How To Store Your Computer Files
File Storage Options Are Everywhere
 We aren’t chained to one computer for all our digital needs anymore: we might use a computer, a laptop, a mobile device, and a tablet that we use interchangeably.
We aren’t chained to one computer for all our digital needs anymore: we might use a computer, a laptop, a mobile device, and a tablet that we use interchangeably.
On top of that, you have the work computer and files shared with friends or family. Sometimes you might want access to a document or images from another device. This adds up to a lot of files in many places!
What if you want to move those files around? You have many options at your disposal.
Backing Up & Terms You Should Know
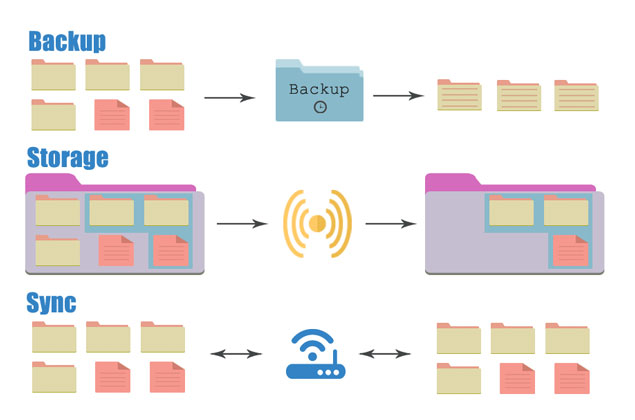
Before we go into your options, it’s important to know the difference between a backup and storage. If you have important files that you absolutely can not afford to lose, it’s important to have a comprehensive backup plan. We advocate the 3-2-1 Backup Plan: 3 copies, on 2 kinds of media, 1 of them off-site.
Backup: Backups, particularly with a backup program, are often much more comprehensive if more difficult to get to. They usually save multiple copies of a compressed file of your data.
Storage: Entails storing a given amount of data online or in a second drive. It may not be a lot of data, and it may be easy to get to again if you want to share it or access it from another device.
Sync: Synching means identical copies of your folder or device are in the second location: if you delete a file in the local folder, the file will also be deleted in the cloud or elsewhere.
Your Options for Storage
![]() External Hard Drive
External Hard Drive
It’s true that some external hard drives are large clunky bricks. Some, however, are the size of a deck of cards and easy to carry around in a bag or purse.
Pros: Lots of space. Fairly secure unless you forget it somewhere. Can be small and easy to carry.
Cons: Sometimes large and bulky. You have to remember to bring it with you. Don’t always play nice with smaller tablets and phones.
 USB Drive
USB Drive
Also known as thumb drives or flash drives, those small sticks (or cards, or tiny little plugs on a key chain) that plug into your computer or laptop, these have been used by college students for years.
Pros: Space is always increasing – a 35GB drive is easy to find and not too expensive. Small and easy to carry.
Cons: Small and easy to forget in that last computer you were using. Easy to lose or break or run through the laundry. Easy to accumulate and hard to organize. Don’t always plug into tablets or phones without a micro-USB adapter.
 NAS
NAS
Network Attached Storage is hard drive space that you reach through your own network. Some of them are small and contain one hard drive, while others are larger and more expensive, and carry the redundancy of multiple drives.
Pros: On-site. You are maintaining your own NAS and it’s right there at hand.
Cons: They tend to be expensive depending on size, with prices increasing depending on the space you need. In a perfect world you are going to want an offsite backup to go along with this.
 Optical Media: CDs, DVDs
Optical Media: CDs, DVDs
The old standbys of backup: CDs and DVDs – no doubt many of us still have a spool sitting around, ready to use.
Pros: Hard to save over. Even with rewritable discs, it takes applied effort to delete the disc’s media and then save again. CDs and DVDs are also inexpensive. Easy to move offsite and store elsewhere.
Cons: Better for one-use backups, discs also tend to degrade in time so they may not be a long term solution.
iCloud
Have an Apple device? Then you have iCloud storage ready to use, and your device is designed to play nice with Apple’s own cloud.
Pros: If you have an Apple product, you’re already set up with your own iCloud space, designed to integrate seamlessly.
Cons: Like any cloud storage, you need some kind of wireless internet access to use the cloud. And Apple’s iCloud hack some months back may leave a bad taste as the security of the system was compromised.
 Dropbox
Dropbox
Dropbox is one of the earlier forms of cloud storage/ synching and many people use it to share files with others for work or otherwise.
Pros: Many people already use it. Easy to use: you have a folder on your computer that syncs with the cloud and other machines. Good if you have multiple machines.
Cons: Too easy to use: sometimes it is easy to delete things, or sync excessively large files to all devices, taking up space.
 Google Drive
Google Drive
Google Drive started as a collection of online office tools called Google Docs. The word processing and spreadsheet tools have involved and they now include Google Drive itself, which starts at 15GB of space that you share with your Google account.
Pros: Comes with word processing tools and plays well with the other various Google products.
Cons: Not as internally organized as it could be, especially if you started using it as Google Docs.
 OneDrive
OneDrive
OneDrive is Microsoft’s answer to cloud storage. It comes already integrated with Windows 8, so long as you sign up for an account, which makes it easy to use if you are a Windows 8 person.
Pros: Easy to use with Windows 8 since it’s integrated right in. Tends to give various ways to hand out more free space.
Cons: While apps exist to let it work with other devices, it’s made for Windows 8 – if you have a scattering of other kinds of devices it may lose its appeal.
The best file storage solution is customized to your uses. If you feel more comfortable with a physical drive and no cloud use, a USB or small external hard drive may be the best way to go. However, if you have fully embraced the cloud and are less worried about security, utilizing the cloud that plays nice with your devices is likely the most appealing solution. Just remember to back up, and you’ll be all set to go.
iCloud Hack and Compromising Data
Take a photo – it will last longer. But do you really want it to?
By now practically everyone has heard about the hacker that managed to acquire private, compromising celebrity photos and post them to distribute on websites. While all the details are still being worked out, the most common theory is that the hacker managed to get to these photos through the use of brute force software and an exploit or hack in iCloud, Apple’s iPhone cloud service.
This particular episode in questionable internet security is making news because of the enraged celebrity targets and the wildfire pace at which the images are making their rounds, but this sort of data breach could happen to anyone. And until Apple and investigators figure out and announce just what happened, users are left trying to keep things secure as possible.
What can you do to keep your data secure?
Strong Passwords
Email is inherently unsecure. Do you really need a backup of all of your emails sent up to a vulnerable cloud too? It’s likely your work email is backed up by your employer and usually personal email providers backup their own email servers, so don’t allow your email to be copied to a cloud too. If you truly need an important email for reference later? Go old school: print it out and store it in a safe or forward it to an encrypted email server for storage.
Photo Stream
Cloud storage is not inherently the most secure way to keep data, and it’s also known as a potential target for hackers. Incidentally, if you have an Apple phone or tablet, Photo Stream may be active and you might not even know it.
You can disable the Photo Stream by doing the following: Go to “Settings,” then “Storage & Backup” and stop the “Photo Stream” feature. This will stop all your photos from automatically uploading to the cloud.
Android and other phones have their own means of cloud backups to check into as well. Some require setting up manually, and others may prompt you to activate them. Read the messages you are given, and check into your settings from time to time.
2-Step Verification
Although it may not have helped in the case of the iCloud hack, 2-Step Verification increases security in devices, and many services including Apple, Twitter, and Gmail have it. 2-Step verification requires that after the user enters a password, you go through an additional step of verification (such as entering a code you are texted) on new devices.
Precautions
Without blaming the victim, keeping compromising photos off easily accessible devices warrants mentioning as well. While phones make it easy to take and send a quick snapshot, this is not inherently secure. And on the user-end, even if your own tech is secure remember that any photo you send to someone else could end up on the wilds of the internet.
If you want to take those potentially compromising photos? A camera may be a better option.




