Top 10 Tips for How to Write With AI
Unleash the power of AI: 10 Tips to revolutionize the blog writing process and boost engagement using AI technology.Read More
11/19/2019 E-Newsletter: Your new keyboard may give you a virus… | Protect your children from adult advertising
Extremely important! Learn how to keep your computers safe from junk and viruses. Also, who gains access to your accounts after you pass away? Read this to learn how that works. More scams coming to your inbox. Don’t fall for fake debt collectors. Click here to read all this and more!Read More
Why You Need an SSL Certificate on Your Website
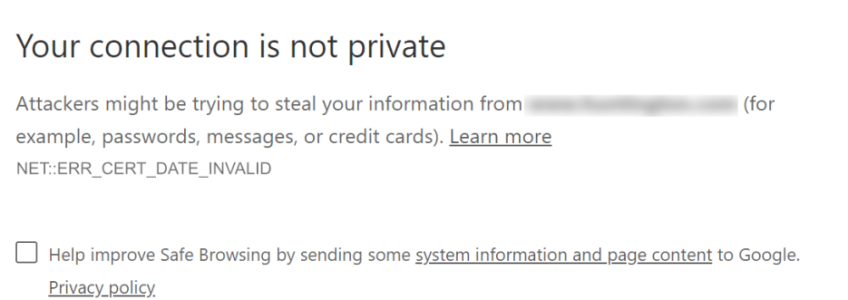
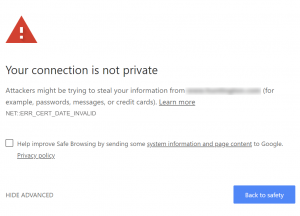 Have you ever visited a website and been greeted by a warning stating that the site is “Not Secure” or something similar? It is definitely off-putting to visitors when this happens. If you are a site owner and notice your site doing this, it is actually pretty easy to fix. All you need to do is install an SSL certificate.
Have you ever visited a website and been greeted by a warning stating that the site is “Not Secure” or something similar? It is definitely off-putting to visitors when this happens. If you are a site owner and notice your site doing this, it is actually pretty easy to fix. All you need to do is install an SSL certificate.
What is SSL?
SSL stands for “secure sockets layer”. This essential technology encrypts data as it moves between a web server and browser. In other words, it stands between you and the rest of the internet, 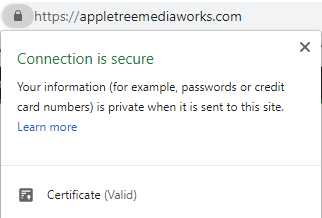 jumbling whatever information you send (such as usernames, passwords, credit card info, etc) into nonsense that can only be decrypted by a special “private key” held by the intended recipient. This protects you from hackers who could otherwise intercept your info while it is in transit. You’ll know you’re on a site with an SSL certificate if you see a padlock to the left of the URL in the address bar.
jumbling whatever information you send (such as usernames, passwords, credit card info, etc) into nonsense that can only be decrypted by a special “private key” held by the intended recipient. This protects you from hackers who could otherwise intercept your info while it is in transit. You’ll know you’re on a site with an SSL certificate if you see a padlock to the left of the URL in the address bar.
What if My Site Doesn’t Collect Personal Information?
Google encourages every site to obtain an SSL certificate. As a reward, your website gets a boost in search ranking. By not having one, you ultimately rank worse regardless of your data collection policy. If you’re running a small business, building a good Google ranking is essential to help bring in customers. This reason alone is good enough to justify the effort – you can outrank your competitors!
In addition to that, not having an SSL certificate causes some browsers to display a warning. Google Chrome, specifically, shows a “Not Secure” label (as mentioned earlier). This can be alarming to potential visitors, redirecting them away before they even land on your site. If enough visitors “bounce” because of this, it can ruin your website’s performance and eventually even harm your company’s credibility!
Keep Your Information Safe
If you manage your website using a content management system like WordPress, your administrative login credentials could become compromised if your site does not have an SSL certificate. Without it, your username and password are sent as plain text over the internet. Credentials sent this way can easily be picked up by hackers. Another way to combat unauthorized logins is by using two-step verification. Enable that whenever it is available.
Stay Cautious
Sometimes even phishing & scam websites are able to obtain legitimate SSL certificates. Just seeing a padlock in the corner does not necessarily mean you should trust the site with your personal information. Usually, you only have to worry about these types of scams coming through your email, so make sure to keep your guard up and know what to look out for.
Now that you know how important SSL certificates can be for you and your customers, help keep your website visitors safe and comfortable by installing one as soon as possible. This will boost your reputation as well as your organic search rankings over time. Not sure how to install SSL yourself? The experts here at Appletree would be happy to assist – we do this all the time! Don’t hesitate to drop us a line and let us know how we can help.
Subscribe to the free Appletree MediaWorks E-Newsletter to get bi-weekly tech tips, scam notices and more, straight to your email!
Common Email Scams to Lookout For
As technology progresses, we’re finding new ways to do things better. One downside of this is, that also means scammers are finding new ways to do things better. Here is some spam to look out for.
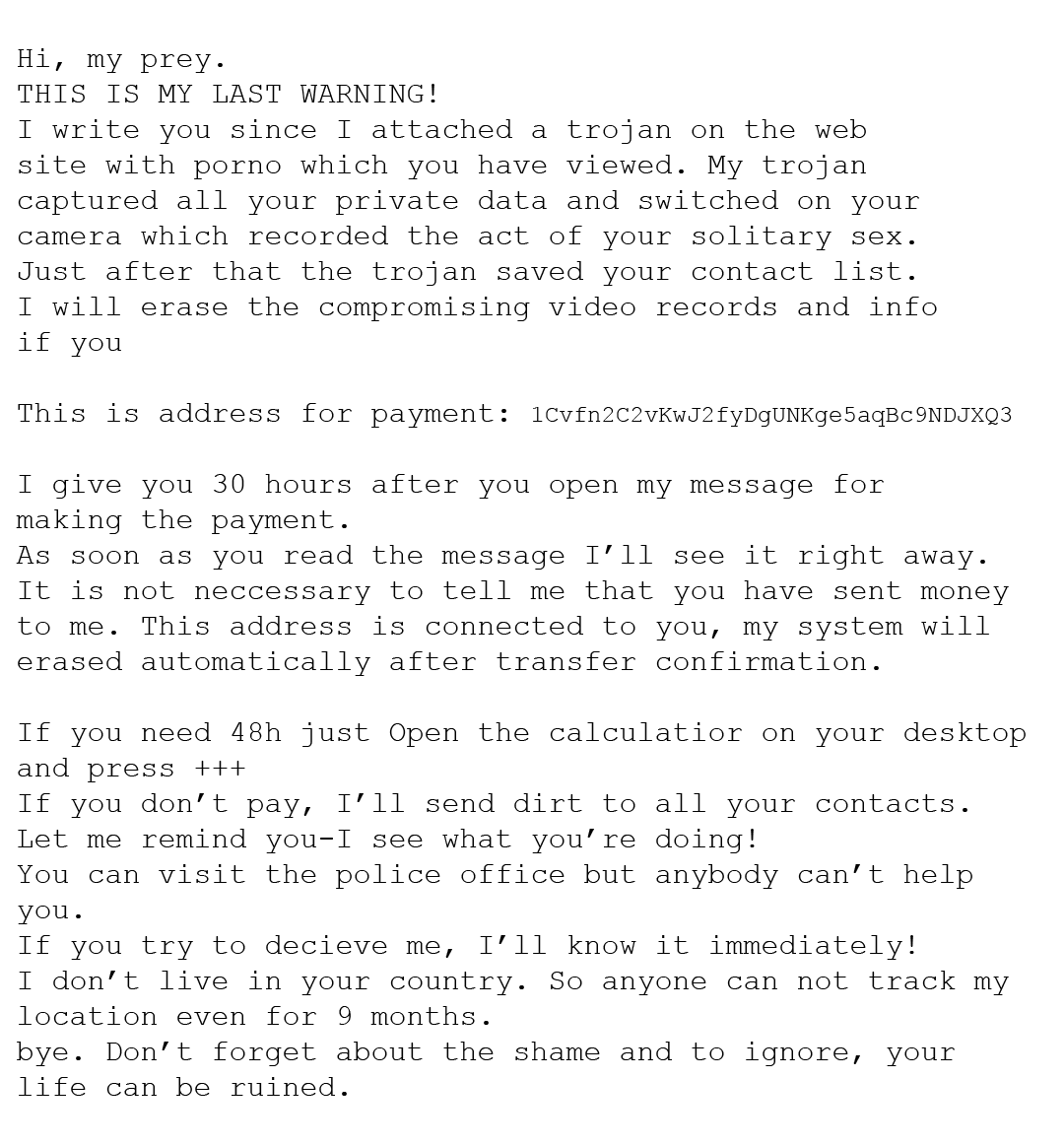
Sextortion Email Scam
One scam that was popular last year had the scammer proclaiming that an amount of money (usually ranging from $600-$3000) in Bitcoin is enough to destroy video that they supposedly have of you. The scammer sometimes even supplies a password of yours within the email. They then threaten to release webcam video of you viewing pornography to your family, friends, and colleges. At this point, you may be nervous.
Here is an example of this scam:
What should you do?
If you’re still using the password they put in the email, you should certainly change it. Do not respond to scammers ever, just report the email and delete it instead.
Various Phishing Scams
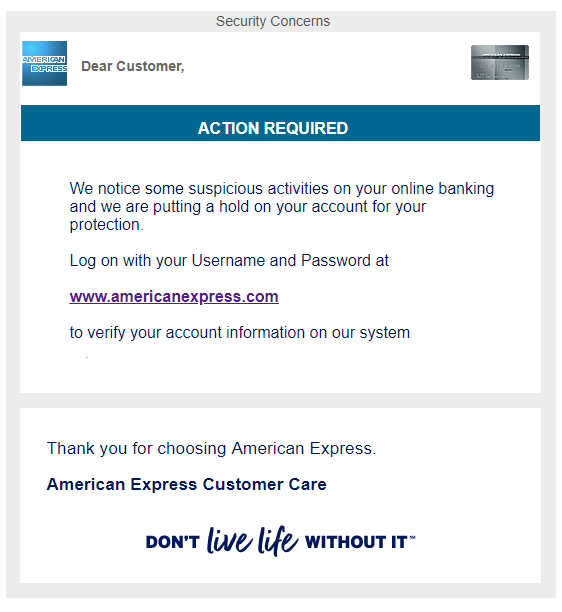
If you haven’t heard of phishing yet, you’re probably at a higher risk of falling for it.
Phishing is a “bait” scam method (hence the relation to “fishing”) where scammers will have an imitation site that strongly resembles the real thing. It takes is a split second for them to get you. From adding a malicious extension to typing in billing information to a “failed transaction” from a fake Amazon, these scammers will pretend to be pretty much anything to get your money from you.
Here is an example of phishing (extremely authentic looking):
What should you do?
If you get an email that contains an external link, don’t click it right away.
– Double check who the sender is. Sometimes this can be a giveaway. Don’t recognize the email? Doesn’t look real? Don’t click the link.
– Use a website like https://www.urlvoid.com/ and paste the link that was provided. It will tell you the destination of the link. If anything..phishy.. comes up, don’t follow through. The link given to you in the email should be the same website as the destination.
– If nothing else, it’s better to be on the safer side. Never provide any information to a link you’re at all suspicious about.
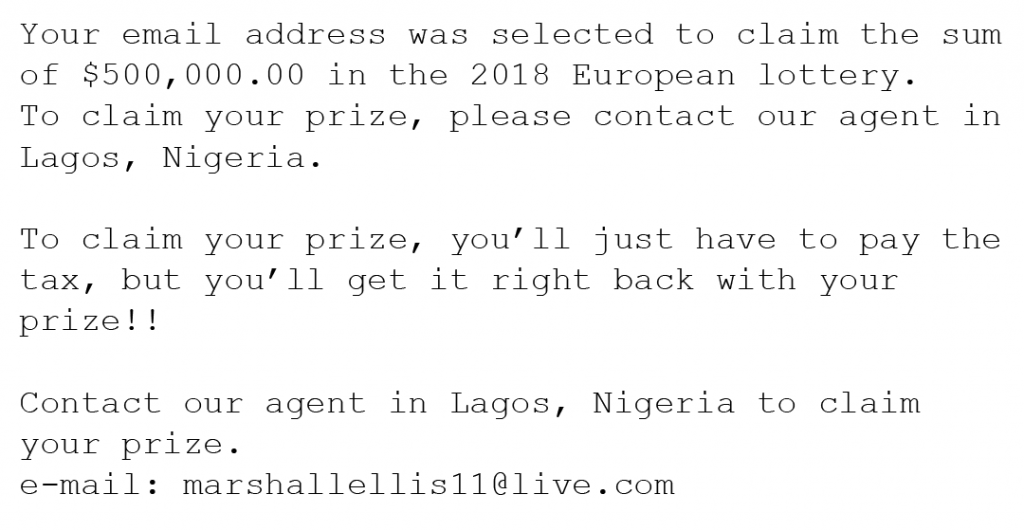
Lottery Scams
These are emails or texts from a fake lottery company saying that you won a lot of money or very valuable prizes out of nowhere. They will tell you that there are fees and/or taxes that have to be paid before your prize can be released to you.
Here is an example of a lottery scam:
What should you do?
Simply report and delete the email. Remember that you can’t win something you didn’t enter to win.
Hallmark eCard Scam
This scam would be an example of phishing, and it comes and goes pretty frequently. It’s a fake Hallmark email that is extremely real looking. If you click the link within the email to open the supposed eCard sent to you by a “friend”, a virus will launch and install malware onto your computer.
These emails will look just like Hallmark eCards.
What should you do?
Don’t click hyperlinks without knowing the destination. Attempt to verify the eCard on Hallmark’s website directly instead of clicking the link. Report and delete any unauthentic emails.
Hitman Scam
This scam would be terrifying for any victim unfamiliar with how internet scams work. Scammers here give you the option to live or die if you do not pay up. They claim a “friend” of yours gave them a lot of money to end your life, but they are giving you a chance to save it for a price ranging anywhere from $1000-$100,000.
Here is an example of the hitman scam: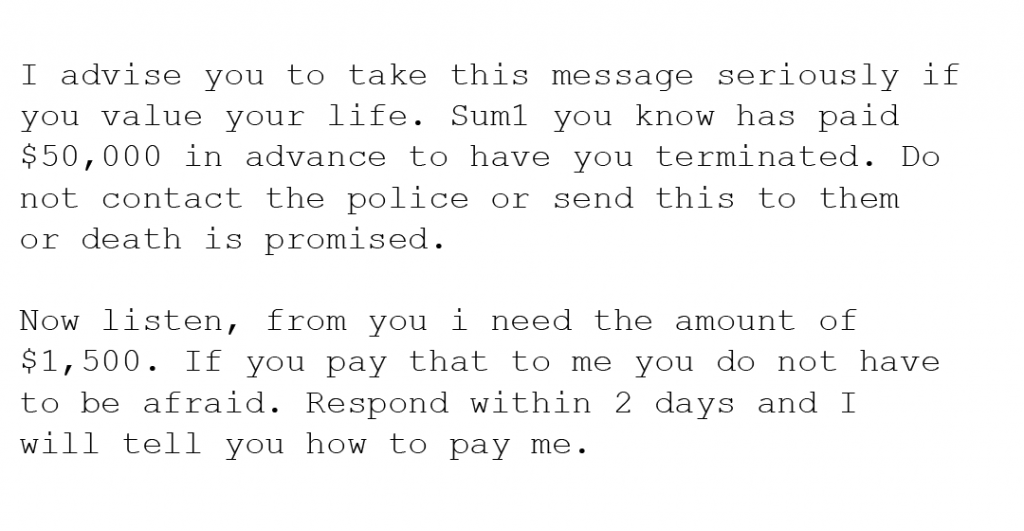
What should you do?
If you notice an email like this in your inbox, delete it without even opening it. Read below to learn where to report scams.
Protection
There are ways to keep yourself protected from scams. The most important thing is to know. Don’t believe everything that comes through your inbox and do your research.
How scammers get your information?
The scammers likely retrieved your email (and possibly an old or current password) from a database of leaked information that was obtained during a breach. To check and see if your email is associated with any data breaches, head to haveibeenpwned. You can type your email in and it will tell you if it’s ever been compromised. Also during which exact breach. Be sure to change your password if you haven’t since the last breach you were involved in.
What to do with spam
If obvious spam ever does come through your inbox, just delete it without opening it. A lot of scam emails contain what is commonly called a “pixel”. This acts as a read receipt. It will tell the scammer that the email was opened. It can also supply them with other information, such as:
- Browser you’re using
- Operating system
- IP Address
- The exact time the email was opened
Thankfully for us, there is a program that can tell us whether or not an email is being tracked. It’s called Ugly Email. It makes an eyeball appear next to the subject of any email that is being tracked. The slight downsides of this are that it’s only for Gmail and is only out for Chrome and Firefox at the moment. If you fall under the criteria, this can be a really useful tool.
Report Scams
You can help eliminate a popular scam by not only reporting it to your email provider, but to the IC3 as well. They are a branch of the FBI that deals with internet crime. Make sure to file a complaint for scams you may get – especially reappearing ones.
How to Avoid Getting Your Email Hacked
How Do You Avoid Getting Your Email Hacked?
- Duplicating usernames and passwords is risky. If you use the same username or password on several different websites, only one of those sites being compromised can make all of your accounts vulnerable. Many hackers use brute force or dictionary attacks in which a program is set up to attempt countless password combinations rapidly. The simpler your password, the easier it will be to “guess” by the program.
- Suggestions: Set up unique login credentials on each website or service you use, making sure to create complex passwords. To remember all of them, use a program or service such as 1Password, LastPass, or KeePass to help manage and keep track of your information. Once you’re set up with a password manager, creating 40-character passwords (and never forgetting them) becomes a breeze!
- Keep your software up to date. Out of date software is risky, especially when it comes to web browsers, browser plugins, and other web-based software. Make sure to keep your operating system and antivirus software up to date. Run anti-spyware programs regularly.
- Suggestions: Many programs update automatically. Still, it is a good idea to set your phone or calendar to remind you to check on these things every few weeks.
- Pay Attention to Login Sessions. Make sure that you are the only person logging into your accounts. You can often monitor recent activity with popular online services such as Facebook and Gmail.
- Suggestions: Change your passwords if things seem fishy. Do not create obvious security questions that people can find the answers to simply by searching Facebook or other sites.
- Think Before You Click! If you receive an ambiguous or unexpected email asking you to click a link, even if it appears to come from a relative or close friend – don’t do it. Contact the person over the phone and ask whether or not they actually sent it. The same goes for attachments.
- Suggestions: Ignore and delete emails like this, even if they appear to come from friends, family, or banks. Don’t click the link or open the attachment – it’s a surefire way to get your info stolen.
- Watch where you log in from. Be careful if you are logging in from a public computer or a network that is not secure. Be sure to log out of any services you used and clear the browser’s cache before walking away from any public computer.
- If Two-Step Authentication is an option, use it! Two-step authentication often requires an extra step, such as inputting a code you are texted, particularly on a new machine. If your email service has this feature, it may very well be worth the effort.
Know that none of this is absolutely foolproof as identity theft and account hacking becomes more rampant. It is best to set up your accounts so that if one gets compromised, the rest remain secure. Have a plan set up for what to do if an email gets hacked or a credit card gets stolen. Keep in mind that this is an extremely common, if problematic.
If your account gets hacked:
- Scan your computer for viruses, malware, and keystroke loggers. It is important to do this first before changing passwords, or the same problem could occur again if your computer itself has been compromised.
- Change your passwords and security questions if you can still access your account.
- If you cannot access your account, follow the directions in the site’s help center – most sites have guides about what to do.
- Report the incident. You may get access to identity protection services through the site.
- Let people know you got hacked and not to click any links appearing to come from you until the problem has been sorted out.
iCloud Hack and Compromising Data
Take a photo – it will last longer. But do you really want it to?
By now practically everyone has heard about the hacker that managed to acquire private, compromising celebrity photos and post them to distribute on websites. While all the details are still being worked out, the most common theory is that the hacker managed to get to these photos through the use of brute force software and an exploit or hack in iCloud, Apple’s iPhone cloud service.
This particular episode in questionable internet security is making news because of the enraged celebrity targets and the wildfire pace at which the images are making their rounds, but this sort of data breach could happen to anyone. And until Apple and investigators figure out and announce just what happened, users are left trying to keep things secure as possible.
What can you do to keep your data secure?
Strong Passwords
Email is inherently unsecure. Do you really need a backup of all of your emails sent up to a vulnerable cloud too? It’s likely your work email is backed up by your employer and usually personal email providers backup their own email servers, so don’t allow your email to be copied to a cloud too. If you truly need an important email for reference later? Go old school: print it out and store it in a safe or forward it to an encrypted email server for storage.
Photo Stream
Cloud storage is not inherently the most secure way to keep data, and it’s also known as a potential target for hackers. Incidentally, if you have an Apple phone or tablet, Photo Stream may be active and you might not even know it.
You can disable the Photo Stream by doing the following: Go to “Settings,” then “Storage & Backup” and stop the “Photo Stream” feature. This will stop all your photos from automatically uploading to the cloud.
Android and other phones have their own means of cloud backups to check into as well. Some require setting up manually, and others may prompt you to activate them. Read the messages you are given, and check into your settings from time to time.
2-Step Verification
Although it may not have helped in the case of the iCloud hack, 2-Step Verification increases security in devices, and many services including Apple, Twitter, and Gmail have it. 2-Step verification requires that after the user enters a password, you go through an additional step of verification (such as entering a code you are texted) on new devices.
Precautions
Without blaming the victim, keeping compromising photos off easily accessible devices warrants mentioning as well. While phones make it easy to take and send a quick snapshot, this is not inherently secure. And on the user-end, even if your own tech is secure remember that any photo you send to someone else could end up on the wilds of the internet.
If you want to take those potentially compromising photos? A camera may be a better option.
How Do You Prevent Your Email From Getting Hacked?
Duplicating Usernames and Passwords is Risky
Database vulnerability
The truth is many online databases do not encrypt your username and password at all. So one dishonest employee can have thousands of passwords in one quick database export. If one online shop gets compromised, then all of the places you use that username and password are now vulnerable. Use a different password for every website login you create and use a specialized program to store those big beautiful passwords.
Brute force attacks
Many attacks are brute force attacks in which a computer program is used to try lots of combinations of passwords rapidly. The simpler your password, the easy to ‘guess’ by the program. Again, if your password is figured out and you use the same on multiple websites, your risk is increased exponentially. Use different passwords to prevent getting your email hacked.
- Use different login credentials and complex passwords on every website you use. We featured an article on our blog featuring more information and tips about passwords.
- Just say no to browsers storing passwords! When Internet Explorer or Mozilla asks to store a password for you, ALWAYS say NO.
- To remember all your new passwords, use a service like 1Password or KeePass to create and store login information. KeePass is free!
Keep Your Software Updated
Out of date software is risky, especially web browsers and other web-based programs including browser plugins. Usually updates are released for software in response to a security hole or technology expansion. Many programs update automatically, but set your phone or calendar to remind you to check on these things every few weeks.
- Keep Windows and your antivirus software up to date.
- Run updates for your programs when they ask. If a program is asking to access your computer that you don’t recognize, choose No for now and check out Google to see what is suggested for that update name.
Pay Attention to Login Sessions
Some sites will tell you the last time you logged in successfully. Change your passwords if things seem fishy. Some programs such as Facebook and Gmail monitor your logins, other programs will let you setup verification by text messages.
- Use verification by text message, if a program asks if you’re using a public computer to login, say yes if you are.
- Do not create obvious security questions in which people can find the answers by searching Facebook or other sites.
Think Before You Click
If you receive an ambiguous or unexpected email, even from a relative or close friend telling you to click a link. Don’t do it. Contact the person over the phone and ask what the email message. Same goes for attachments. If the email does not look like something your contact would send you, QUESTION it!! Email spoofing is common too, for example there have been very real looking emails floating around that appear to be from the IRS, but the attachment is a virus.
- Ignore and delete strange emails even if they’re from friends, family, and banks. Don’t click the link or open the attachment – it’s a surefire way to get a virus.
- If you find out your account has been hacked and an email was sent from your account, first change your password. 2nd follow up with those that received your hacked email message. Tell them your email was hacked and that they should DELETE the email they received from you.
Watch Where You Login From
Be careful if you are logging in from a public computer or a network that is not secure. Do not stay logged in, when you are done with the website be sure to log out. Connecting to public WiFi can open the door to hackers.
- Be sure your computer has a strong firewall. The annoying extra click to allow something to access or update your computer is better than a hacking mess from keeping the door open.
How do you prevent your email from getting hacked? As identity theft and account hacking becomes more rampant, there is no foolproof way, but you can minimize risks by using our suggestions. It is best to set up your accounts so that if one gets compromised not all of them do. Have a plan set up on what to do if an email gets hacked or a credit card gets stolen, and know that it is extremely common, if problematic.
If You Do Get Hacked
- Change your password if you can still get in to your account.
- Follow the directions in the help center of the website you’re trying – most sites have guides on what to do.
- Scan your computer for viruses and malware, then schedule future scans to happen weekly.
- Let people know you got hacked and not to click on links, and pass along info on what to do if they did.
- Report the incident to the website. You may get access to identity protection services through the hacked site.
Extra Credit
Protecting your credit card information online goes hand in hand with your email getting hacked. We suggest using a payment service such as Paypal to store your credit card number rather than typing your credit card number directly into a website. Websites and stores are not supposed to store credit card numbers in their databases….but there are no internet police enforcing this.
Follow Appletree MediaWorks on Facebook or subscribe to our website blog RSS feed to keep up on topics like this.