Scam Emails
 Scam emails are a very popular and while most email services have a spam sorting feature built in, not all will be sorted properly. Scams can look like they came from a friend, a business you interact with or do not interact with, federal agencies, charities, or complete strangers.
Scam emails are a very popular and while most email services have a spam sorting feature built in, not all will be sorted properly. Scams can look like they came from a friend, a business you interact with or do not interact with, federal agencies, charities, or complete strangers.
There are ways to notice whether the emails are legitimate or not. There are extra precautions you can take for those that may not be as noticeable but still suspicious. However sometimes you do fall victim to these and there are some steps to take if that happens.
Common Types of Scams
There are so many types of email scams out there but some of the popular ones include bogus offers, phishing, Trojan Horse, and request for help.
Bogus Offers
These usually involve discounted or free items or too good to be true products or services. Your best bet if it sound too good to be true then you are probably right.
Bogus Business Opportunities
 Subject Lines: Make a Regular Income with Online Auctions, Put your computer to work for you!, Get Rich Click, or Use the Internet to make money.
Subject Lines: Make a Regular Income with Online Auctions, Put your computer to work for you!, Get Rich Click, or Use the Internet to make money.
Scam: Most of these contain links that either contain malware, bring you to bogus sites that ask you to enter personal information or pay for an “information kit”
Health and Diet Scams
Subject Lines: Need to lose weight for summer?, Reduce body fat and build lean muscle without exercise, CONTROL YOUR WEIGHT!!, or Takes years off your appearance.
Scam: Most contain links that contain malware. Some may contain fake customer testimonials to convince you.
Easy Money or Free Items
Always avoid anything with these similar titles. It is almost always a scam.
Scam: They usually lead to a website you have to enter your information in to steal it or ask for some sort of fee for “processing” or “shipping”.
Phishing
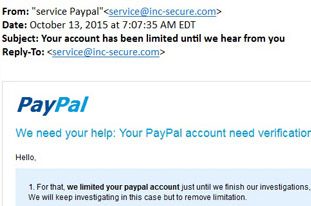
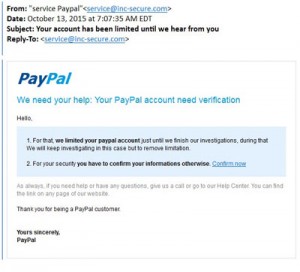 The definition is in the name, these are people “fishing” for your information. These types of scams exploit existing companies that you may or may not interact with. Using a popular companies name can make you believe the email is real.
The definition is in the name, these are people “fishing” for your information. These types of scams exploit existing companies that you may or may not interact with. Using a popular companies name can make you believe the email is real.
Account or Credit Information
Subject Lines: Your account is going to expire!, You’re Pre-Approved, or Guaranteed credit card
Scam: This will most likely contain a link that downloads malware, more specifically a keystroke logging malware so when it directs you to the convincing but fake website it steals your sensitive information.
Trojan Horse
These are emails that contain attachments. They usually promise something funny, a photograph, or a patch for software vulnerability.
Subject Line: Funny, Hi Friend, Check it out!
Scam: These attachments contain malware making your device vulnerable and possible installs software stealing your information.
Requests for Help
Disaster Relief
Fake charity websites are created to get people to donate money to a disaster such as 9-11 or Katrina.
Scam: Link inside email will direct you to offer your bank or credit card information to steal.
Nigerian – 419
These are very common scam emails that include sob stories, unfailingly polite language, and a promise of a big payoff.
Subject Lines: My Dearest Friend, Contact my secretary, and from the desk of.
Scam: Most offer huge payout if you help. Only problem is you need to pay a fee or “tax” to get the money. This allows scammer to take your money and identity.
Most Recent Reported Scams
 WhatsApp Scam Email
WhatsApp Scam Email
This email poses as a popular mobile phone app called “WhatsApp” claiming it has an incoming voice message for the user. Inside the email is a video message that if played will add malware to your device or bring you to a site that will add malware.
Credit Card Chip Scam Email
With new credit card chips on the rise, scammers have created an email that say you need to update your information to receive your new card. This is a method of phishing, and scammers even use the credit company’s logos. “… card companies won’t be giving you a heads-up, you’ll simply get your new card in the mail…”
How to recognize that an email is a scam?
- Sounds too good to be true
- Include words like easy, free, fast, and quick
- All capital letters
- Sounds urgent
- Uses misspelled words or slang
Sender
- Email account name does not match sender name.
 Example:
Example:
From: Meijer (ShopForMore@mymeijer.com) – The name of sender and email account match well enough to show some trust from the sender
Example:
From: Allied & NAVL (79JN@kipwring.com) – Most businesses have their business name after @ and before .com and start with either info, support, and noreply.
Body of Email
- Information is extremely vague – Especially when pertaining to subject lines about account expiration or upgrade, is a tactic to get you to click on link because of your confusion. This is also common in the ‘get rich quick scams’ and ‘lose weight fast’ using you curiosity to their advantage.
- Image is only thing in body – A real email will try to use a good mix of images and text.
- Plain text is only thing in body – Once again a real email will try to use a good mix of images and text.
How to avoid these scam emails?
 Install/Update Antivirus Software – This will help block any email-born viruses
Install/Update Antivirus Software – This will help block any email-born viruses
- Android Antivirus Apps
- iOS Antivirus Apps
- Desktop Antivirus
Install/Update Personal Firewall – This will also help block any email-born viruses
Setup Email Spam Filtering – A lot of emails offer spam filtering which does a fairly good job. This is not 100% effective though so do not rely on spam filtering.
 Setup Email Security – A lot of emails automatically have a security set up for spam but some you may need to configure yourself. Anytime you make an account on the internet you need to always check the security and privacy options to protect yourself.
Setup Email Security – A lot of emails automatically have a security set up for spam but some you may need to configure yourself. Anytime you make an account on the internet you need to always check the security and privacy options to protect yourself.
Do Not Trust Unsoliciated Email – These are individuals or organizations that are unknown. Most likely they are not a trustworthy sender.
Tip: Anything of real importance will contact you by phone or mail. Anything federal/Government related will only contact you by mail.
Be Cautious About Attachments – This is a very easy way to download malware onto your device. To be safe, only open attachments from trusted senders.
 Do Not Click Links – This is another easy way to download malware onto your device. Even though the link name may look familiar, mimicking a real business, it does not mean it is real.
Do Not Click Links – This is another easy way to download malware onto your device. Even though the link name may look familiar, mimicking a real business, it does not mean it is real.
Click link to see an example: https://www.youtube.com – Looks like a real link to YouTube but it didn’t take you to YouTube
Tip: Not sure if a link is safe? Type it into your browser instead of clicking on the link.
If you have been a victim of fraud email
- Run a antivirus scan
- Contact Credit Agency – You can place an alert with any one of the three major credit bureaus signals to potential creditors that you could be a victim of identity theft.
- Update Account Logons – Change passwords on as many accounts as possible
- Report it to Action Fraud
- Fill a complaint at the Federal Bureau of Investigation Internet Crime Complaint Center and review recent press releases
- File a report with the Federal Trade Commission
[stylebox color=”gray” bgcolor=”#7ad0ff” textcolor=”#000000″]
TIPS:
- IRS and court appearances will never contact you by email. They will most likely use paper mail.
- Type links into your browser instead of clicking on the link. This will prevent a redirected link.
- Do not open attachments unless from a trusted sender.
- If it is free or too good to be true then do not trust it.
- Before you donate to charity, research the company to make sure it is real. Use the Guidestar Nonprofit Directory to search for registered charities.
- Do not send money to people you do not know.
- If the subject line says urgent it’s most likely a scam.
- If buying any items, use scamAdviser to check website trust ratings.
[/stylebox]
Google Event. The Good and The Bad.
Google held their press event on Tuesday, September 19th in San Francisco announcing many new products such as the Nexus 6P and 5X, the new Chromecast 2, Chromecast Audio, and the Pixel C. They also announced their new Operating System.
 Nexus 6P
Nexus 6P
This was the most anticipated product coming out of Google and is considered the “flagship”. While there are a lot of great features in this new phone some have found minor complaints about the Nexus 6P
5.7 Inches
1440 Resolution
Metal Exterior
Gorilla Glass 4
7.3mm Thick
Snapdragon 810 Processor
Complaint: Users disappointed in this version of Snapdragon
Android 6.0 Marshmallow Operating System
3GB RAM
Complaint: Future is looking at 4GB and some worry this will not be enough RAM
Project Fi (WIFI) Availability
Updated Camera – 8 Megapixel front-facing and 12.3 Megapixel Back facing (4K video and slow-motion shots)
Complaint: There is a camera bump (similar to the iPhone bump) and an “ugly” black bar
Complaint: Does not have optical image stabilization (OIS)
2 Front Facing Speakers
Nexus Imprint – Fingerprint sensor. Used to easily unlock phone and can be used to authorize payments on android pay or the play store.
Larger Battery
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Complaint: Future is leaning towards the wireless charging. Users disappointed that was not incorporated.
Colors – Frost White, Aluminum, and graphite
Cost – $499
 Nexus 5X
Nexus 5X
The Nexus 5X is considered the affordable alternative to the Nexus 6P over $100 cheaper. Even that being said it still has a lot of great features but the biggest worry it is not worth the update from their current phone. (ibtimes)
5.2 Inches
1080 Resolution
Gorilla Glass 3
Equipped with Android Marshmallow
Project Fi (Wireless Network) availability
Bigger battery
Nexus Imprint – Fingerprint sensor. Used to easily unlock phone and can be used to authorize payments on android pay or the play store.
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Complaint: Future is leaning towards the wireless charging. Users disappointed that was not incorporated.
Snapdragon 808 processor – Many like this processor better than Nexus 6P’s Snapdragon 810
12-megapixel camera (4k video)
Cost – $379
Chromecast 2
Chromecast has gotten some updates but luckily the price did not change. A new look along with better Wifi are only a few update. Some features are still yet to come in the next year.
Wifi Updates – Supports 5GHz Wi-Fi and has 2 antennas for better streaming
New Look – A small disc with bendable HDMI arm
Colors – red, yellow, and black
Cost – $35 (no change)
 Chromecast App Update – Universal voice search tool – “fast Play” videos google thinks you want to watch – “what’s On” popular content (youtube and Netflix) – adding new apps, showtime, sling TV, NBA, and NHL and Spotify
Chromecast App Update – Universal voice search tool – “fast Play” videos google thinks you want to watch – “what’s On” popular content (youtube and Netflix) – adding new apps, showtime, sling TV, NBA, and NHL and Spotify
Only Complaint: Does not support 4k TVs
Chromecast Audio
Google announced a brand new product called Chromecast Audio. A neat way to put life back into your old speakers. You can connect and send music. Many were happy to here Chromecast now supports Spotify. With it’s cute look it seems to be a hit.
Plugs Into Speaker – 3.5mm audio port
OS Support – iOS/Android/Chrome
Supports RCA or optical outputs
Connect and Send Music – Using google play, Pandora, NPR one, Rdio, and Spotify (controlled by phone lock screen and android smartwatch or android and chrome tab)
Cool Look -Looks like a mini vinyl record
Cost – $35
Complaint: Users are concerned with compatibility with speakers.
 Pixel C
Pixel C
Top feature of the tablet Pixel C is that fact it is light but solid. The keyboard connects well and feels stable. While there is not a release date Google promises it will be out by the holidays.
10.2 Inch Tablet
Detachable Keyboard
USB Type-C port charging – “can charge the device twice as quickly as an iPhone 6 Plus” – The Verge
Complaint: Need to buy new cord.
Nvidia X1 Processor
Complaint: Users likes Intel Processor and not sure why they switched.
3GB of RAM
Android Marshmallow
Complaint: Users want the Chrome OS. Using a mobile OS limits some of the things that can be done on the tablet.
Cost – $499
Keyboard cost – $149
Complaint: Enter and delete key take time to getting used to placement.
Complaint: No touch pad. Sometimes the touchscreen is not optimal e.i. word documents.
 Android 6.0 Marshmallow
Android 6.0 Marshmallow
Android’s new ‘M’ operating system is the 6.0 Marshmallow. It comes with some desirable improvements.
Notifications – More consistent
Improves Battery Life
Fine-Grained Privacy Controls
Now on Tap – Google searches and voice interaction in individual apps
Doze – Power-saving mode – shuts down processes when hasn’t been moving or used
Not released to enough phones to have any known complaints
Devices to get Android Marshmallow:
End of 2015 – HTC One M9, One M8
Early 2016 – HTC M9+, HTC E9, HTCME, HTC E8, HTC M8 EYE, HTC Butterfly 3, HTC Desire 826, HTC Desire 820, HTC Desire 815
Samsung has yet to say except their new devices will not be launching with it. – techRepublic
Protect Your Smartphone From Malware
With the recent scares about Android’s ‘StageFright 2.0’ bug, that you get by opening a MP3 or MP4 file, it might get your wondering more about whether you have or had a bug on your phone. Different malware includes adware, bug, spyware, Trojan horse, virus, and many more (Learn more about Malware types ) There are some signs that your phone is being attacked and many ways to prevent your smartphone from getting malware. Already have a virus? There are ways to get your phone back in your control.
Has your phone been bugged? Here are some signs your phone is being tapped into:
- Difficulty Shutting Down – You may experience a delay in shutting down your phone. Often you will notice the back-light is still on even after it’s shut off.
- Odd Activity – This can consist of distortions on your screen or even application being installed by itself.
 Call Interference – During phone calls there may be unexplained background noises, clicks, echoes, or static.
Call Interference – During phone calls there may be unexplained background noises, clicks, echoes, or static.- Data Use Increase – Drastic increases in data without a good explanation. Not sure how to tell… “Look at how much data your device is using, and see if there’s a big discrepancy between how much data you’re using, and how much your applications are using. Any difference involving 10MB or more might be a sign of ‘parasitic activity’” – DarkReading
- Low Battery and High Temperatures – Both paired together could be caused by a constantly running application tapping into your phone.
- Coded Text Messages – This is a strong sign your phone has been tapped
The 2015 Internet Security Threat Report from Symantec showed that data breaches surged by 23 percent last year, and nearly a million new pieces of malware (“malicious software”) were created per day. Almost 1 in 5 Android apps available last year were actually malware in disguise, says the same report. The more popular smartphones and downloading apps become, the more popular malware and other viruses are becoming as well. Be smart and keep your smartphone safe from these bugs.
How do you prevent your phone from getting infected?
Strong Lockscreens – The stronger your passcode to get your phone unlocked the more secure your phone is.
- Not sure how to set up a lockscreen…

- Android Lockscreen Setup
- iPhone Lockscreen Setup
- Top lockscreen apps…
Get A Security Program – Ultimately the best ones would include anti-virus, anti-malware, anti-spam, anti-phishing defense, and a firewall.
- Android Antivirus Apps
- iOS Antivirus Apps
Update Your OS – There is a reason they come out with updates and new operating systems. The longer you put off updating your phone, the more susceptible it is.
Use Trustworthy Companies – If you are downloading applications, ringtones, wallpapers, etc. always use trustworthy companies, take the time to read reviews too.
Avoid Suspicious Websites – If you feel suspicious there’s good reason.
- How do you tell a website is unsafe? (SpyRambly)
- Poor layout
- Bright and flashing buttons, banners, or images
- Constant pressure to download
- Manipulation used to click on unsafe links
Turn Off Bluetooth – When you are not using the Bluetooth, have it set to off
Take Out Battery – Although this make not as practical for frequent users but if you know you won’t be using your phone for a while, take out the battery.
Don’t Jailbreak – If you jailbreak your phone this leaves you much more susceptible to viruses.
Use the Two Step Verification – This is an extra security step.
- Not sure how to set it up…
- Google 2-Step Verification
- Apple 2-Step Verification
Encrypt Sensitive Information – Another extra security step to help keep you safe.
- How do you encrypt?
 TIP: Backup Your Information – No matter how hard you try to prevent it there is still a chance you will get infected. It is always a good idea to have your information backed up in case you have to wipe your phone clean.
TIP: Backup Your Information – No matter how hard you try to prevent it there is still a chance you will get infected. It is always a good idea to have your information backed up in case you have to wipe your phone clean.
- How do you backup your phone?
- Android Backups
- iPhone Backups
My phone is infected! What do I do now?
- Take out your SIM card at first sign of malware
- Restart your phone in ‘Safe Mode’
 Depending on the severity of the infection:
Depending on the severity of the infection:
- Uninstall the application or remove file/software from where the malware came from
- Reset to factory settings – you can do this on your own or take it to your provider (This is where backing your information up is important)
- Run an anti-virus scan