resource (employee) data, it must agree to cooperate and comply with EU Data Protection Authorities (DPAs)
- Companies transferring personal data to third-party service providers remain fully responsible for the proper handling of personal data; must conduct appropriate due diligence concerning its service provider; and must properly monitor and re-mediate any deficiencies of its service providers relating to the handling of personal data
Our Advice
Ideally, companies should give consumers control over the information they divulge. This becomes even more urgent since corporations so freely share information with government authorities. Until consumers begin reading those 30-page privacy policies rather than blindly accepting them, they will continue falling for the same traps. Generally, as consumers we must understand that the “free” services we consume are actually very expensive. It often comes at the price of our privacy. So take a long hard look at the next privacy policy you’re asked to accept. You may be better served just paying cash instead.
Social Media Copyright Issues: Fair Use or Infringement?
Social media copyright issues have become a hot topic in recent months. Nearly everyone has shared something on social media that was copyrighted by someone else. But what is fair to use on social media and what infringes on the rights of the copyright holder?
Is it fair use or infringement?
If you do not get a license from the copyright holder then the only way to use the content is through something called “fair use”.
What is fair use?
Generally, fair use covers any copyrighted material that was shared with a “transformative” purpose. This might constitute a comment, criticism, or parody accompanying material. Such sharing can take place without permission from the copyright owner.
Categories of Fair Use
- Commentary and Criticism – Commenting upon or critiquing copyrighted material. Examples include online reviews, news reports, education courses, or court case.
- Parody – A parody takes copyrighted material and ridicules it in a comedic way.
Fair Use Checklist
Not sure if you’re allowed to share something under “fair use”? Run it through this checklist to be sure before you post.
☐ Purpose and Nature of Use
The use of copyrighted material must be “transformative”. This means you took the time to add new meaning or value to the copyrighted material with new information, aesthetics, insights, or understandings.
Example of Fair Use: Google images – All Google images are copyrighted by the owner. Google’s use is considered “transformative” because it displays pictures in a different way, for a new purpose.
Example of Fair Use: Scary Movie Series – This movie series is a parody which borrows copyrighted material in order to ridicule it. Producers added value using new information, aesthetics, insights, and understandings.
Example of Infringement: Posting a copyrighted image on social media is for aesthetic or entertainment purposes. This is likely NOT a different use than the copyright holder intended and does not transform the work.
☐ Nature of the Work
Using copyrighted information has more leeway in fair use than copyrighted creative works. Also, there is more leeway in using published work rather than unpublished work.
☐ Amount and Substantiality of the Portion Used
Less is more. Meaning the less you use of the copyrighted material the more likely it will be considered fair use.
Exception: Using the most memorable (although small) part of a copyrighted work, such as the opening riff of “Sweet Child O’ Mine” by Guns N’ Roses.
Exception: Parodies – Quite a bit of a copyrighted material, even the heart of the material, can be used for parody. The Supreme Court acknowledges that “the heart is also what most readily conjures up the [original] for parody, and it is the heart at which parody takes aim,” as decided in Campbell v. Acuff-Rose Music,510 U.S. 569 (1994)
☐ Effect of Use Upon Market or Value
If you deprive the copyright holder income or undermine copyrighted work that could have potential market it is not fair use and you are most likely looking at a lawsuit. This holds true even if you are not using the copyrighted work directly.
Example of Infringement: An artist used a copyrighted photo to produce wood sculptures and earned a lot of money selling them. Even though the photographer did not plan on make sculptures it was considered a potential market and the court ruled in favor of the photographer.
[alertbox color=”blue”]MYTH
If you list a source, using copyrighted material is permissible.[/alertbox]
This is probably the most popular myth about copyrighted material. Even if you list your source, using copyrighted work without permission is still an infringement, especially if you are making income from it.
☐ Check Original Source
Sometimes the original source will have copyright notices. If you are unsure, be safe and obtain a license from the copyright holder.
 ☐ Check Social Media Terms and Conditions
☐ Check Social Media Terms and Conditions
When someone posts original work on social media, you should check the authorization to re-post, re-tweet, or re-pin that content. Read our blog article Social Media Content Rights for more detail.
Example: Pinterest’s term of service states that if a user posts content on Pinterest they are providing a license to all other users to use that content on Pinterest.
☐ Post a link instead of content
On social media, post a link to the original source of the material instead of the material itself. While this is still infringement, the chances of a complaint are much lower (especially since everyone does it). This does support a fair use defense.
☐ Keep Sharing Within Network
When you find content on social media you want to share, keep it within that network. Always read the terms and services before sharing.
[alertbox color=”blue”]
MYTH
Content posted on social media is fair game.
[/alertbox]
Some may think that if the content is on social media then it is fair game to use. This is not the case – the copyright still belongs to the copyright holder.
 You can be held at fault for posting copyrighted material or even sharing something someone else posted that was copyrighted. This seems to happen so frequently on social media that the chances of litigation are low, but it’s still a risk.
You can be held at fault for posting copyrighted material or even sharing something someone else posted that was copyrighted. This seems to happen so frequently on social media that the chances of litigation are low, but it’s still a risk.
U.S. Copyright Office Fair Use contains comprehensive information if you’d like additional information.
Is Your Smart Phone Spying on You?
Is your smart phone spying on you? In short, yes. Follow the simple guide below to find out how to protect yourself.
Apple
 Frequent Locations
Frequent Locations
iPhones track your location data down to the minute.
Who uses this information:
- Third party advertisement: If you visit a shoe store, you might receive shoe advertisements.
- Apps: Apps may request permission to access your frequent locations. This may be useful for some things such as viewing local weather or calculating ETAs from your location.
![]() How to stop it:
How to stop it:
- Settings > Privacy > Location Services > System Services > Frequent Locations
- There is a toggle for turning on and off frequent Locations and Improve Maps
 Identifier for Advertising (IDFA)
Identifier for Advertising (IDFA)
This allows developers and marketers to track your activity. They use this data for targeted advertising on apps and web pages.
![]() How to stop it:
How to stop it:
- General > About > Advertising
- There is a toggle to turn on Limit Ad Tracking
Microsoft
 Windows 10
Windows 10
The new updated Windows 10 tracks just about everything you do.
Here is a section of the Windows 10 terms:
Finally, we will access, disclose and preserve personal data, including your content (such as the content of your emails, other private communications or files in private folders), when we have a good faith belief that doing so is necessary to: 1.comply with applicable law or respond to valid legal process, including from law enforcement or other government agencies; 2.protect our customers, for example to prevent spam or attempts to defraud users of the services, or to help prevent the loss of life or serious injury of anyone; 3.operate and maintain the security of our services, including to prevent or stop an attack on our computer systems or networks; or 4.protect the rights or property of Microsoft, including enforcing the terms governing the use of the services – however, if we receive information indicating that someone is using our services to traffic in stolen intellectual or physical property of Microsoft, we will not inspect a customer’s private content ourselves, but we may refer the matter to law enforcement.
![]() How to stop it:
How to stop it:
Many methods are available, with varying effectiveness:
- InPrivate Mode – Setting you browser to InPrivate mode does not completely cover your tracks
- Unchecking all tracking pages upon opening – This has been tested (even with a DisableWinTracking tool) and found it still tracked some information.
Google/Android
 Voice Commands
Voice Commands
Every voice command you make on your android phone is logged. These recordings should only be available to you but the idea of possibly having any personal information stored may be unnerving to some. Every Google device records and stores voice commands.
![]() How to stop it:
How to stop it:
- Settings > Account > Google > Sign In > Personal Info & privacy > Activity Controls > Voice & Audio Activity
- There is a toggle to turn this off. You can also delete all saved recordings.
 Location Tracking
Location Tracking
Just Like Apple, Android tracks your location. Google doesn’t limit their tracking to cell phones. They continue tracking you from your desktop computer, if you leave your Google account logged in.
Who uses this information:
- Third party advertisement: If you visit a shoe store, you might receive shoe advertisements.
- Apps: Apps may request permission to access your frequent locations. This may be useful for some things such as viewing local weather or calculating ETAs from your location.
![]() How to stop it:
How to stop it:
- Settings > Account > Google > Sign In > Personal Info & privacy >Google Location History
- The you can toggle this off and you can delete location history
 Android Advertising ID
Android Advertising ID
Similar to Apple’s Identifier for Advertising, Google takes information from your search activity to use for targeted advertising. You see these within apps downloaded from Google Play.
![]() How to stop it:
How to stop it:
- Settings > Account > Google > Sign In > Personal Info & privacy > Ads Services
- This will take you to a web page to manage the ad settings. Then you can toggle it off.
- You can also reset the ID which clears past data. This can be helpful if you still want to see ads tailored to you but not about something you recently searched about. You can even delete and add interests to better tailor the ads.
This will not stop the ads but will stop the targeted ads based on your search history.
How to Download Apps Safely
As of July 2015, the Google App Store has 1.6 million apps and the Apple App Store has 1.5 million apps. With an ever-growing universe of apps available, the chances of getting a compromised or infected app are on the rise.
More than 85 billion apps have been downloaded from the Apple App Store since October of 2014 and that number is growing substantially. All that traffic leaves a lot of room for hackers to gain a footing. To stay safe, you should take precautions, learn which download sources are reputable, and do a little research.
Take Precautions
Before even looking for apps for you device you need to guard yourself against any malware that might get through. Before installing anything new, make sure that your device’s operating system and existing software are fully up to date.
 Anti-virus and Firewall – Use an anti-virus application that scans every app you install. It should also scan updates and block malware.
Anti-virus and Firewall – Use an anti-virus application that scans every app you install. It should also scan updates and block malware.
Stay Updated – Update your web browsers and operating systems. Updates to these often include important security patches. Once a security patch is released to the public, you have very little time to apply the update before hackers have figured out how to exploit it. This is why it is so important to update early and often!
Where to Buy and Not to Buy
Buy from Here…
Google App Store, Apple App Store, Windows Store – For all devices, use the default app store that comes installed with the device. Most app stores have a screening process which weeds out most malicious code. If you do happen to find something bad, you can report the app to: Google, Apple, or Windows
Not from Here…
DarkSideLoader
The DarkSideLoader is a rogue app store for iOS phones and tablets. This app store lets user download unusual, unapproved apps alongside normal apps which are offered free of charge (as in stolen).
What are the Dangers?
Downloading compromised apps from DarkSideLoader can make you lose control of your phone and receive unwanted installations. Compromised or malicious applications can be very dangerous to your phone and personal information. Here are a few examples of what these “rogue apps” can do to your phone:
- Operating System Access Through API Access
- Root Devices
- Install Apps Without Permission
- Communicate With Malicious Sites on Internet
- Malware Installation
Any third party app store can have these potential problems
Check if you have a rogue app on your Android device
Do Your Research
There are many things you can look for to check if an app is dangerous. While it can be easy to just click download, you should do a little research beforehand. Here are a few common safety checks:
 Reviews – Read some reviews about the app. If there is a known problem it will most likely be expressed in a review. You can find reviews in the app store you are using.
Reviews – Read some reviews about the app. If there is a known problem it will most likely be expressed in a review. You can find reviews in the app store you are using.
Developer Information – Research the developer to find out how popular they are. Make sure the developer exists in the real world. Usually there is a link in the app store to the developer’s website. Browse through some of the top app developers of 2016.
Permissions – Make sure to read and understand the permissions before granting anything to a new app. Learn more about permissions and why apps need access to certain things.
Star Ratings – Similar to reviews, a star rating will most likely be fairly low if users experienced problems with the app. Again, this is available on the app store you are using.
Download Count – If an app has a high download count the chances of it being safe are higher.
![]()
Outside Forums – Still not sure? Google the app and find out what others are writing about it. Users love to post information like this to Reddit or other discussion forums.












